Telegram: The Dark Horse of Website Malware Attacks
Telegram, the messaging platform known for its emphasis on privacy and security, has been revealed as a surprisingly potent tool in the hands of cybercriminals. A new in-depth analysis by Krasimir Konov, malware analyst at Sucuri, exposes how hackers are leveraging Telegram’s unique features to execute sophisticated website attacks.
Telegram’s flexibility and robust privacy features, which have garnered it a substantial user base, are now being leveraged by cybercriminals to execute sophisticated attacks. By utilizing Telegram’s API, hackers create bots that oversee and manage their malicious activities across compromised websites. Here’s a closer look at how attackers are exploiting Telegram:
- Real-time Alerts: Telegram bots act as vigilant sentinels, notifying attackers the moment a website is compromised. This includes alerts on data breaches, malware implants, and even administrator interactions.
- Data Exfiltration: Stolen data – from login credentials to sensitive personal information – is swiftly and stealthily funneled through Telegram’s encrypted channels, evading traditional security measures.
- Command and Control: Gone are the days of easily traceable command-and-control servers. Hackers now use seemingly innocuous Telegram messages to instruct malware to spread, initiate attacks, or download additional components.
- Evasion and Anonymity: Telegram’s strong encryption and privacy policies provide a cloak of anonymity for attackers, making it incredibly difficult to trace their actions.
Last year, Sucuri’s research team identified numerous malware infections leveraging Telegram in their website attacks. They cleaned over 11,000 malicious files from more than 290 infected websites related to this malware. Konov’s analysis highlights numerous real-world examples of Telegram-based website attacks, including:
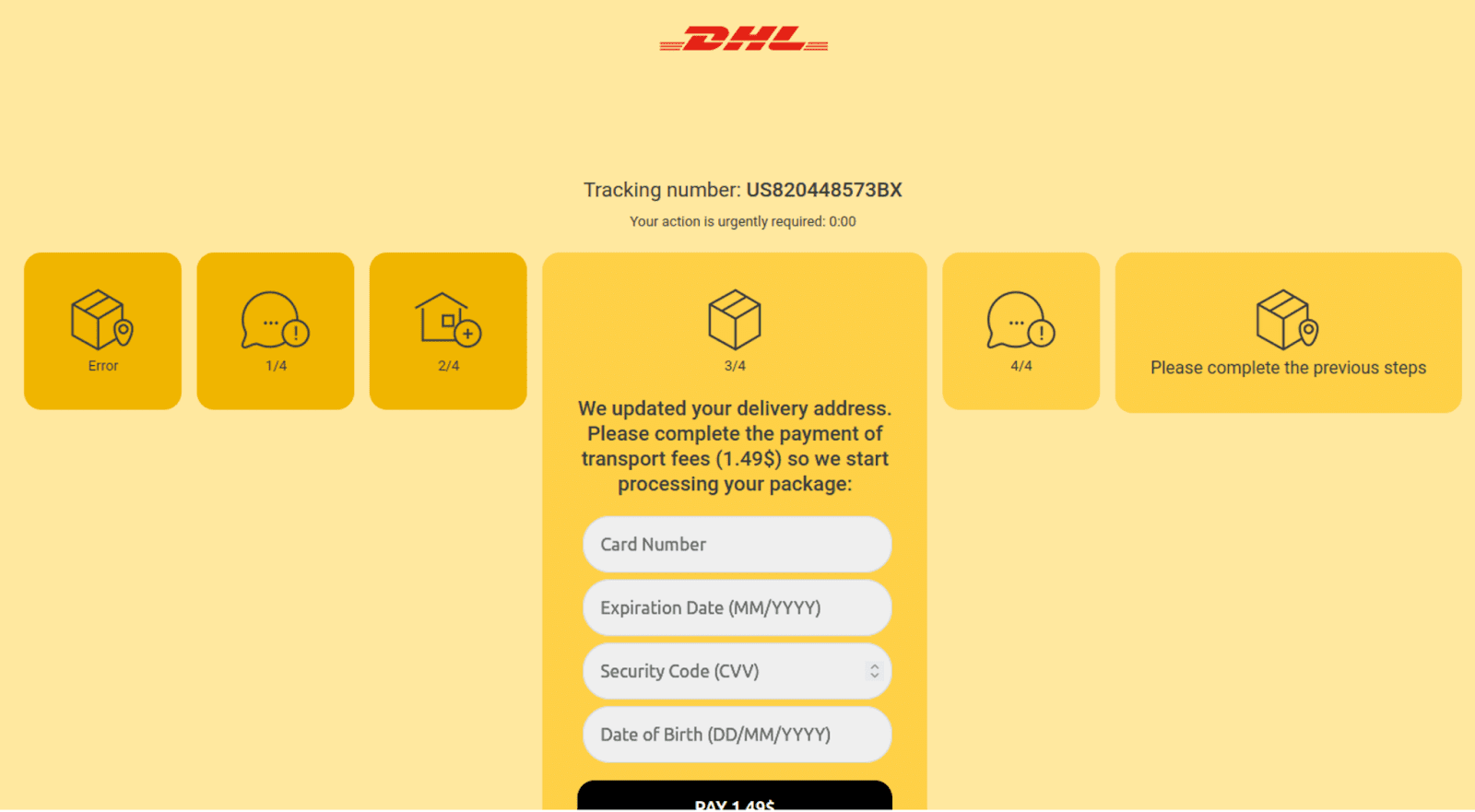
Fake DHL phishing page designed to trick unsuspecting victims into providing credit card details
- Phishing for Credit Card Details: Attackers replicated DHL’s tracking page to steal personal information, then exfiltrated the data through Telegram, bypassing traditional security mechanisms.
- Server-Side Data Exfiltration: Malicious code injected into a WordPress login page captured credentials and sent them directly to a Telegram bot.
While other messaging apps offer encryption, Telegram stands out due to its accessible API and potential for automation. Unlike WhatsApp and Signal, it doesn’t require a directly linked phone number, enhancing the attacker’s anonymity.
The revelation of Telegram’s role in website malware underscores the ever-evolving nature of cyber threats. It’s a reminder that even the most secure platforms can be turned against us. Cybersecurity professionals and everyday users alike must remain vigilant and adapt their defenses accordingly.





