TeamsPhisher: Send phishing messages and attachments to Microsoft Teams users
TeamsPhisher
TeamsPhisher is a Python3 program that facilitates the delivery of phishing messages and attachments to Microsoft Teams users whose organizations allow external communications.
It is not ordinarily possible to send files to Teams users outside one’s organization. Max Corbridge (@CorbridgeMax) and Tom Ellson (@tde_sec) over at JUMPSEC recently disclosed a way to get around this restriction by manipulating Teams web requests in order to alter the recipient of a message with an attached file.
TeamsPhisher incorporates this technique in addition to some earlier ones disclosed by Andrea Santese (@Medu554).
It also heavily leans upon TeamsEnum, a fantastic piece of work from Bastian Kanbach (@bka) of SSE, for the authentication part of the attack flow as well as some general helper functions.
TeamsPhisher seeks to take the best from all of these projects and yield a robust, customizable, and efficient means for authorized Red Team operations to leverage Microsoft Teams for phishing for access scenarios.
Features and demo
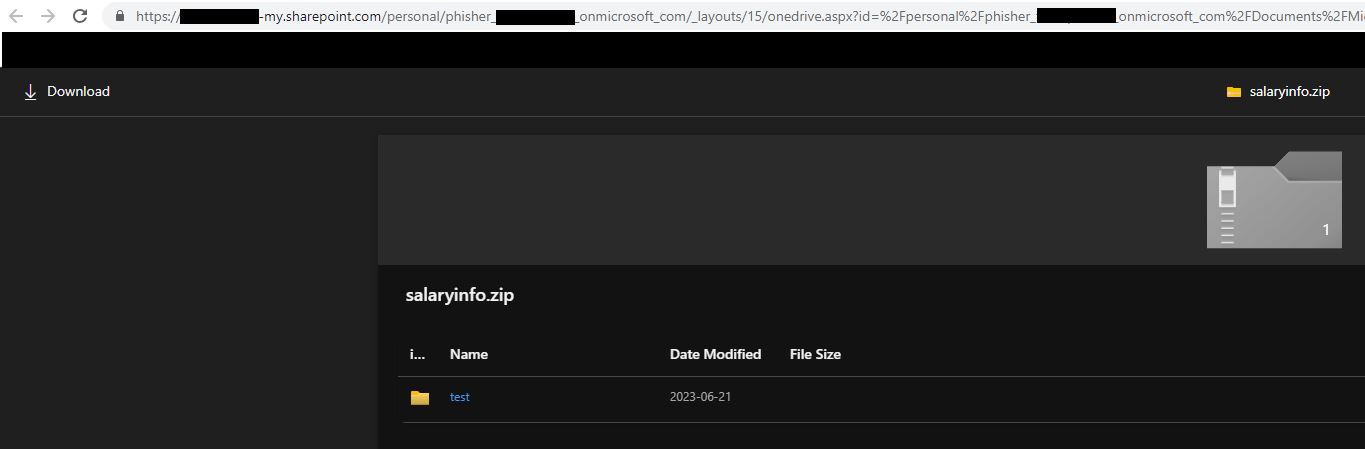
Give TeamsPhisher an attachment, a message, and a list of target Teams users. It will upload the attachment to the sender’s Sharepoint, and then iterate through the list of targets.
TeamsPhisher will first enumerate the target user and ensure that the user exists and can receive external messages. It will then create a new thread with the target user. Note this is technically a “group” chat because TeamsPhisher includes the target’s email twice; this is a neat trick from @Medu554 that will bypass the “Someone outside your organization messaged you, are you sure you want to view it” splash screen that can give our targets reason for pause.
