
Fortinet’s FortiGuard Labs recently released a detailed analysis of a sophisticated cyberattack targeting the Ivanti Cloud Services Appliance (CSA). The attackers, suspected to be a nation-state actor, exploited a chain of vulnerabilities, including two zero-days, to compromise the appliance and gain a foothold in the victim’s network.
The attack, first detected on September 9, 2024, when the victim organization observed suspicious communication with a known malicious IP address, unfolded in multiple stages. FortiGuard’s incident response team meticulously analyzed the attack chain, revealing a calculated and persistent effort by the adversary.
The attackers initially exploited a previously unknown path traversal vulnerability in the /client/index.php resource, allowing them to access sensitive information like user lists. This vulnerability, combined with another undisclosed command injection flaw in the /gsb/reports.php resource, enabled the attackers to execute arbitrary commands on the CSA appliance.
As the FortiGuard report states, “The threat actor sent a malformed URL to the resource /client/index.php, by inserting %3F.php at the end of the URI, and appended the URL with the location of the php resource to be accessed through path traversal.” This clever manipulation allowed them to bypass authentication and access restricted resources.
Once inside, the attackers didn’t stop there. They leveraged CVE-2024-8190, a known command injection vulnerability in the /gsb/DateTimeTab.php resource, to escalate privileges and gain access to user credentials. Armed with this information, they further exploited the command injection vulnerability in /gsb/reports.php to establish a web shell and gain persistent access to the compromised system.
The attackers demonstrated sophisticated persistence tactics. Not only did they exploit the vulnerabilities to establish initial access, but they also worked to patch the vulnerabilities themselves, thereby locking out potential competitors from leveraging the same vulnerabilities. The report notes, “In the past, threat actors have been observed to patch vulnerabilities after having exploited them to maintain exclusive control over compromised systems.” By downloading a patched version of the vulnerable resources and overwriting the existing files, they effectively locked out any potential competitors or security researchers who might try to follow in their footsteps.
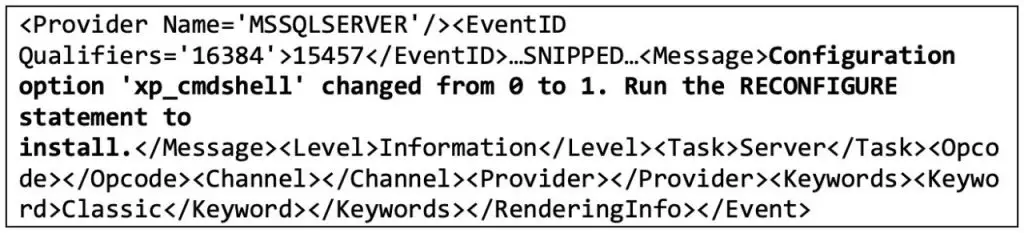
The attackers then moved laterally within the victim’s network, exploiting a SQL injection vulnerability (CVE-2024-29824) in Ivanti’s backend SQL database server. They enabled the xp_cmdshell stored procedure to gain remote code execution on the server, created a new user account, and disabled the firewall. They also conducted reconnaissance activities and attempted to exfiltrate data using DNS tunneling.
To establish even deeper persistence, the attackers attempted to deploy a rootkit on the CSA appliance. While the rootkit deployment was not entirely successful due to a corrupted archive file, the intent was clear: to maintain kernel-level access that would survive even a factory reset.
While CVE-2024-8190 had been publicly disclosed by September 10, 2024, Ivanti was only informed of the two new vulnerabilities during a meeting with FortiGuard on September 19, 2024. Ivanti subsequently issued a security advisory for CVE-2024-8963 to address the path traversal flaw.
Related Posts:
- Critical Flaw in Ivanti CSA 4.6: CVE-2024-8963 Actively Exploited, Urgent Upgrade Required
- CISA & Ivanti Warn of Active Exploitation Cloud Services Appliance Flaw CVE-2024-8190
- New Agent Tesla Spyware Variant was spread via Microsoft Word documents
- CISA Adds Three Actively Exploited Security Vulnerabilities to KEV Catalog, Urges Urgent Patching
- SideWinder APT Group Sets Sights on Ports and Maritime Facilities in Espionage Campaign