Talon v3.1 releases: perform a password guessing attack against the Kerberos and LDAPS services
Talon
Talon is a tool designed to perform automated password guessing attacks while remaining undetected. It can enumerate a list of users to identify which users are valid, using Kerberos. Talon can also perform a password guessing attack against the Kerberos and LDAPS (LDAP Secure) services. It can either use a single domain controller or multiple ones to perform these attacks, randomizing each attempt, between the domain controllers and services (LDAP or Kerberos).
More info about the techniques can be found on the following Blog
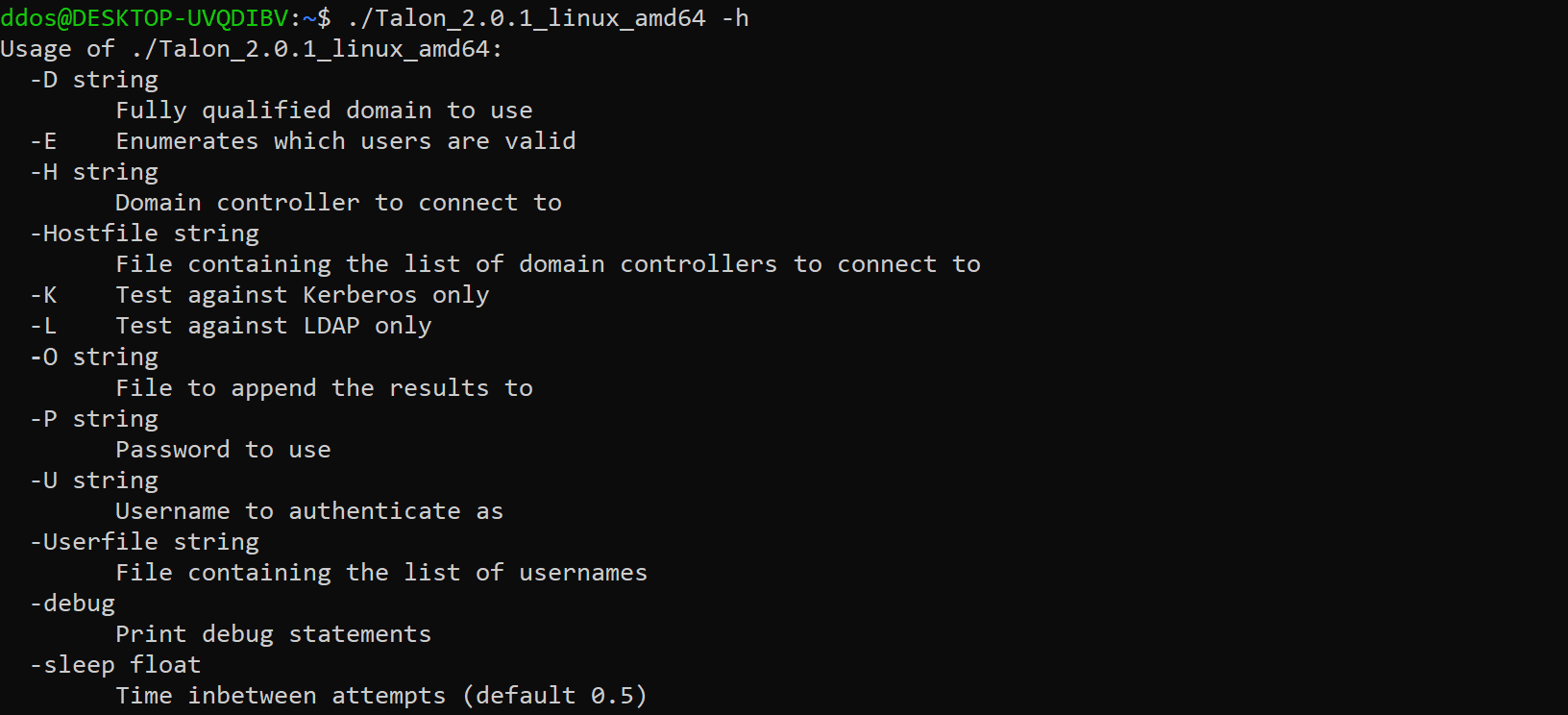
Usage
Enumeration Mode
User enumeration mode can be executed with the -E flag which will send only Kerberos TGT pre-authentication request to the target KDC, however, this request is sent with a known bad or no longer supported encryption type. Talon reviews the response by the KDC to determine if the response with a KDC_ERR_ETYPE_NOSUPP, which indicates if a user exists, or KDC_ERR_C_PRINCIPAL_UNKNOWN if it does not. It can perform this type of enumeration against multiple domain controllers in an enterprise using the -Hostfile command to specify multiple domain controllers or a single domain controller using -H. Using this technique will not cause any login failures so it will not lock out any of the users.
Automated Password Guessing Mode
Talon utilizes Kerberos and LDAP, which are both integrated into Active Directory for authentication. It can perform password guessing by alternating between the two services, allowing the password attack traffic to be split across two protocols. This splits the number of potential events generated, as a result reducing the chance of an alert. Talon takes this one step further, by distributing a password attack against multiple domain controllers in an enterprise using the -Hostfile, alternating between LDAP and Kerberos each time to create an additional layer of obscurity. A single domain controller can be provided using the -H command if needed.
Talon is designed to be versatile given any situation as a result, if only Kerberos is available, Talon can be set to only attack against Kerberos using the -K flag or the only LDAP using the -L flag.
Talon can use both Kerberos and LDAP to read the responses as we perform a password guessing attack. Talon can detect account lockouts during an active password guessing attack by reading the response code from each password attempt. This can help prevent any unwanted account locks across an enterprise, helping you to remain undetected. Simply follow the prompt to quit or continue the attack.
Changelog v3.1
New Features
- Added consecutive x failure
- Added a function to remove locked accounts while spraying multi-pass files
Bug Fixes
- Corrected logic in LockErr function
- Updated multi-password processing logic
-
- Updated location to set password, corrected logic that allowed skipped passwords by decreasing slice location if the attempts were reached
Download
Copyright (c) 2020 Optiv Security
Source: https://github.com/optiv/





