Telerecon: OSINT reconnaissance framework for researching, investigating, and scraping Telegram
Telerecon
Telerecon is a comprehensive OSINT reconnaissance framework for researching, investigating, and scraping Telegram.
For example: Input a target username, and Telerecon efficiently crawls across multiple chats gathering profile metadata, account activity, and user messages, extracting potential selectors, ideological indicators, identifying named entities, indicators of capability and violent intent, constructing a network map of possible associates, and a EXIF metadata geo-map, amongst various other analytics.
Other features of Telerecon include scraping Telegram channels/groups, automated forward mapping for exploratory network analysis, and conducting a channel community census.

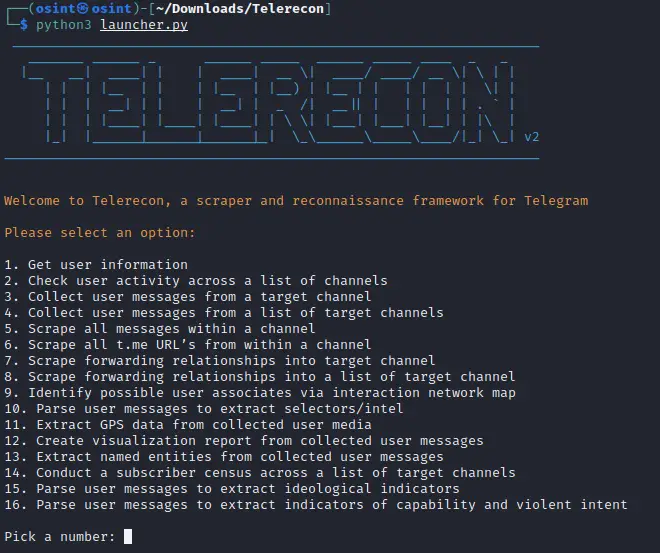
Options
-
Get user information: Search a @username and return any public user information (username, first name, last name, phone number, UserID, Bio, Online status, profile picture).
-
Check user activity across a list of channels: Iterate through a txt/csv directory list of Telegram channels, looking for any messages by the target username. (Assumes directory list is in the primary Telerecon directory).
-
Collect user messages from a target channel: Collect and compile any messages from the target username in a target channel. Option to also download media (NOTE – media download slows collection).
-
Collect user messages from a list of target channels: iterate through a txt/csv directory list of Telegram channels, collecting and compiling any messages by the target username. Option to also download media (NOTE – media download slows collection). Assumes directory list is in the primary Telerecon directory.
-
Scrape all messages within a channel: Collect and compile messages in a target channel. Download full history, last 24 hours, or custom date range.
-
Scrape all t.me URLs from within a channel: parses a channel and extracts all t.me URLs mentioned within. This is designed to easily create a Telegram directory.
-
Scrape forwarding relationships into target channel: Scrape forwarding relationships into a target channel. Exporting a Gephi optimised adjacency list, and URL directory of the discovered channels.
-
Scrape forwarding relationships into a list of target channels: Iterate through a txt/csv directory list of Telegram channels, scraping forwarding relationships. Exporting a Gephi optimised adjacency list, and URL directory of the discovered channels. Afterwards can use terminal commands to merge outputs. (i.e. merge URLs lists = cat *.csv | sort | uniq > combined.csv)
-
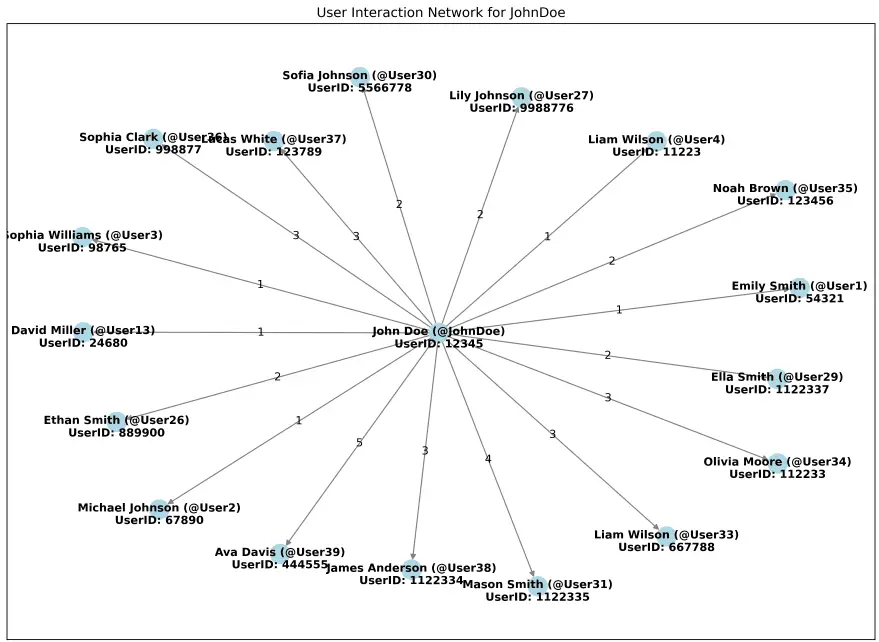
Identify possible user associates via interaction network map: Assumes user messages have already been collected. Constructs a network visualisation showing replies/interactions with other users (useful for identifying possible associates).

