Multi-stage infection chain
A sophisticated hacking group suspected to be the infamous CoralRaider is ramping up its attacks, using multiple well-known infostealers to target a shockingly wide range of organizations worldwide. Security researchers at Cisco Talos have uncovered a complex, ongoing campaign that hints at a dangerous escalation of cyberwarfare tactics.
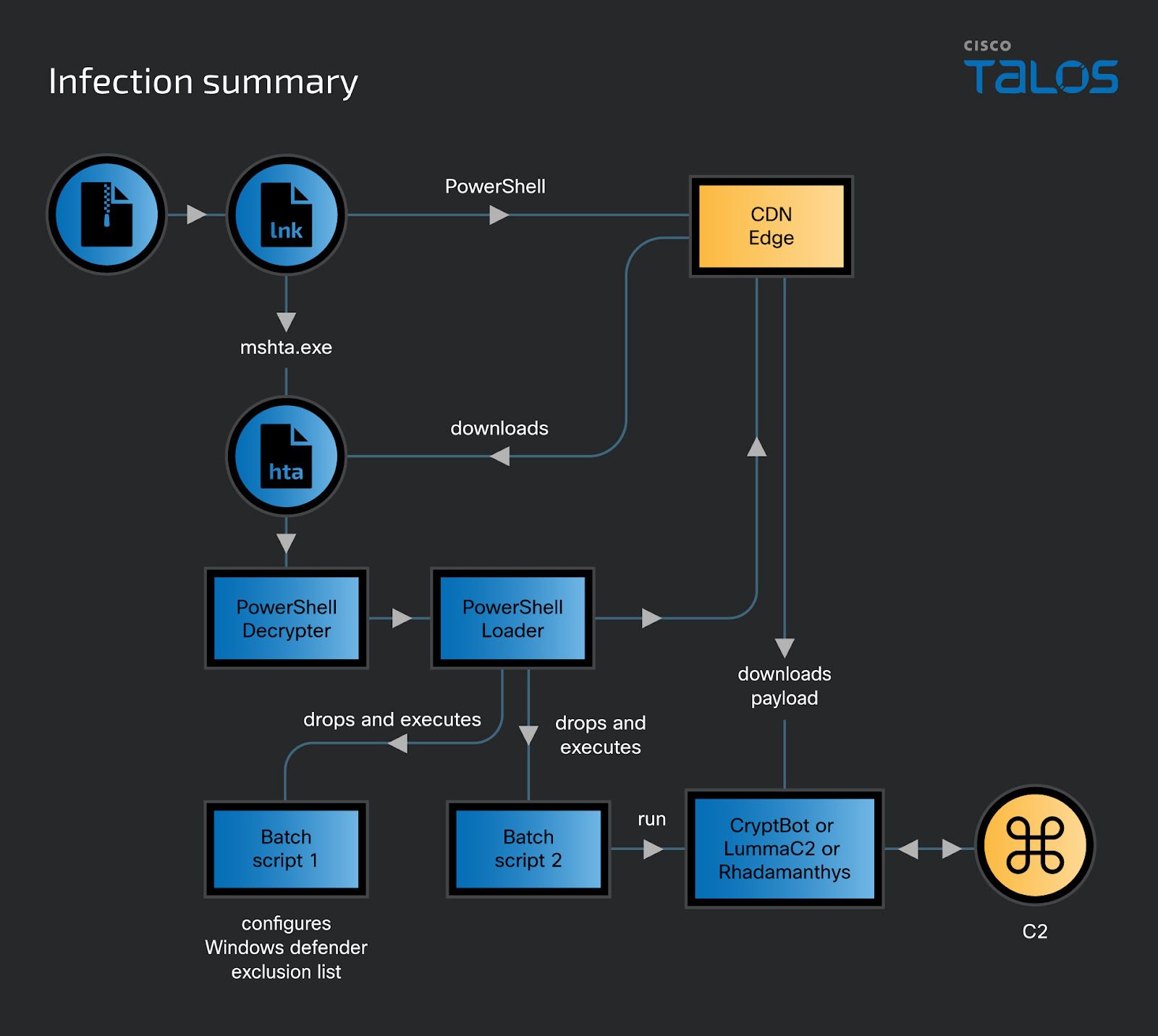
CoralRaider’s campaign leverages a series of innovative techniques to bypass antivirus defenses and successfully deploy its malware. A key tactic discovered involves a novel PowerShell command embedded within a Windows Shortcut (LNK) file. This command is crafted to evade detection tools and facilitate the download of malicious payloads onto victims’ devices.

The geographical spread of this campaign is vast, affecting individuals and organizations in countries including the U.S., Nigeria, Pakistan, Ecuador, Germany, Egypt, the U.K., Poland, the Philippines, Norway, Japan, Syria, and Turkey. Notably, victims include entities like Japan’s computer service call centers and civil defense service organizations in Syria, indicating the campaign’s widespread and indiscriminate nature.
The attack commences with the victim downloading a seemingly innocuous ZIP file that contains a malicious LNK file. Once executed, this file triggers a PowerShell command that fetches and runs a heavily obfuscated HTML application (HTA) file from a malicious server, hosted on a Content Delivery Network (CDN) to minimize latency and avoid red flags.
This HTA file contains embedded JavaScript that decodes and executes a PowerShell decryptor script. This script, in turn, decrypts further PowerShell scripts that orchestrate the downloading and execution of the payload while bypassing User Access Control (UAC) using techniques such as the FoDHelper bypass.
Unlike many campaigns that focus on a single piece of malware, this attack deploys a trio of dangerous infostealers:
- Cryptbot: A powerful infostealer known for targeting browser credentials, cryptocurrency wallets, and even two-factor authentication protected accounts.
- LummaC2: A heavily modified infostealer designed to harvest a wide range of sensitive information, including Discord credentials.
- Rhadamanthys: A rapidly evolving infostealer with powerful data-grabbing capabilities and process injection techniques.
The use of three distinct tools suggests the attackers are determined to maximize their chances of stealing valuable data, regardless of the defenses in place.
The diverse and sophisticated nature of CoralRaider’s campaign underlines a significant escalation in the threat landscape, necessitating robust defensive measures. Organizations and individuals alike are urged to enhance their cybersecurity posture by:
- Implementing advanced threat detection systems that can identify and neutralize sophisticated malware strains.
- Educating users on the risks of downloading files from unverified sources, especially files that masquerade as harmless content.
- Ensuring regular updates and patches are applied to all software to close any vulnerabilities that could be exploited.