Example of the new TA571 lure containing similar language to ClearFake
Proofpoint researchers have discovered a sophisticated social engineering technique that leverages clipboard manipulation to deliver malware through PowerShell scripts. This new method has been employed by threat actors such as TA571 and the ClearFake cluster, targeting users with malware including DarkGate, Matanbuchus, NetSupport, and various information stealers.
The attack begins with a seemingly innocuous prompt, instructing users to copy and paste a provided PowerShell script. Whether through malicious spam emails (malspam) or compromised websites, the method relies on users’ willingness to follow instructions to resolve a fabricated error message. The result is the execution of a malicious script that can lead to severe consequences, including remote code execution and data theft.
These campaigns exploit the legitimate use of clipboard functionality and encoded scripts in HTML to evade detection by antivirus software and EDR systems. The manual execution by victims complicates detection, as traditional security measures may not inspect clipboard content effectively. The choice between PowerShell terminal and Run dialog box presents different challenges in user interaction, with both methods designed to maximize the likelihood of execution.
ClearFake Campaign
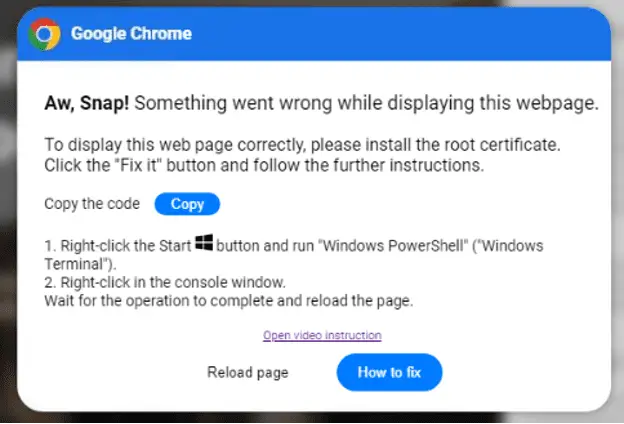
First observed in early April 2024, the ClearFake campaign involves compromising legitimate websites with malicious HTML and JavaScript. Visitors to these sites encounter an error message instructing them to install a “root certificate” by copying and pasting a PowerShell script. The campaign has evolved, using a multi-stage payload delivery system:
- Initial Infection: Users are tricked into executing a PowerShell script that performs initial tasks like flushing the DNS cache and downloading additional scripts.
- Payload Delivery: The scripts progressively load more complex payloads, including AES-encrypted scripts and ZIP files containing trojanized DLLs.
- Final Stage: The final payload includes malware such as Lumma Stealer, Amadey Loader, XMRig cryptocurrency miner, and a clipboard hijacker for cryptocurrency theft.
ClickFix Campaign
In mid-April 2024, researchers identified the ClickFix campaign, which displayed error messages on compromised sites, urging users to run PowerShell commands. Although initially semi-functional due to a taken-down payload domain, it quickly adapted, integrating ClearFake injects. This overlap suggests possible collaboration or re-compromise by ClearFake actors.
