
Proofpoint researchers have identified a new spearphishing campaign by TA397, a South Asia-based advanced persistent threat (APT) group also known as Bitter. The campaign, observed on November 18, 2024, targets organizations in the defense sector with highly targeted lures, employing advanced techniques to deploy malware and exfiltrate sensitive information.
The attack begins with an email sent from a compromised government account, designed to evade suspicion. The email subject, “PUBLIC INVESTMENTS PROJECTS 2025 _ MADAGASCAR,” aligns with the attached files, a compressed RAR archive containing three key elements:
- A decoy PDF detailing a legitimate World Bank initiative.
- A malicious LNK file masquerading as a PDF.
- Alternate Data Stream (ADS) files embedded within the RAR archive.
Proofpoint notes, “The usage of RAR archives is a staple tactic of TA397 payload delivery.” This method exploits Windows NTFS file system features to conceal malicious payloads, which remain invisible to users employing default Windows extraction tools.
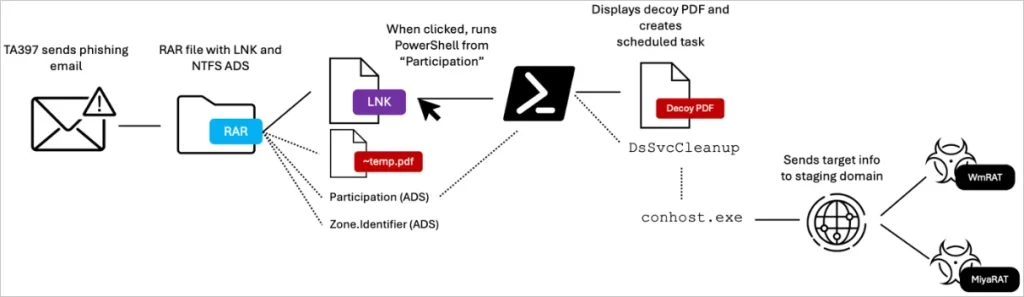
When the target interacts with the malicious LNK file, the embedded Alternate Data Stream is activated, executing base64-encoded PowerShell code. This initiates the download of additional payloads, including the well-documented WmRAT and a newer tool, MiyaRAT.
The infection chain also establishes a scheduled task, ensuring persistence and enabling regular communication with the C2 server at jacknwoods[.]com. Commands from the threat actors facilitate data exfiltration and additional payload delivery.
TA397 employs two distinct remote access trojans (RATs) in its campaigns:
- WmRAT: A legacy tool capable of gathering system data, exfiltrating files, and running arbitrary commands. WmRAT employs noise-generating techniques to hinder analysis, such as creating junk threads and redundant processes.
- MiyaRAT: A newer and more sophisticated addition to TA397’s toolkit. It employs advanced encryption methods and is reserved for high-value targets. MiyaRAT supports reverse shell capabilities, file transfers, and comprehensive directory enumeration.
The group’s staging and C2 domains reveal meticulous planning. Domains like jacknwoods[.]com serve as staging points, while academymusica[.]com and samsnewlooker[.]com are used for C2 communication. Proofpoint observed, “The infrastructure and hosting providers in use bears similarities to historical TA397 infrastructure.”
Proofpoint attributes this campaign to TA397 with high confidence, citing the group’s consistent use of scheduled tasks, RAR archives, and specific working hours (UTC+5:30). “Proofpoint assesses TA397 campaigns are almost certainly intelligence collection efforts in support of a South Asian government’s interests,” the report states.
Targets primarily include defense, energy, telecommunications, and government organizations in EMEA and APAC regions. The group’s focus on espionage underscores its intent to extract privileged information and intellectual property.
Related Posts:
- APT29’s Espionage Campaign Exploits WinRAR Flaw, Targets Embassies
- North Korean Hacking Organization Kimsuky’s Global Spearphishing Campaign Unraveled
- Hacker exploits Google App script to spread malware
- Israeli Hacker-For-Hire Gets 80 Months for Spearphishing Crimes