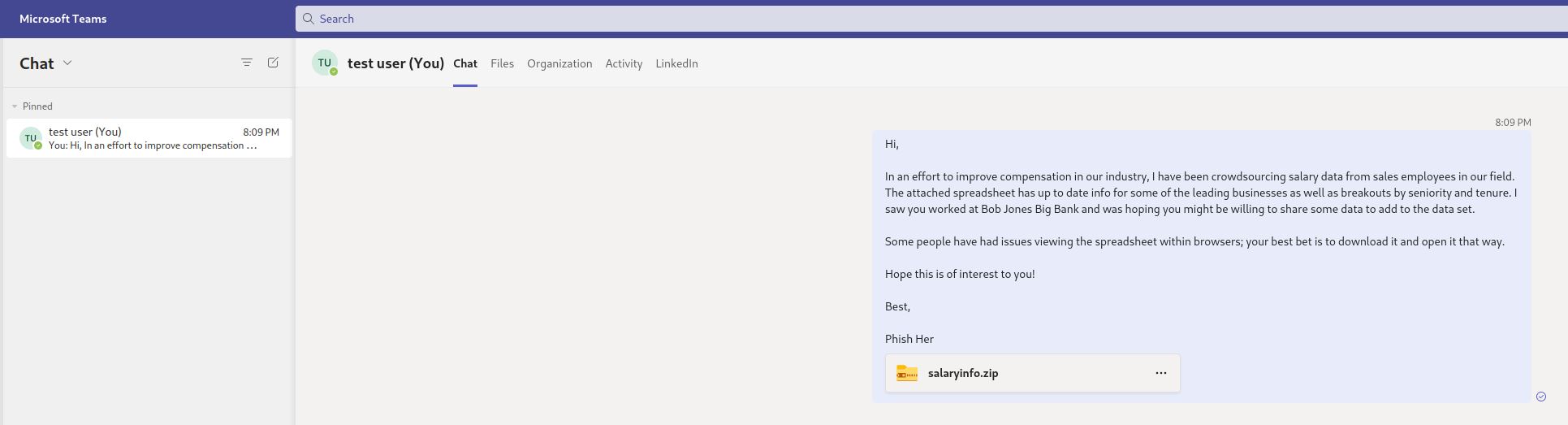
With the new thread created between our sender and the target, the specified message will be sent to the user along with a link to the attachment in Sharepoint.
Once this initial message has been sent, the created thread will be visible in the sender’s Teams GUI and can be interacted with manually if need be on a case-by-case basis.
