Symantec, the world’s leading provider of solutions for cybersecurity, warned in a blog post on Wednesday that a hacker group based in Iran called “Chafer” has been expanding its presence in the Middle East and List of targets in other regions and add new tools to their network of arsenals.
In 2017, the group launched a series of malicious attacks, including a major telecommunications service provider attacking the Middle East. One of the company’s main businesses is the provision of sales solutions to several telecom operators in the region, and successful intrusion will allow Chafer to monitor a large number of end users.
Symantec said Chafer has been active at least since July 2014. In December 2015, for the first time, Symantec publicly disclosed malicious attacks on the organization. Symantec said that at the time, Chafer was mainly using customized backdoors to target individuals and businesses in Iran and the Middle East (such as Afghanistan and Saudi Arabia, especially airlines and telcos).
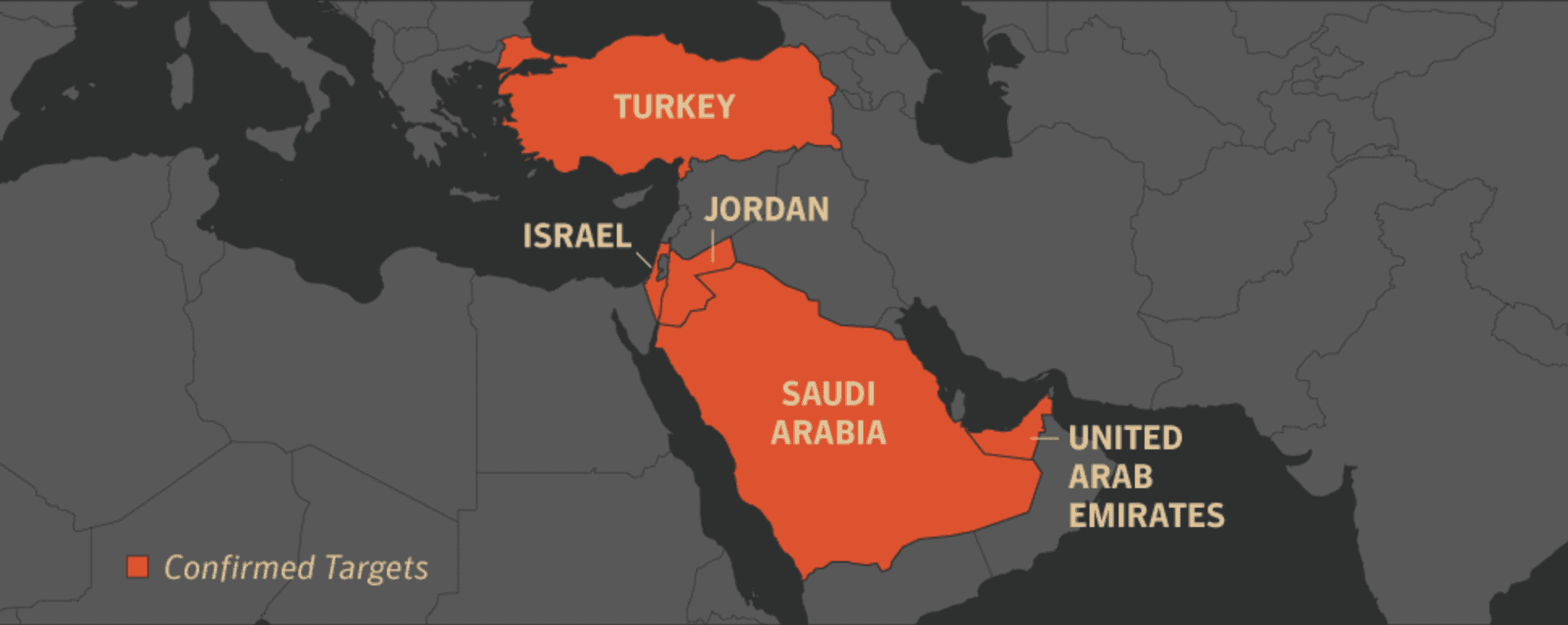
During the year 2017, the organization used seven new tools, introduced new infrastructure and created nine new divisions in Israel, Jordan, the United Arab Emirates, Saudi Arabia and Turkey. The targets include airlines, aeronautical services companies, software and IT services companies, telecommunications companies, payroll services companies, engineering consulting firms and document management software companies serving the aviation and maritime sectors.
