Image Credit: PwC
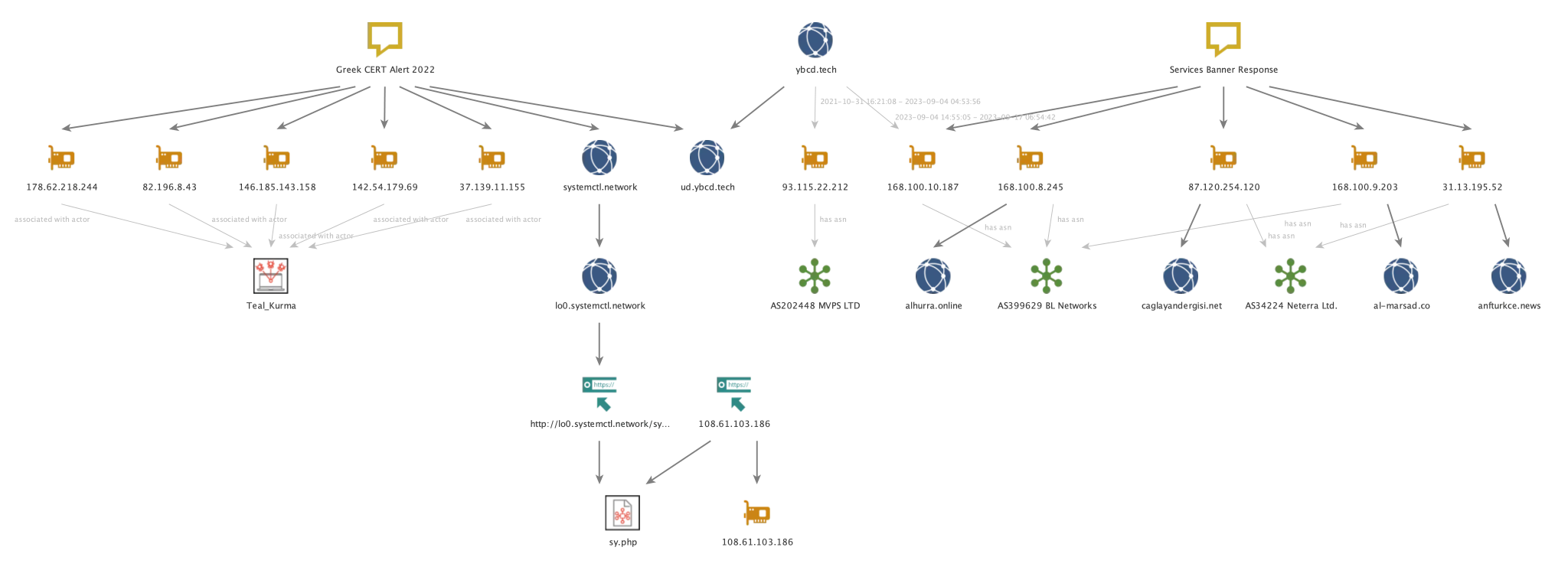
Teal Kurma, also known as Sea Turtle, represents a sophisticated and elusive cyber espionage threat that has captivated the attention of security experts worldwide. This Türkiye-nexus entity, after fading into obscurity following its initial public disclosure over three years ago, has re-emerged with a vengeance. PwC’s comprehensive analysis has brought to light the actor’s persistent and evolved cyber activities, particularly focusing on Europe and the Middle East.
Teal Kurma’s weapon of choice is ‘SnappyTCP,’ a simple yet effective reverse TCP shell for Linux/Unix systems. This tool, primarily used for establishing persistence on a system, is crafted in at least two main variants: one that relies on plaintext communication and another that utilizes TLS for secure connections. This dual approach not only signifies the actor’s adaptive tactics but also its sophistication in maintaining a low profile.

Previously, Teal Kurma was heavily involved in large-scale and prolonged Domain Name Server (DNS) hijacking attacks. These attacks misled users to malicious websites by manipulating DNS queries. Recently, the actor has diversified its arsenal, leveraging major CVEs with publicly available proof-of-concept codes such as CVE-2021-44228, CVE-2021-21974, and CVE-2022-0847, to infiltrate networks. Once inside, the actor deploys a shell script that establishes a connection to a web server under its control.
Intriguingly, Teal Kurma appears to have used code from a publicly accessible GitHub repository, raising questions about the actor’s control over or abuse of this account. This code similarity, coupled with the use of specific IP addresses, suggests a realistic probability that Teal Kurma is operating this GitHub account, further diversifying its espionage toolkit.
Furthermore, PwC’s analysis revealed multiple domains associated with Teal Kurma, spoofing NGOs, and media organizations, indicative of its espionage and surveillance objectives. This activity aligns with the actor’s historical focus and suggests a continued interest in gathering intelligence for economic or political gains.
Teal Kurma primarily targets government, telecommunication, and IT service providers, sectors rich in high-value information. This information ranges from customer metadata in telecommunication companies to technology companies targeted in supply chain attacks. The actor’s focus on these sectors underscores its intent to gather intelligence for surveillance or traditional espionage.
Geographically, Teal Kurma’s operations span the Middle East and North Africa, focusing on European countries, especially those in the Mediterranean region. This geographic targeting provides insight into the actor’s priorities and areas of interest.
PwC advises organizations to proactively search historical logs and configure alerts for identified indicators or detection content. In cases where these indicators are discovered or alerts are generated, a thorough investigation and forensic analysis are recommended. If nothing significant is found, blocking the malicious indicators is advised to prevent potential breaches.