Operational mode
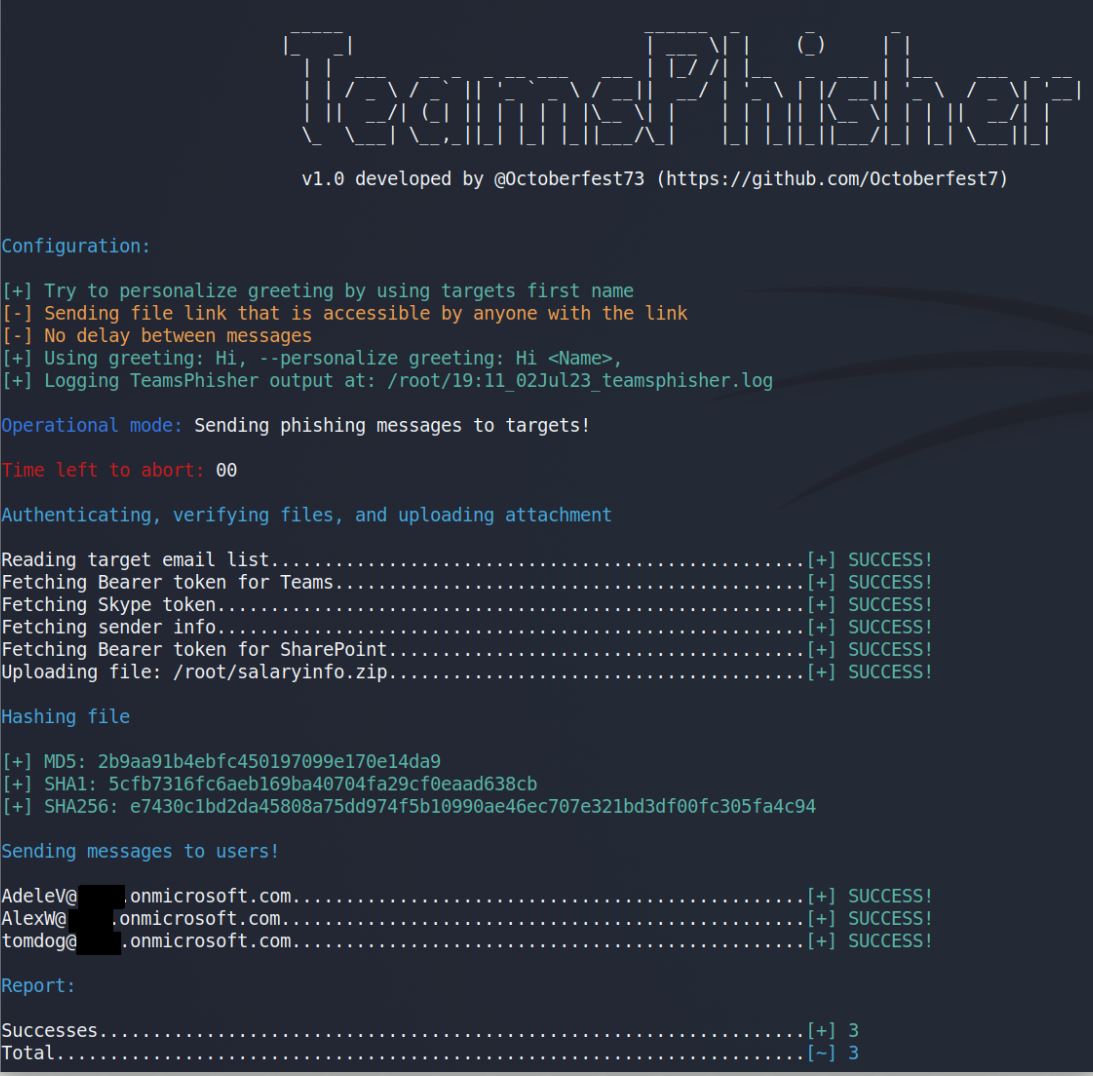
Run TeamsPhisher for real. Send phishing messages to targets.
Command:
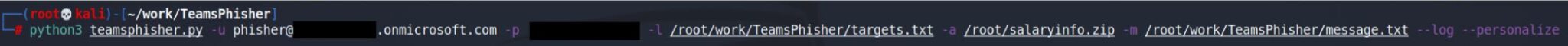
Targets.txt:
Message.txt:
TeamsPhisher output:

Sender’s view:
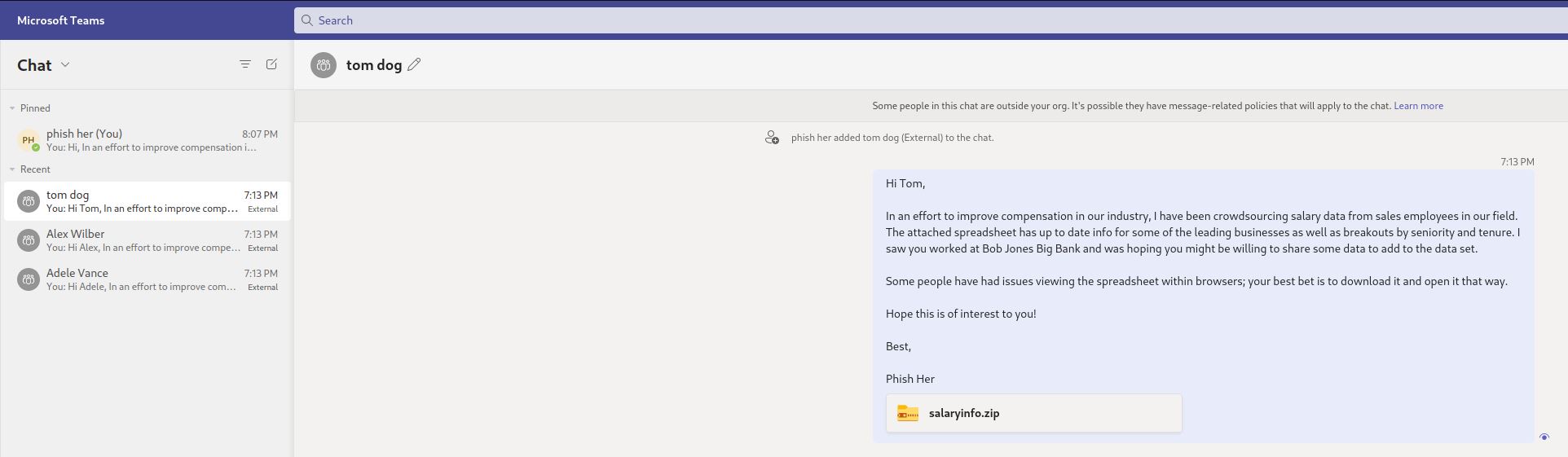
Targets view:
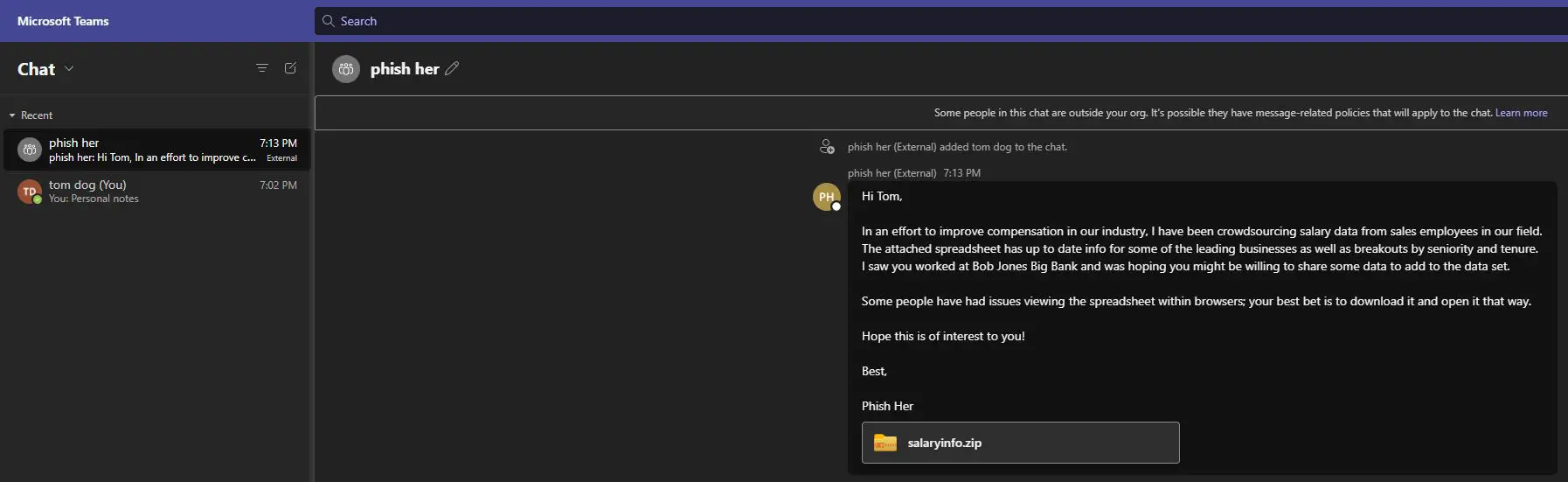
Attached file:
Preview mode
Run TeamsPhisher in preview mode in order to verify your list of targets, preview their “friendly names” (if TeamsPhisher can resolve them using the –personalize switch), and send a test message to your own sender’s account in order to verify everything looks as you want it.