- Parse user messages to extract selectors/intel: Outputting a report containing any potential phone numbers, emails, or other selectors based on regex and key phrase targeting (the report includes citations for ease of verification). Key phrases are customizable by editing the script.

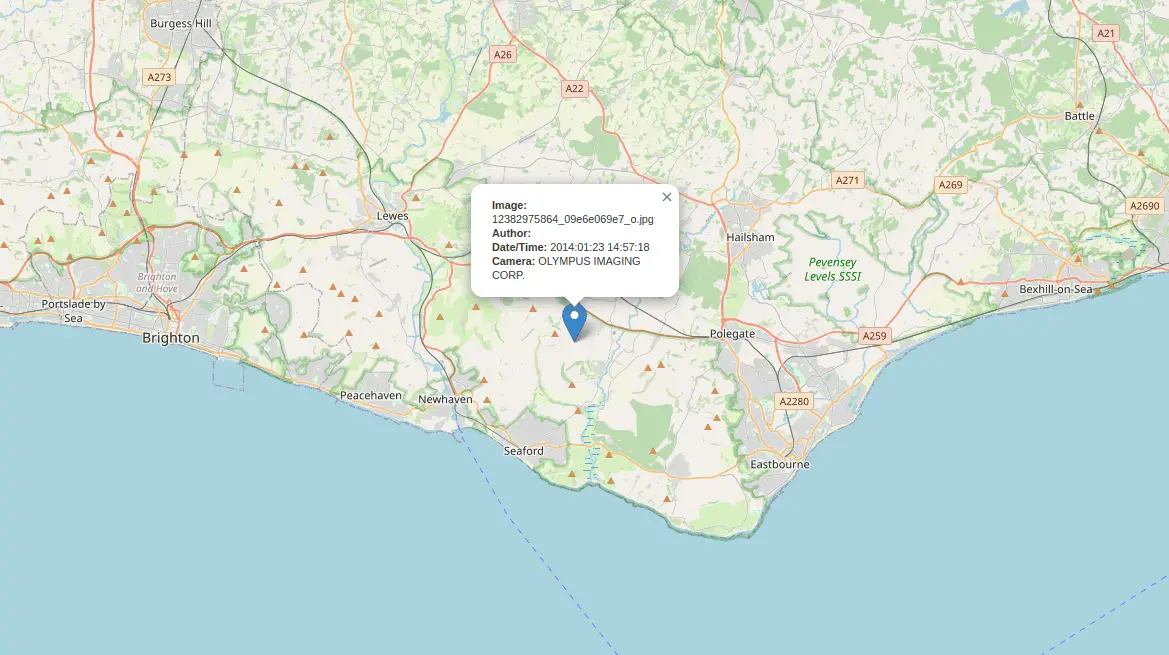
- Extract GPS data from collected user media: Assumes user messages have already been collected. Creates a compiled spreadsheet of extracted EXIF metadata from all images, and a map visualization displaying any extracted GPS metadata.

