TargetCompany Ransomware Evolves: New Linux Variant Targets ESXi Environments
Trend Micro’s threat-hunting team has uncovered a new Linux variant of the TargetCompany ransomware, marking a significant escalation in the group’s tactics. Known for primarily targeting Windows systems, this evolution underscores the growing trend of ransomware attacks expanding to critical Linux environments, including VMWare ESXi, a popular platform for hosting virtualized infrastructure.
First discovered in June 2021, TargetCompany has primarily been active in Taiwan, India, Thailand, and South Korea. Over time, the group has continually refined its techniques to evade security measures. One notable method involves using PowerShell scripts to bypass the Antimalware Scan Interface (AMSI) and utilizing fully undetectable (FUD) obfuscator packers.
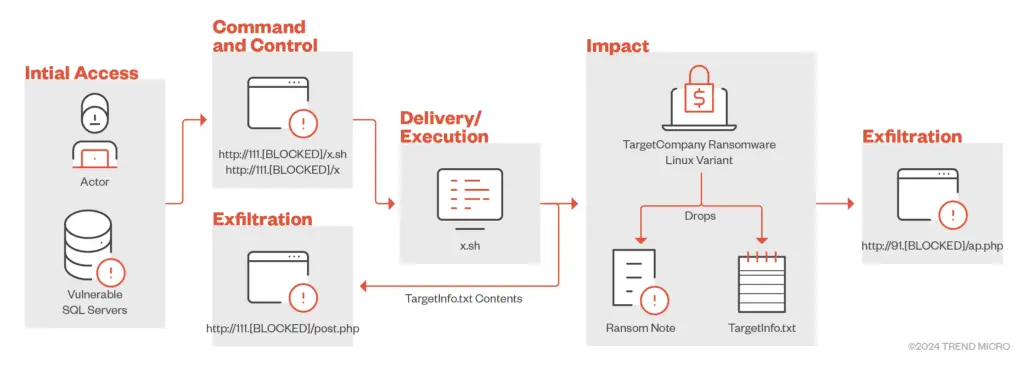
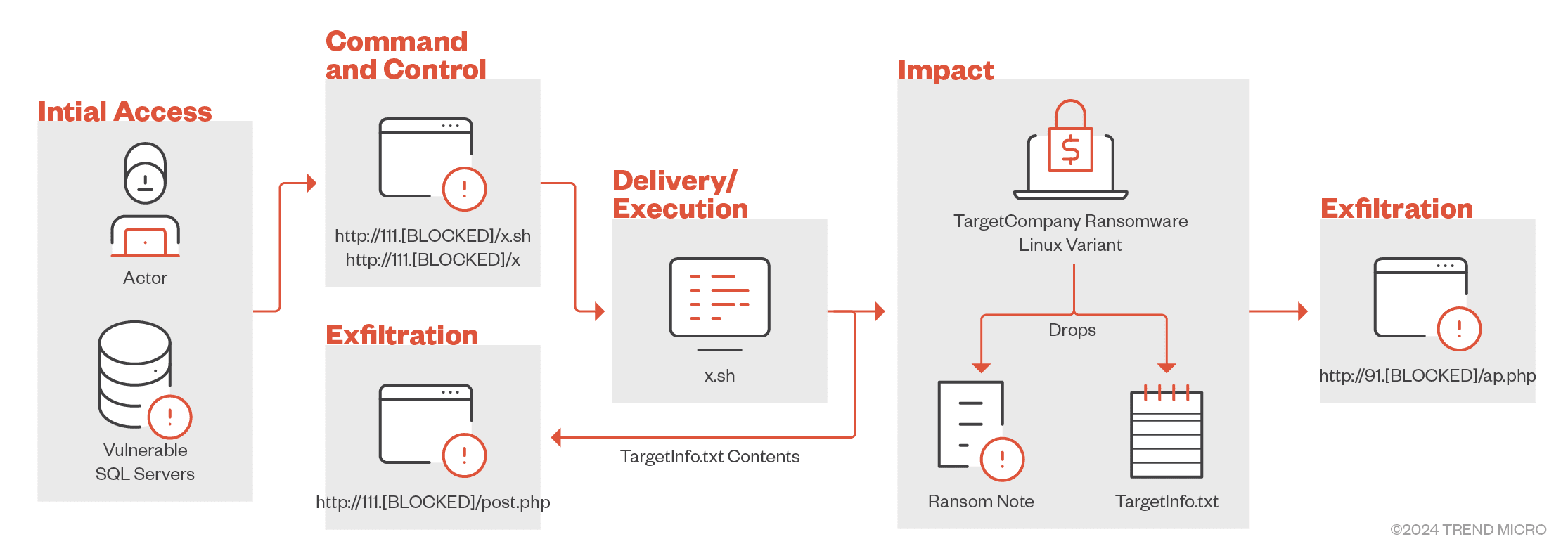
The infection chain of TargetCompany’s Linux variant
In a worrisome development, the ransomware now specifically checks if the infected machine is running in a VMWare ESXi environment. If confirmed, the variant enters “VM mode,” encrypting files with specific extensions commonly found in virtual machines. This targeted approach demonstrates the threat actor’s intention to cause maximum disruption and potential financial gain, as compromised ESXi servers can severely impact an organization’s operations.
The Linux variant also exfiltrates sensitive victim information to two different servers, possibly as a redundancy measure to ensure data backup in case one server becomes unavailable. This tactic complicates incident response for security teams, as the limited artifacts make it difficult to assess the full extent of the attack.
The IP address used for payload delivery and data exfiltration, hosted by China Mobile Communications, has not been observed in previous TargetCompany campaigns. This address, likely rented for short-term use, further complicates attribution efforts.
An affiliate named “vampire” is associated with this specific campaign, hinting at a broader operation involving high ransom demands and extensive IT system targeting. This affiliation suggests a complex network of threat actors collaborating to maximize their impact.
While the exact impact of this new variant remains unclear, its discovery serves as a stark reminder of the ever-evolving ransomware landscape. Organizations, particularly those relying on ESXi environments, are urged to review and strengthen their security measures.