A new and dangerous cross-site scripting (XSS) vulnerability has been discovered in Microsoft Office, affecting hundreds of millions of users worldwide. The vulnerability was disclosed by cybersecurity researchers @adm1nkyj and @justlikebono at PKSecurity, and it resides in the “Online Videos” tab, which allows users to insert external videos into their documents.
The “Online Videos” feature within Microsoft Office, at face value, offers a touch of modern functionality to an otherwise traditional program. It lets users integrate videos from external sources directly into their documents. But here’s where things get dicey.
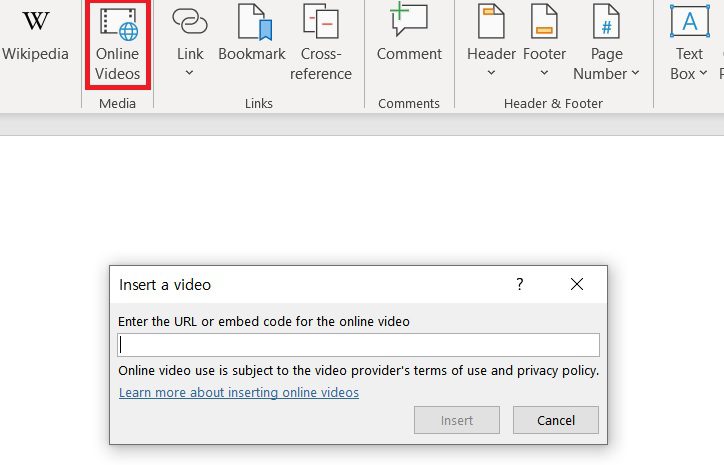
When a user plays one of these embedded external videos, Office does its due diligence by verifying the video’s source, determining if it’s from a reliable provider, say YouTube. To achieve this, it relies on a regular expression matched against the video URL. Once passed, a request is dispatched to a server that fetches details like the video’s title and thumbnail.
Yet, it’s precisely here, within this process, that the vulnerability emerges.
The server’s response includes the video’s title, description, and an HTML iframe tag which facilitates video play. The flaw, however, lies in how the server treats the video title. It is added to the “title” attribute of the iframe tag sans any validation.
For those savvy in cyber trickery, this offers a golden ticket. By craftily using double quotes, one can tamper with this iframe tag. They can introduce an onload attribute that the server will unknowingly send back.
Such manipulation allows for injected JS code (from the attacker) to find its way into an HTML file that Word relies upon, executed via Edge Webview. This particular sequence culminates with potential malicious activities due to certain sandbox attributes of the iframe.
Given the sandbox permissions in place, this vulnerability is not just a quiet threat. It grants permissions to execute JavaScript, run desired URIs, or even beckon scripts from a foreign server.
How to reproduce the vulnerability
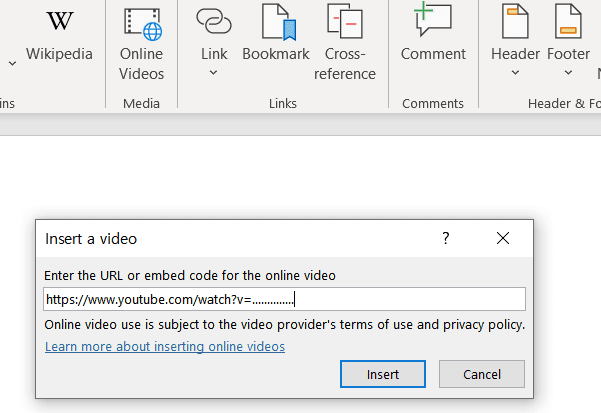
- Create a YouTube video with a title that includes a payload for inserting the onload attribute.
- Click on the Online Videos tab in Word and insert the URL of the malicious video into the document.
- Set up a simple web server that allows CORS and responds with malicious JavaScript, as below. (The example executes calc.exe through the calculator URI Scheme.)
Simply put, a malicious actor could forge a Word document embedding a particular video. Once an unsuspecting user plays the video, it can unleash arbitrary JavaScript code. Familiar with past Office exploits, such as CVE-2021-40444 and CVE-2022-30190 (Folina)? These too started with the firing of arbitrary javascript.
There’s even a more sinister possibility: combining this flaw with other vulnerabilities could cascade into a critical Remote Code Execution (RCE) exploit.
The most alarming aspect is the simplicity of exploiting this vulnerability. Given the appeal of multimedia, it’s hardly challenging for an attacker to lure a user into playing an embedded video.
Microsoft has released a patch for this vulnerability, so it is important to update your version of Office as soon as possible. In the meantime, there are a few things you can do to protect yourself:
- Do not open Word documents from unknown senders.
- Be careful about clicking on links in email messages, even if they appear to come from someone you know.
- If you do need to open a Word document from an unknown sender, disable macros before doing so. To do this, open the document and click on the File tab. Then, click on Options and Trust Center. Under Trust Center Settings, click on Macro Settings. Select Disable all macros (recommended) and click OK.
Microsoft has also provided the following guidance for IT administrators:
- Deploy the latest security updates for Microsoft Office.
- Implement a strong email security solution to filter out malicious email messages.
- Educate users about the dangers of phishing attacks and how to protect themselves.