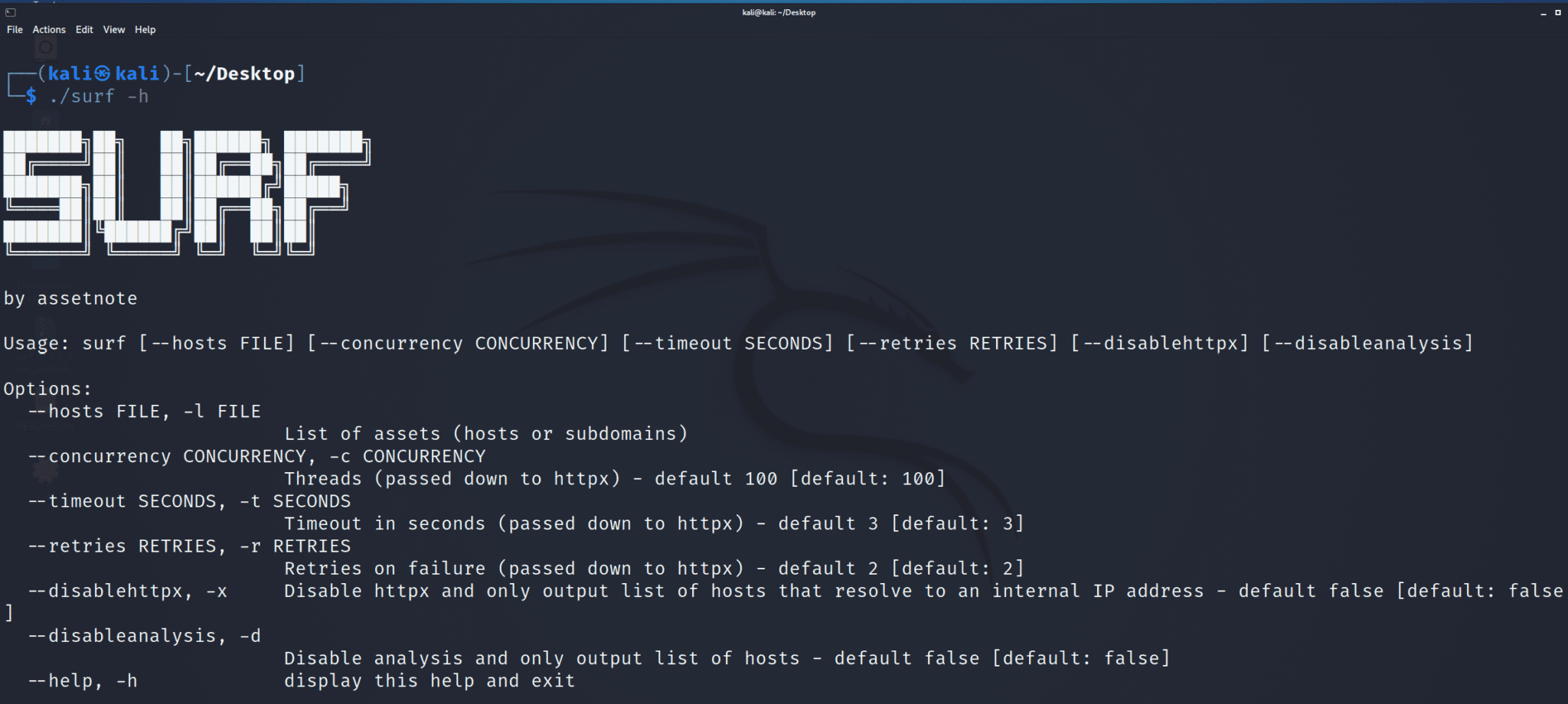
Surf – Escalate your SSRF vulnerabilities on Modern Cloud Environments
surf allows you to filter a list of hosts, returning a list of viable SSRF candidates. It does this by sending an HTTP request from your machine to each host, collecting all the hosts that did not respond, and then filtering them into a list of externally facing and internally facing hosts.
You can then attempt these hosts wherever an SSRF vulnerability may be present. Due to most SSRF filters only focusing on internal or restricted IP ranges, you’ll be pleasantly surprised when you get SSRF on an external IP that is not accessible via HTTP(s) from your machine.
Often you will find that large companies with cloud environments will have external IPs for internal web apps. Traditional SSRF filters will not capture this unless these hosts are specifically added to a blacklist (which they usually never are). This is why this technique can be so powerful.
Installation
This tool requires go 1.19 or above as we rely on httpx to do the HTTP probing.
It can be installed with the following command:
go install github.com/assetnote/surf/cmd/surf@latest
Use

Consider that you have subdomains for bigcorp.com inside a file named bigcorp.txt, and you want to find all the SSRF candidates for these subdomains. Here are some examples:
Output
When running surf, it will print out the SSRF candidates to stdout, but it will also save two files inside the folder it is run from:
- external-{timestamp}.txt – Externally resolving, but unable to send HTTP requests to from your machine
- internal-{timestamp}.txt – Internally resolving, and obviously unable to send HTTP requests from your machine
These two files will contain the list of hosts that are ideal SSRF candidates to try on your target. The external target list has higher chance of being viable than the internal list.
Source: https://github.com/assetnote/