Technical Details Released for Check Point Remote Access VPN 0-Day Flaw
Security researchers at watchTowr Labs have detailed a zero-day vulnerability (CVE-2024-24919) in Check Point’s Remote Access VPN appliances, which is actively being exploited by malicious actors. The vulnerability allows attackers to read sensitive information on internet-connected gateways with remote access VPN or mobile access enabled. This flaw affects a wide range of Check Point products, including CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, and Quantum Spark Appliances.

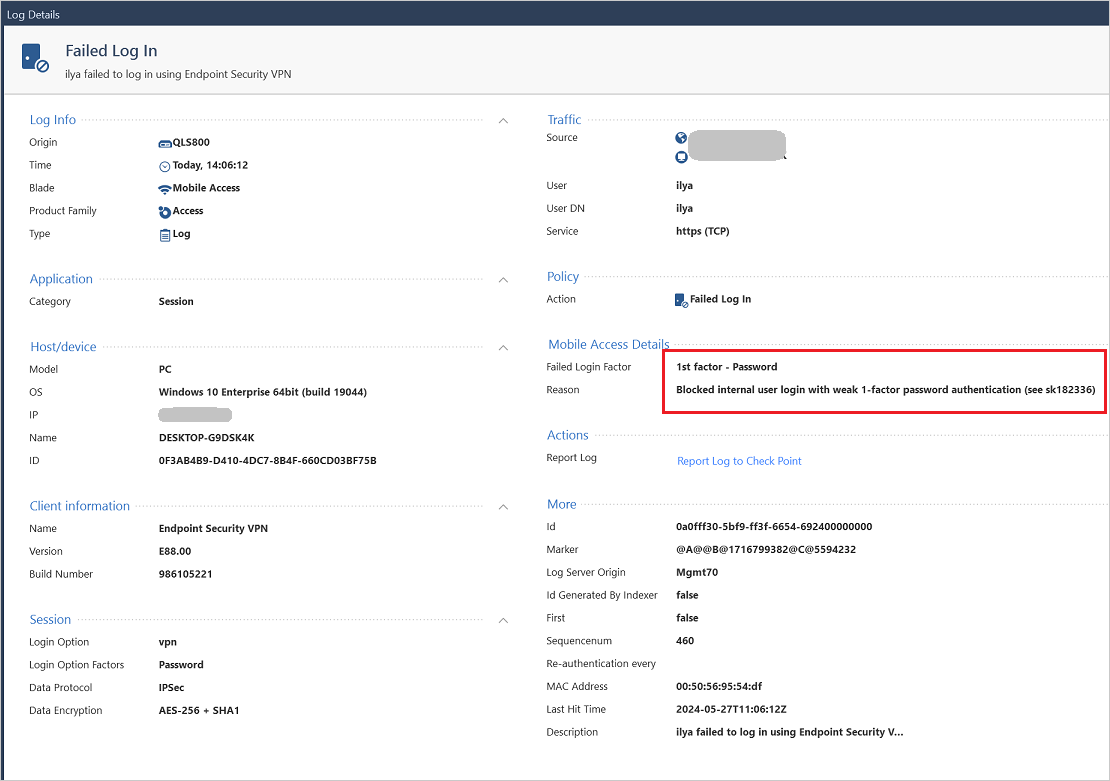
Blocked login attempt
Image: Check Point
CVE-2024-24919 has been actively exploited since April 30, according to cybersecurity company mnemonic. The vulnerability is particularly critical due to its ease of exploitation, requiring no user interaction or privileges on the targeted Check Point security gateways. An attacker can exploit this flaw to enumerate and extract password hashes for all local accounts, including those used to connect to Active Directory.
Upon detailed analysis, watchTowr Labs discovered new code designed to log “Suspected path traversal attack from,” indicating a path traversal vulnerability. Functions like send_path_traversal_alert_log and sanitize_filename were added, pointing to a bug in the endpoint /clients/MyCRL. This bug allows attackers to exploit the system’s handling of URLs and POST bodies, enabling directory traversal and access to sensitive files. The severity of this bug, initially understated, has been confirmed to allow arbitrary file reads, including critical files like the shadow password file, undermining the security of the affected devices.
“This entry isn’t a file, but a directory, which would mean we can traverse into it and then back out via the venerable .. . As long as we have the string CSHELL/ somewhere in the requested file, the request will be accepted,” the researcher wrote.
A POST request to trigger the bug:
The vulnerability impacts the following product versions:
- CloudGuard Network: R80.20.x, R80.20SP (EOL), R80.40 (EOL), R81, R81.10, R81.10.x, R81.20
- Quantum Maestro and Quantum Scalable Chassis: R81.20, R81.10, R80.40, R80.30SP, R80.20SP
- Quantum Spark Gateways: R81.10.x, R80.20.x, R77.20.x
Check Point has released security updates to address the flaw:
- Quantum Security Gateway and CloudGuard Network Security: R81.20, R81.10, R81, R80.40
- Quantum Maestro and Quantum Scalable Chassis: R81.20, R81.10, R80.40, R80.30SP, R80.20SP
- Quantum Spark Gateways: R81.10.x, R80.20.x, R77.20.x
To apply the update, navigate to the Security Gateway portal, go to Software Updates > Available Updates > Hotfix Updates, and click ‘Install.’ The update process takes approximately 10 minutes and requires a reboot.
For those unable to apply the update immediately, it is advised to enhance their security posture by updating the Active Directory (AD) password used for authentication. Check Point has also provided a remote access validation script, VPNcheck.sh, which can be uploaded to ‘SmartConsole’ to review results and take appropriate actions.
Check Point has created a FAQ page with more information about CVE-2024-24919, including an IPS signature and manual hotfix installation instructions. For more details on updating the AD password and using the VPNcheck.sh script, users can refer to Check Point’s security bulletin.