TeamsPhisher output:
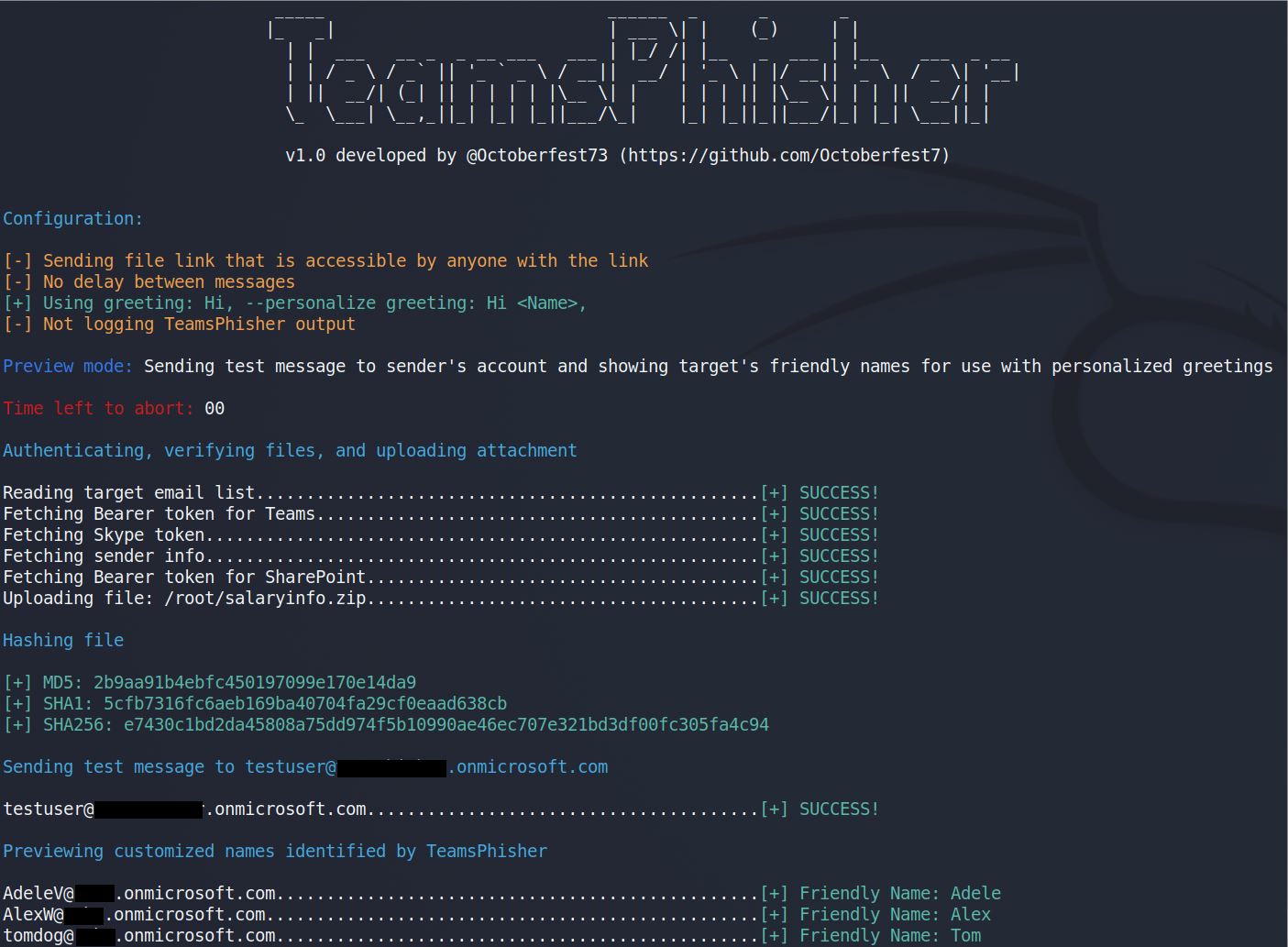
Sender’s view:
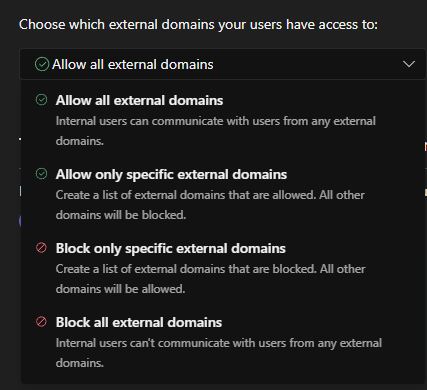
Mitigation
Organizations can mitigate the risk posed by this vulnerability by managing the options related to external access via the Microsoft Teams admin center under Users -> External access.
