How Attackers Exploit PAM’s Modular Design on Linux
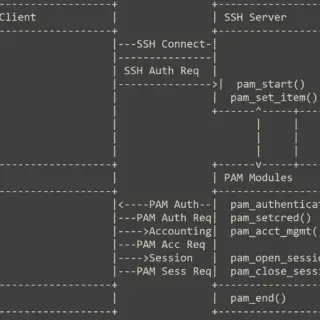
The Linux ecosystem offers its users a comprehensive method for user access and authorization through the Pluggable Authentication Modules (PAM). But what exactly is PAM and why should you be concerned about its security...