tapioca: MITM network analysis
CERT Tapioca is a utility for testing mobile or any other application using MITM techniques. CERT Tapioca development was sponsored by the United States Army Armament Research, Development, and Engineering Center (ARDEC) as well as the United States Department of Homeland Security (DHS).
Tapioca Desktop Layout
Once you have installed Tapioca, you should end up with a screen like the below. Individual icons may vary slightly across platforms.
Browse results
Open a file manager to view already-tested applications.
Terminal
Open a terminal to allow manual execution of scripts.
Web Browser
Open Chromium web browser.
Enable software WiFi AP
This button will configure a connected WiFi adapter for HOSTAP mode. This will allow you to wirelessly connect your client device to Tapioca for traffic inspection.
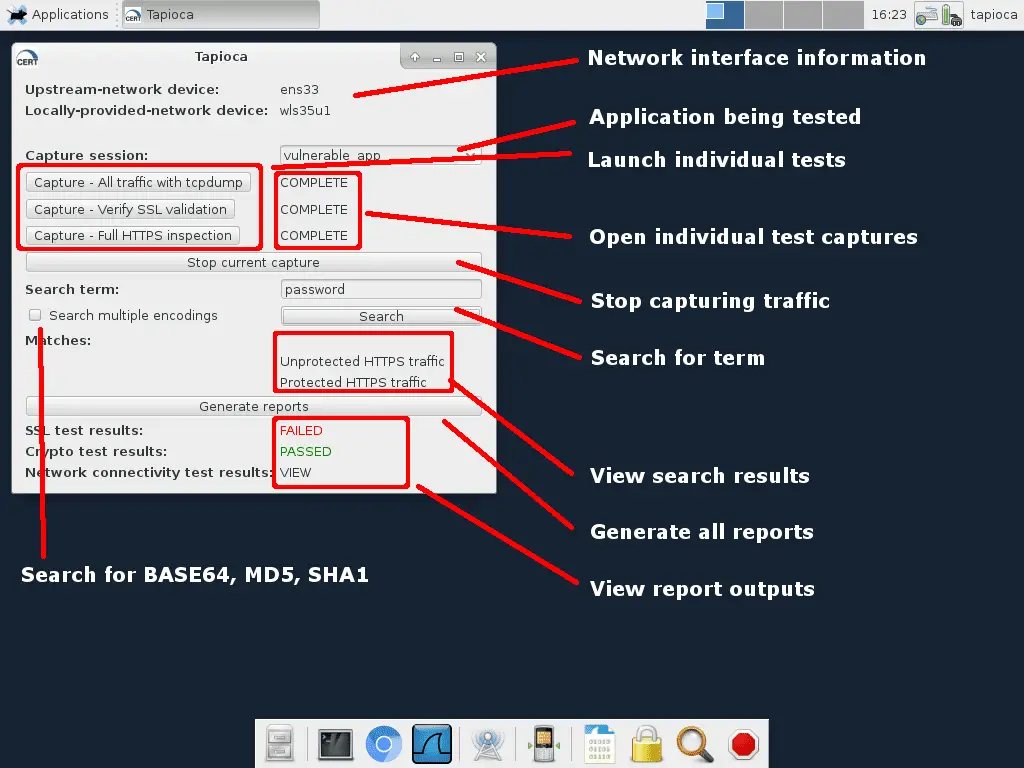
Tapioca GUI
Launch the main Tapioca interface.
Capture all traffic
Use tcpdump to capture all raw network traffic without interfering.
SSL validation
Use mitmproxy to intercept HTTP/HTTPS traffic, using an untrusted root certificate. Any HTTPS traffic that passes through is an indication of a client that isn’t validating HTTPS certificates.
Full HTTPS inspection

Use mitmproxy to intercept HTTP/HTTPS traffic, using a root certificate that has been installed on the client system. This allows full inspection of non-pinned HTTPS traffic.
Stop capture
Stop any (tcpdump, mitmproxy) capture.
Copyright 2018 Carnegie Mellon University. All Rights Reserved.