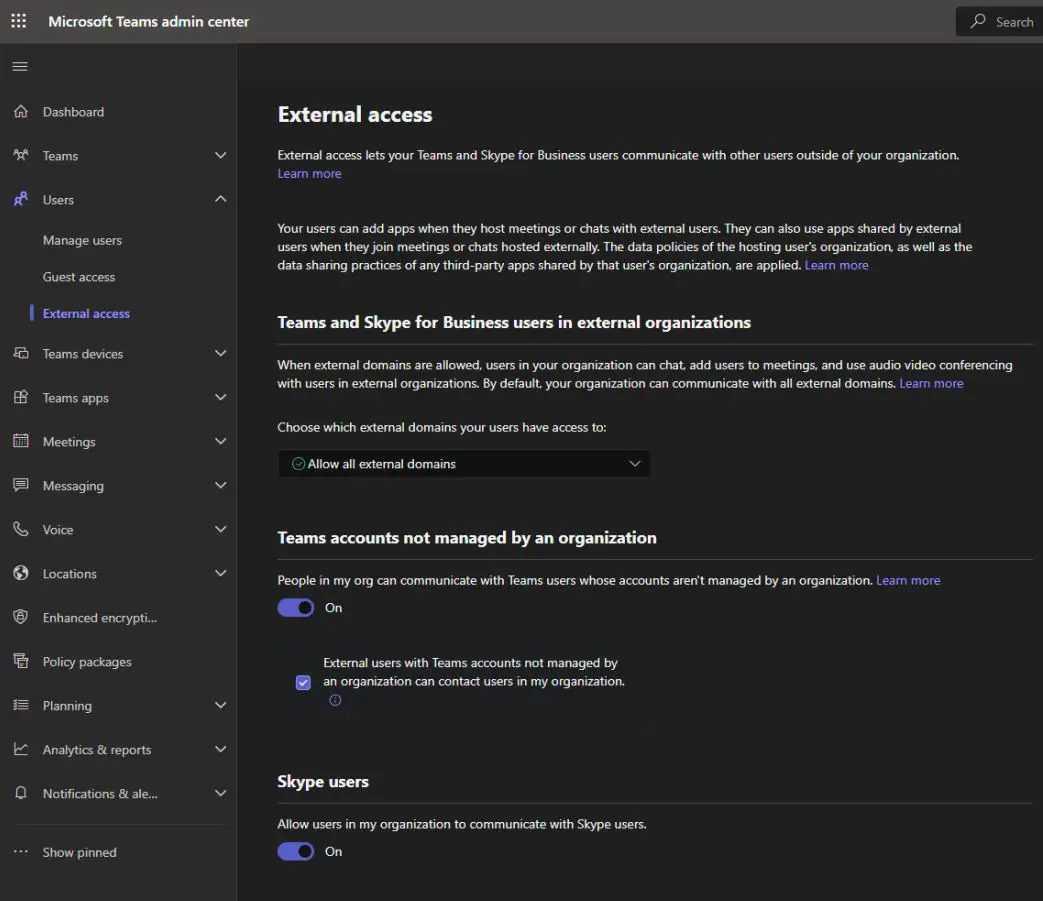
Microsoft provides flexibility to organizations to choose the best permissions to fit their needs, including a universal block as well as whitelisting only specific external tenants for communications.