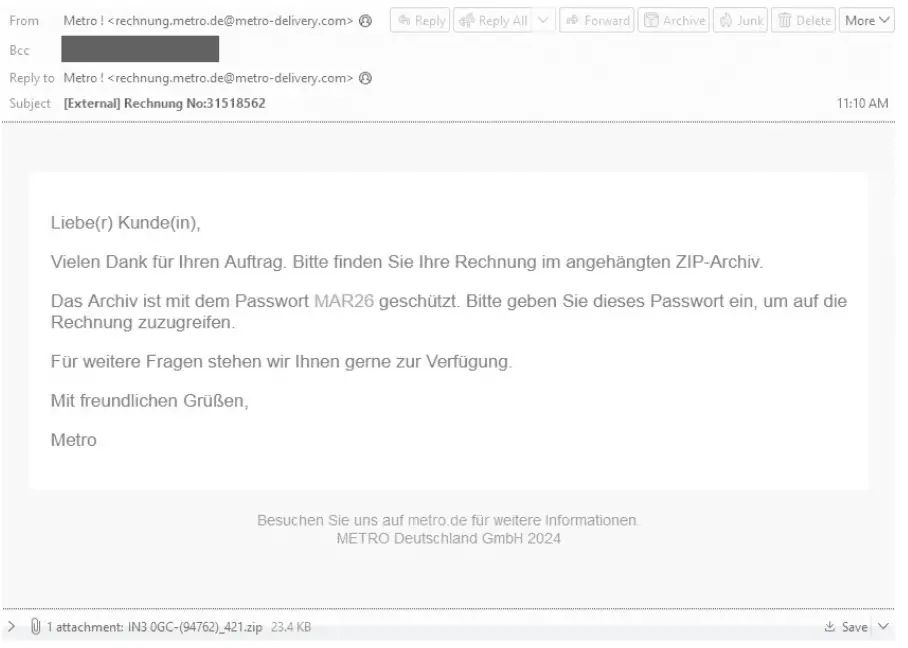
Example TA547 email impersonating the German retail company Metro
In a recent hacking campaign exposed by Proofpoint, German organizations faced a multifaceted attack. The financially motivated group TA547 deployed the Rhadamanthys information stealer for the first time, marking a shift in their usual tactics. Intriguingly, the hackers may have gotten a helping hand from an unlikely source – artificial intelligence.
The cornerstone of this campaign is the deployment of Rhadamanthys, an information-stealing malware previously unseen in TA547’s arsenal. This malware, known for its potency and the breadth of its use among cybercriminal circles, signifies a strategic pivot in TA547’s operational tactics. The threat actor’s method of delivery? An ingeniously crafted email campaign masquerading as communications from Metro, a renowned German retail giant, purportedly concerning invoices.

The emails, targeting a wide array of industries within Germany, were found to contain a password-protected ZIP file. Once opened, this file would unleash a chain reaction: an LNK file within would execute a PowerShell script, which then decoded and launched the Rhadamanthys malware directly into memory, bypassing traditional disk-based detection mechanisms.
What sets this campaign apart is the suspected use of LLMs in crafting the PowerShell script responsible for deploying Rhadamanthys. Proofpoint researchers noted the presence of unusually well-commented and grammatically correct code, a hallmark of LLM-generated content. This suggests that TA547 either directly utilized an LLM to generate the script or adapted machine-generated content from another source, marking a potentially groundbreaking shift in the landscape of cybercrime.
TA547 is no stranger to the global cybercriminal stage, having been recognized as an initial access broker with a penchant for delivering a variety of payloads, including the NetSupport RAT and other information stealers like StealC and Lumma Stealer. The group’s recent pivot to using compressed LNK files for malware delivery, observed since early March 2024, along with its expansion into geographic targets beyond Germany, underscores its adaptability and the evolving threat it poses.
This campaign not only highlights a shift in TA547’s tactics but also offers a glimpse into how cybercriminals are leveraging the advancements in artificial intelligence to enhance their attack vectors. The integration of LLM-generated content into malware campaigns represents a nuanced challenge for cybersecurity defenses. However, as Proofpoint points out, the nature of the content—whether human or machine-generated—does not alter the fundamental approach to defense. Behavioral-based detection mechanisms remain a cornerstone of identifying and neutralizing such threats, underscoring the importance of adaptive and robust cybersecurity frameworks in the face of evolving cyber threats.