Outside the Middle East, Symantec also uncovered evidence of Chafer’s attack on an African airline in an attempt to attack an international travel company.

From the early attacks launched in 2015, Chafer attacks enterprise Web servers mainly through SQL injection and uploads malware. And by 2017, the organization added a new method of infection to its arsenal that began to spread malware by intruding into the employee’s personal e-mail address at the target organization.
The bait file used in the attack is usually an Excel spreadsheet with a malicious VBS file that runs a PowerShell script to execute the removal program on the target computer. After a few hours, a dropper assembly appears on the target computer to install three files: an information-stealing program, a screen capture program, and an empty executable.
The screen capture app seems to be used for initial information collection since it will only be used briefly at the beginning of each infection and will not be seen again later. An information theft program can steal the contents of the clipboard, take screenshots, record keystrokes, and steal files and user credentials. After this initial activity, attackers typically use the PowerShell downloader to download additional tools to their computer and attempt to move laterally across the victim’s network to find more targets.
Back to the new tools and new infrastructure mentioned at the beginning of the article, in addition to the known malware, Chafer has started using seven new tools. Symantec also pointed out that most of these tools are provided free of charge. New tools include:
- Remcom: An open-source alternative to PsExec, which is a Microsoft Sysinternals tool used for executing processes on other systems.
- Non-sucking Service Manager (NSSM): An open-source alternative to the Windows Service Manager which can be used to install and remove services and will restart services if they crash.
- A custom screenshot and clipboard capture tool.
- SMB hacking tools: Used in conjunction with other tools to traverse target networks. These tools include the EternalBlue exploit (which was previously used by WannaCry and Petya).
- GNU HTTPTunnel: An open-source tool that can create a bidirectional HTTP tunnel on Linux computers, potentially allowing communication beyond a restrictive firewall.
- UltraVNC: An open-source remote administration tool for Microsoft Windows.
- NBTScan: A free tool for scanning IP networks for NetBIOS name information.
In addition, the organization continues to use tools such as its custom backdoors Remexi, PsExec, Mimikatz, Pwdump, and Plink.
Chafer clearly intends to use these tools to coordinate the targeted network. For example, the organization recently adopted NSSM to preserve persistence and install Plink on infected machines. Then use Plink to open the reverse SSH session from Chafer’s server to the RDP port on the victim’s computer, apparently in order to be able to use RDP to access the compromised computer. Once established, Chafer can use PsExec, Remcom and SMB hacking tools to move laterally across the victim’s network.
Chafer, on the other hand, has begun using the new infrastructure, which is embedded in the dropper assembly. Symantec discovered a large number of copies of the tools on a staging server Chafer had used, and Chafer did not even hide their activity and saved copies of the tools to the desktop without renaming them.
According to Symantec, malicious attacks by Chafer are linked to another hacker group called Crambus (aka Oilrig). This is another hacking group that is believed to have an association with Iran, mainly conducting cyber espionage.
Both seem to use the same IP address as the command and control (C&C) server address and use a similar infection vehicle, an Excel spreadsheet with malicious VBS files. Both VBS files reference the same file path and contain the same misspellings.
Recent activities by Chafer not only show that the organization is still very active, but that it has become bolder in choosing targets. Similar to other targeted hacking organizations, it follows two trends in global targeting attacks: the first is more reliance on software tools that are provided free of charge; the second is the attack on the supply chain, first Attack a goal, target the target customer after the success, and then continue to expand. This type of attack requires more “steps” to reach its ultimate goal, adding additional time and risk to the attacker’s goal. However, if successful, an attacker can gain a large number of potential goals.
Source: Symantec