How Attackers Exploit PAM’s Modular Design on Linux
The Linux ecosystem offers its users a comprehensive method for user access and authorization through the Pluggable Authentication Modules (PAM). But what exactly is PAM and why should you be concerned about its security implications? Security researchers from Palo Alto Networks have detailed this on a blog.
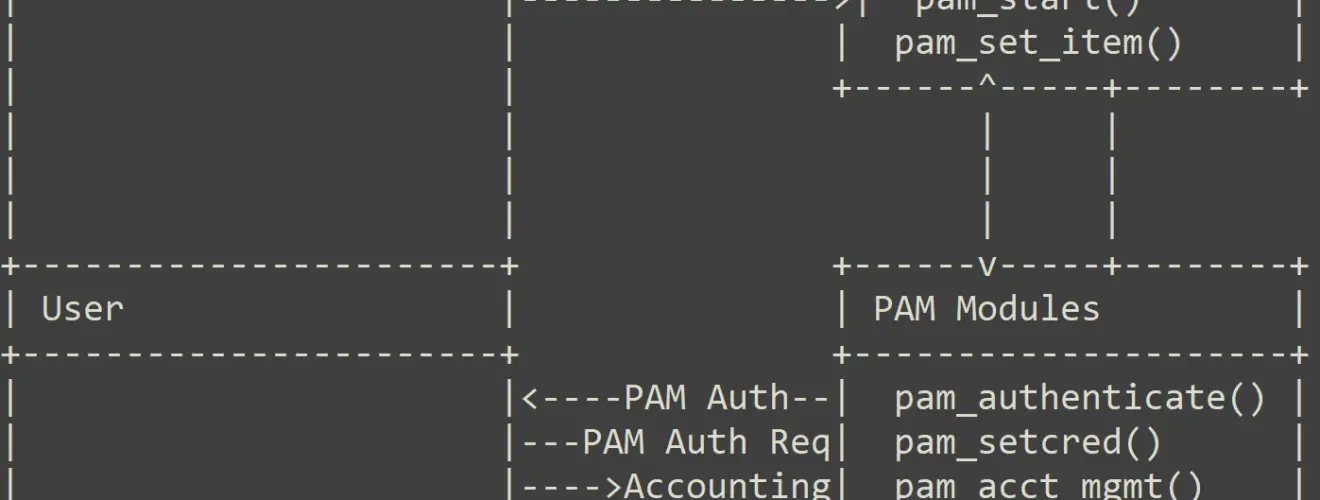
In essence, PAM serves as a unified authentication framework for Linux systems. The beauty of PAM lies in its modular architecture, anchored on pluggable modules. Think of these modules as shared object libraries designed to oversee specific authentication tasks. PAM’s flexibility means these modules can be crafted independently and then plugged in to amplify PAM’s functionalities.

SSH authentication process
For instance, the `pam_unix` module lets applications authenticate users based on their Unix passwords, all by harnessing the power of traditional Unix-style password files.
Central to PAM is a library, aptly named `libpam`. It’s the linchpin that links applications to PAM modules through PAM APIs. So, when an application, say SSH or the GNOME Display Manager, seeks authentication, `libpam` jumps into action, coordinating between the application and the relevant PAM modules.
It’s clear that PAM’s design exudes flexibility. Yet, this same trait can be weaponized by attackers. By tapping into PAM’s APIs, malware can intercept the authentication flow, thereby jeopardizing system security.
Consider these notable malware families that have maliciously leveraged PAM APIs:
- Orbit malware: Found in 2022, this malware keeps tabs on SSH passwords by hooking into PAM APIs like `pam_open_session` and `pam_authenticate`.
- Azazel rootkit: This open-source rootkit, designed for older Linux kernels, utilizes PAM APIs to infiltrate victims’ systems.
- Derusbi malware: Adept at targeting Linux and Windows, Derusbi uses PAM APIs to aid its espionage and illicit activities.
- Skidmap malware: Active since 2019, Skidmap cunningly replaces a legitimate PAM library with its malicious variant, facilitating unauthorized access.
Despite the vulnerabilities, PAM remains a cornerstone for Linux due to its standardized and secure authentication framework. The challenge lies in continually monitoring PAM APIs, particularly in isolated environments, to thwart malicious intrusions.
Vigilance against unusual activities, especially around the `LD_PRELOAD` environment variable, can offer early warnings against attempts to misuse PAM APIs. By staying one step ahead and understanding the intricate interplay of PAM in the Linux universe, you can build robust defenses against threats lurking in the digital shadows.