Tax Extension Malware Campaign Exploits Trusted GitHub Repositories to Deliver Remcos RAT
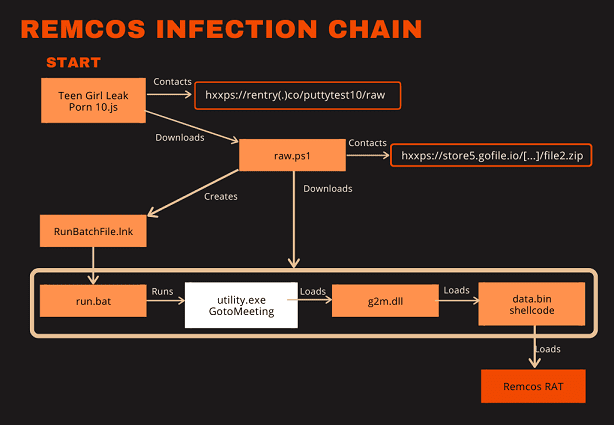
In a recent report from security researcher Jacob Malimban at Cofense Intelligence, a phishing campaign exploiting GitHub links to bypass Secure Email Gateway (SEG) defenses was detected. This campaign used trusted repositories associated with tax organizations to trick victims into downloading malware, specifically the Remcos Remote Access Trojan (RAT).
According to the report, the phishing emails promised tax extension assistance, urging recipients to download a password-protected archive from GitHub. The lure was designed to appear legitimate, with repositories from widely trusted entities such as UsTaxes, His Majesty’s Revenue & Customs (HMRC), and New Zealand’s Inland Revenue being exploited. “Using trusted repositories to deliver malware is relatively new compared to threat actors creating their own malicious GitHub repositories,” Malimban notes.
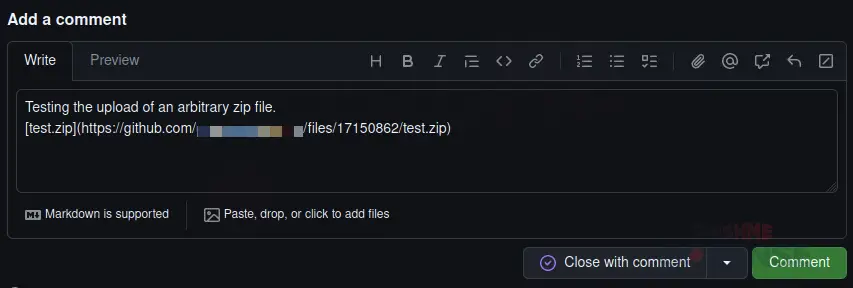
A GitHub comment that uploads a file without committing it to the repository | Image: Cofense
At the core of this campaign was GitHub’s comment system, a tool typically used for collaboration and project management. However, threat actors have found that GitHub comments provide an avenue to attach malicious files without uploading them to the repository’s source code. As Malimban points out, “GitHub comments are useful to a threat actor because malware can be attached to a comment in a GitHub repository without having to upload it to the source code files of that repository.” This allows attackers to bypass security mechanisms, as GitHub is considered a trusted platform by SEGs.
The malware-laden archives in this campaign were associated with GitHub repositories of legitimate tax organizations, making the phishing emails appear more credible. The use of password-protected archives further added a veneer of legitimacy, creating the illusion of security for handling sensitive tax-related documents. Inside these archives, however, was the Remcos RAT, a powerful tool giving attackers remote access to the victim’s machine upon installation.
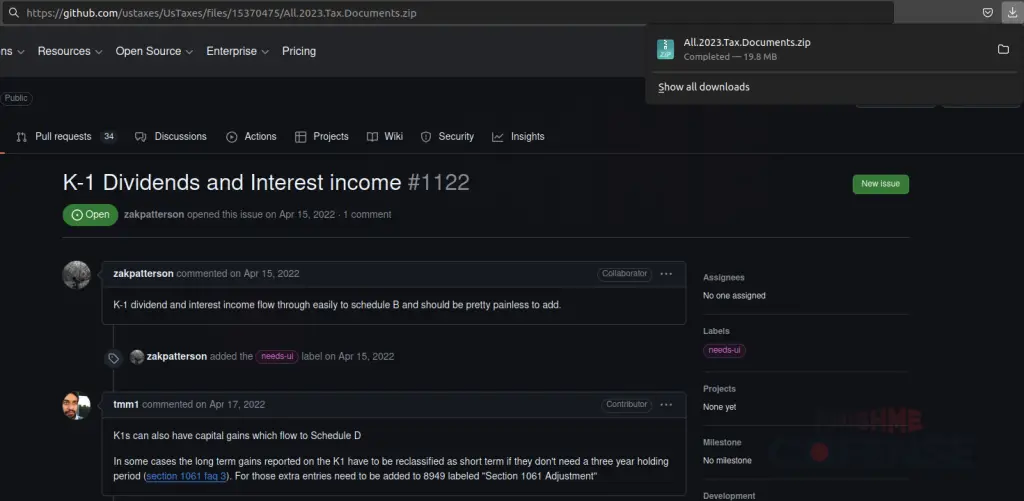
Remcos RAT archive download is still active, despite the threat actor’s comment being deleted | Image: Cofense
GitHub’s reputation as a trusted platform played a significant role in the effectiveness of this campaign. As explained by Malimban, “Emails with links to GitHub are effective at bypassing SEG security because GitHub is typically a trusted domain.” Instead of relying on methods like Google redirects or QR codes, threat actors leveraged GitHub’s legitimate repositories to host the malicious files. This allowed them to directly include links in phishing emails, bypassing standard security measures designed to filter out suspicious URLs.
The files were not embedded in the actual repository code but rather linked via comments associated with trusted repositories, making detection even more difficult. Even after the original comments were deleted, the malware links remained active, enabling continuous exploitation. This abuse of trusted platforms represents a sophisticated evolution in phishing techniques, shifting from less credible tactics to those that exploit known and trusted brands.
Though this campaign used tax-related themes, it specifically targeted financial and insurance industries. “Closer inspection of the data revealed that only two industries were targeted: Insurance and Finance,” the report states. While any sector could have been impacted given the universal nature of taxes, the attackers appeared to focus on these sectors, likely to test the effectiveness of their phishing tactics in a controlled scope.
Despite the smaller scale of the attack compared to broader campaigns like those using QR codes, the implications are significant. This campaign shows a growing sophistication among threat actors in using trusted platforms and credible themes to exploit vulnerabilities.





