takeover: Sub-Domain TakeOver Vulnerability Scanner
TakeOver
Sub-domain takeover vulnerability occurs when a sub-domain (subdomain.example.com) is pointing to a service (e.g: GitHub, AWS/S3,..) that has been removed or deleted. This allows an attacker to set up a page on the service that was being used and point their page to that sub-domain. For example, if subdomain.example.com was pointing to a GitHub page and the user decided to delete their GitHub page, an attacker can now create a GitHub page, add a CNAME file containing subdomain.example.com, and claim subdomain.example.com. For more information: here
Supported Services
‘AWS/S3’
‘BitBucket’
‘CloudFront’
‘Github’
‘Shopify’
‘Desk’
‘Fastly’
‘FeedPress’
‘Ghost’
‘Heroku’
‘Pantheon’
‘Tumbler’
‘WordPress’
‘Desk’
‘ZenDesk’
‘TeamWork’
‘Helpjuice’
‘Helpscout’
‘S3Bucket’
‘Cargo’
‘StatuPage’
‘Uservoice’
‘Surge’
‘Intercom’
‘Webflow’
‘Kajabi’
‘Thinkific’
‘Tave’
‘Wishpond’
‘Aftership’
‘Aha’
‘Tictail’
‘Brightcove’
‘Bigcartel’
‘ActiveCampaign’
‘Campaignmonitor’
‘Acquia’
‘Proposify’
‘Simplebooklet’
‘GetResponse’
‘Vend’
‘Jetbrains’
‘Unbounce’
‘Tictail’
‘Smartling’
‘Pingdom’
‘Tilda’
‘Surveygizmo’
‘Mashery’
Installation
# git clone https://github.com/m4ll0k/takeover.git
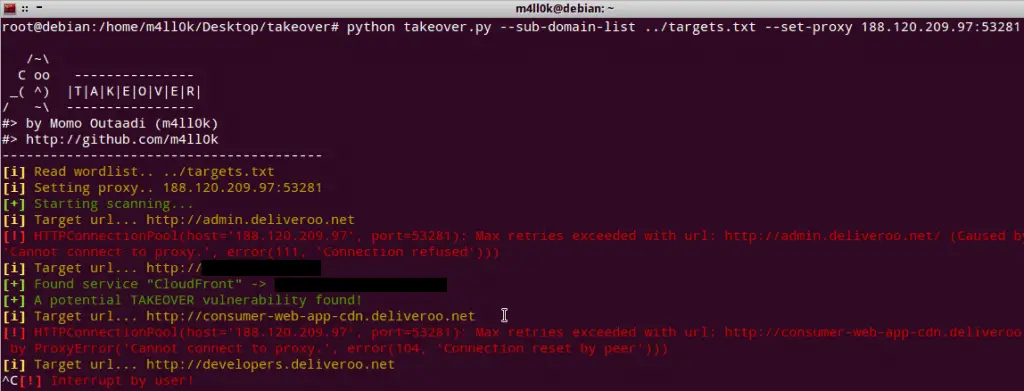
Usage

Source: https://github.com/m4ll0k/