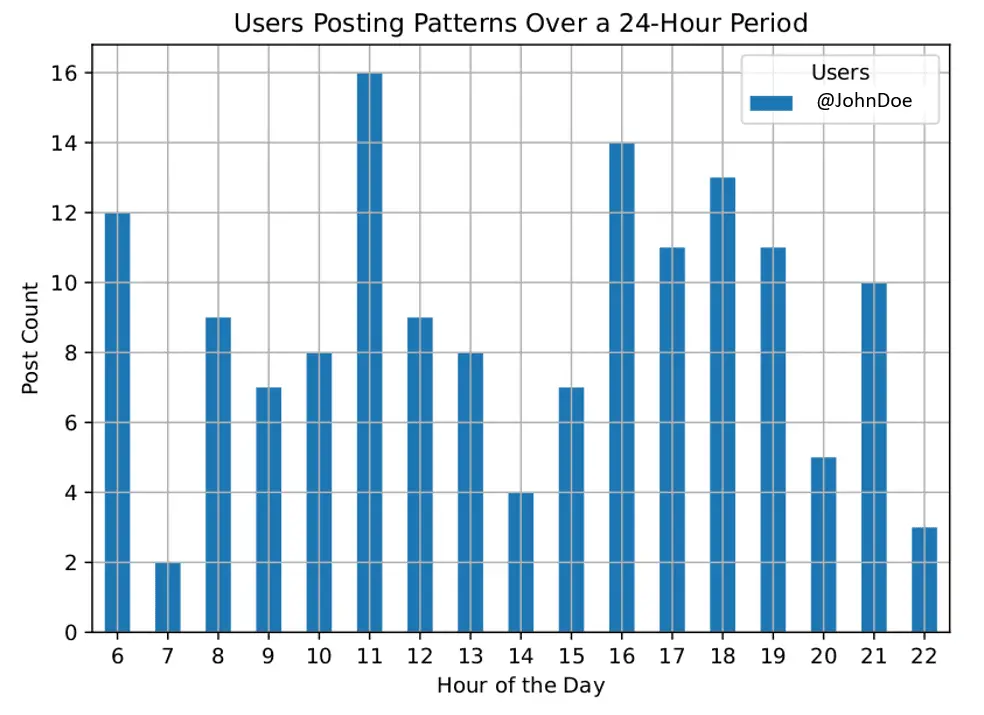
- Create visulisation report from collected user messages: Assumes user messages have already been collected. Creates a comprehensive analytics report showing user postage patterns over time (useful for pattern of life analysis etc).

- Extract named entities from collected user messages: Assumes user messages have already been collected. Creates a report containing extracted Person, Organisation, Location, and date entities extracted by named entity recognition. While not perfect, this function can be useful in identifying key entities for further investigation within big datasets.

-
Conduct a subscriber census across a list of target channels: Iterate through a txt/csv directory list of Telegram channels, reporting the number of subscribers/members.
-
Parse user messages for ideological indicators: Assumes user messages have already been collected. Outputs a report containing keyphrases that could indicate ideology (the report includes citations for ease of verification). Key phrases are customizable by editing the script. Default function parses text to detect hate speech/racism, white-identity-motivated extremism, conspiratorial ideation, sovereign citizen, and incel terminology. Note: Context is key, mentioning a keyword does not make a user ideologically motivated. However, this function is still useful for rapidly assessing a target.
-
Parse user messages for indicators of capability and violent intent: Assumes user messages have already been collected. Outputs a threat assessment containing keyphrases that could indicate capability or intent (the report includes citations for ease of verification). Indicators of capability are measured by a regex proximity search looking for the target discussing having or seeking to acquire weapons/capability. Indicators of violent intent is detected by the mention of specific threatening phrases. While this method is not perfect and may generate some noise it is still highly useful for rapidly conducting a threat assessment. The Key phrases are customizable by editing the script.

Install & Use
Copyright (C) 2024 sockysec