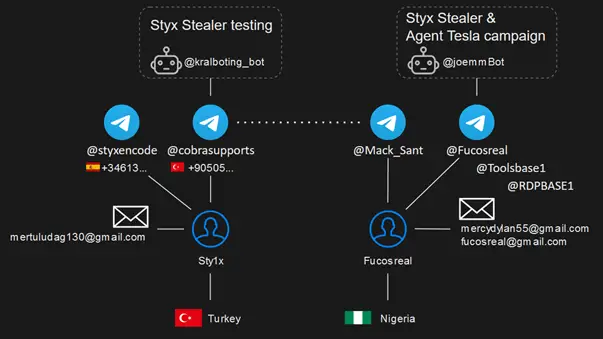
Accounts and nicknames of the Styx Stealer developer and the Agent Tesla threat actor | Image: CPR
Recently, Check Point Research (CPR) discovered a new malware variant, Styx Stealer. Derived from the notorious Phemedrone Stealer, Styx was being sold via subscription with advanced capabilities such as a persistence mechanism, a clipboard monitor, a crypto-clipper, and additional evasion techniques.
However, the malware’s developer, known as Sty1x, made a critical operational security mistake. During the malware’s development and testing, sensitive information, including Telegram bot tokens and chat IDs, was leaked from his computer.
Styx Stealer is the latest offspring of the infamous Phemedrone Stealer, a tool that exploited the CVE-2023-36025 vulnerability in Microsoft Windows Defender SmartScreen. While Styx Stealer inherits many of Phemedrone’s core capabilities, such as stealing saved passwords, cookies, and cryptocurrency wallet data, it goes several steps further. The new variant introduces a persistence mechanism, a clipboard monitor and crypto-clipper, and enhanced anti-analysis techniques.
The crypto-clipper feature is particularly dangerous, enabling Styx Stealer to intercept cryptocurrency transactions by replacing the intended wallet address with the attacker’s address, all while the transaction is in progress. This functionality, combined with its persistence on the victim’s system, makes Styx Stealer a formidable threat, especially for those dealing with digital currencies.
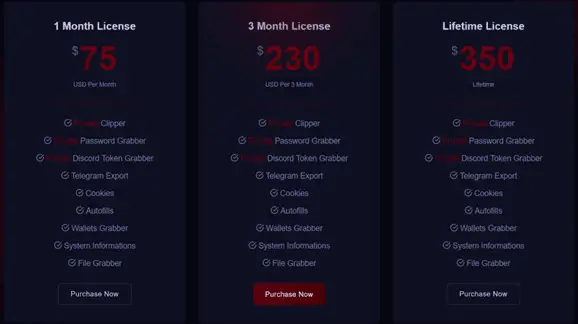
Unlike its predecessor, which was open-source and free, Styx Stealer is sold via a subscription model. Prices range from $75 per month to $350 for a lifetime license, with payments facilitated through the Telegram account @Styxencode.
During their analysis, CPR extracted a Telegram Bot token from the malware, leading them to a Telegram bot operated by a user identified as Fucosreal. It was through this bot that CPR stumbled upon a document labeled as “Styx Stealer,” complete with a screenshot of the Visual Studio IDE showing the project “PhemedroneStealer.” This revelation indicated that the document had leaked from Sty1x’s own computer.
From this single mistake, CPR was able to uncover a wealth of information about Sty1x. They identified two of his Telegram accounts (@styxencode and @cobrasupports), his email addresses, phone numbers, and even his approximate location in Turkey. Further analysis revealed Sty1x’s interactions with other cybercriminals, including Fucosreal, shedding light on their activities and connections.
The investigation into Styx Stealer and its developer did not stop at identifying Sty1x. By monitoring Telegram activity and decrypting intercepted data, CPR was able to link Styx Stealer’s development to the ongoing Agent Tesla campaign. On March 26, 2024, Fucosreal launched a spam campaign using Agent Tesla malware, targeting global victims, including CPR’s clients.
The real breakthrough came on April 14, when CPR intercepted an archive containing data from a debug run of Styx Stealer on Sty1x’s computer. This archive not only revealed Sty1x’s location but also the bot token for a second Telegram bot (@kralboting_bot). With this information, CPR intensified their monitoring, eventually capturing another data archive from Fucosreal’s PC, which exposed his location in Nigeria and further identifying information.
The investigation culminated on April 17, when Fucosreal launched another spam campaign using a Styx Stealer sample. Fortunately, this campaign failed to affect any real victims, thanks to CPR’s timely intervention.