TA571 Campaign
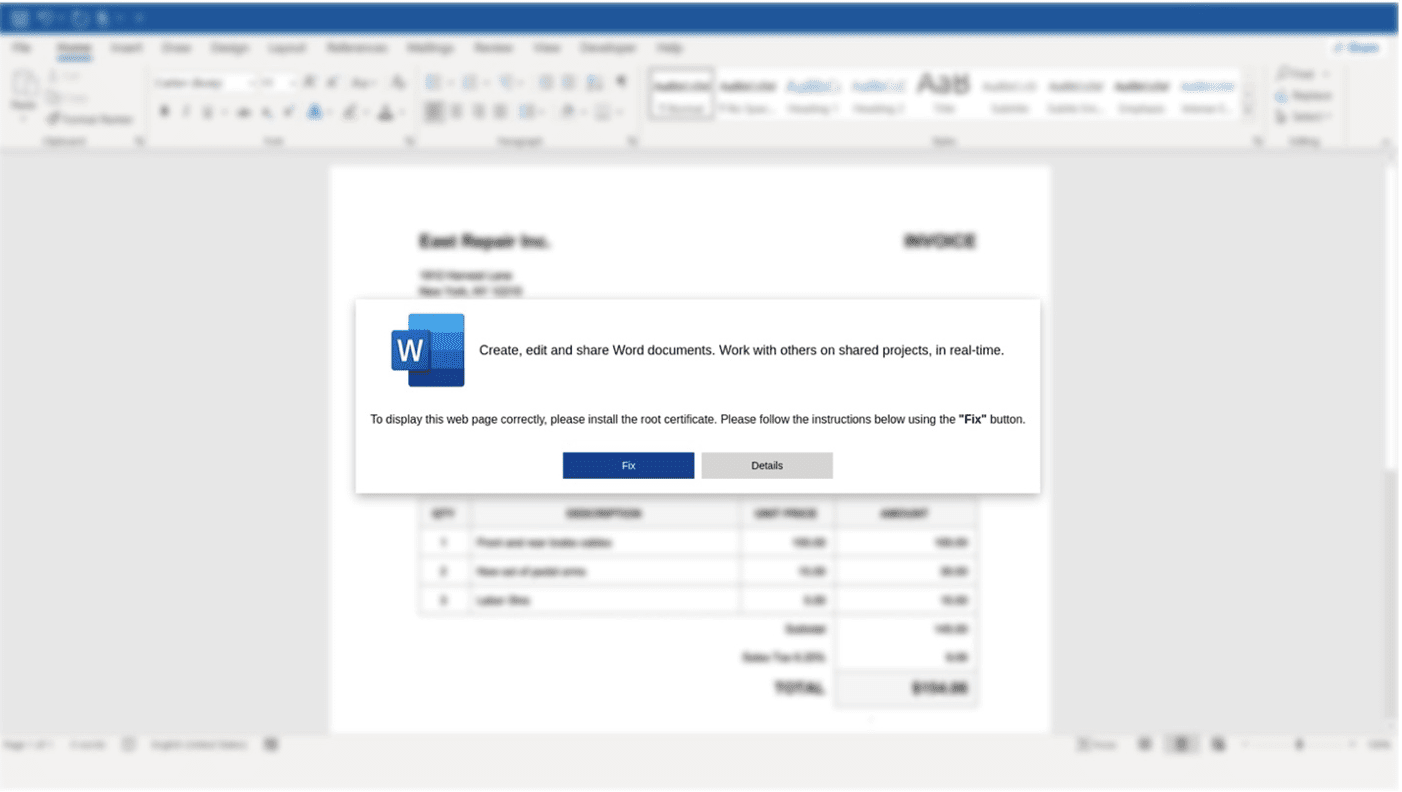
TA571, an initial access broker known for high-volume spam campaigns, began using this technique on March 1, 2024. Their campaigns typically involve HTML attachments that simulate Microsoft Word errors, prompting users to copy and execute PowerShell commands. The payloads range from DarkGate malware to Matanbuchus, utilizing different visual lures and methods, including the Run dialog box and PowerShell terminal.
TA571’s high-volume email campaigns serve various cybercriminal customers, often leading to ransomware infections. ClearFake, while not attributed to a specific threat actor, exhibits similar techniques, indicating a trend of shared strategies among cybercriminals.
The good news is that these attacks often require significant user interaction to succeed. However, their reliance on social engineering makes them particularly challenging to defend against. Organizations need to prioritize user education, teaching employees to be wary of unexpected prompts and to verify the legitimacy of instructions before executing any code.
In addition, robust security measures are essential. Organizations should deploy tools that can detect and block malicious PowerShell scripts, even when they are delivered through seemingly innocuous channels like the clipboard.