As digital currencies soared, extraordinarily disinterested attackers turned their attention to it. Last week, a 24-year-old Chicago man was arrested on suspicion of stealing bitcoin and Litecoin worth $2 million from his employer. In addition to the traditional digital theft crime, the frenzy of cryptocurrencies has spawned even more massive hidden hijackings, such as mining its computing resources without the user’s knowledge. Although most victims of hidden hijacking are ordinary PC users, large cloud infrastructures cannot escape.

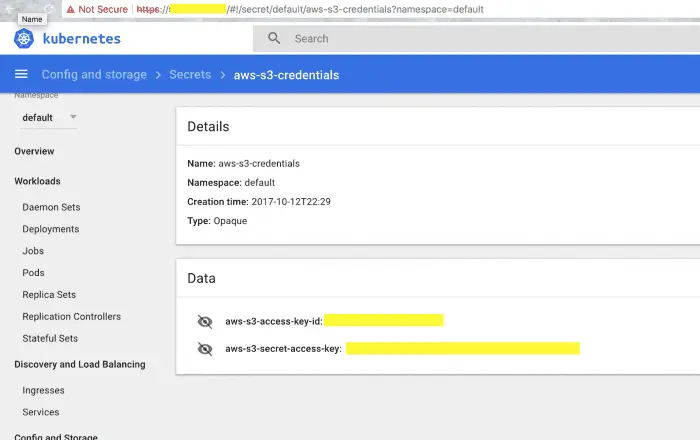
Figure -1: Tesla AWS credentials exposed
A new study from RedLock pointed out that the public cloud infrastructure of the well-known electric car company Tesla has also been used by hackers to encrypt money mining operations.
Hackers infiltrated the Tesla Kubernetes console, which lacks password protection, and just one node succeeded. Tesla’s cloud access to the AWS environment was exposed, including the S3 family bucket (including telemetry data, etc.) Sensitive information).
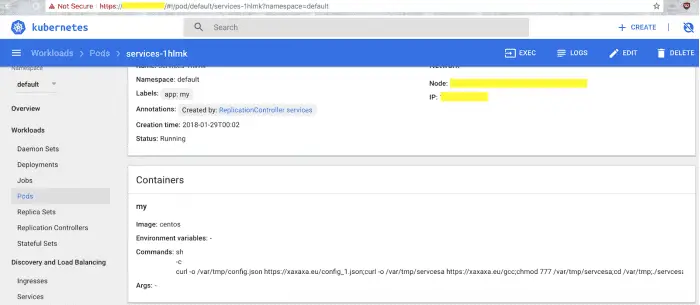
Figure-2: Mining script running on Tesla Kubernetes node
What needs to be pointed out is that for its own illegal activities are not detected, it uses a variety of methods to hide. For example, mining software can be well tuned to keep CPU usage in the normal range.

Figure-3: RedLock Bitcoin Mining Traffic Test
Fortunately, RedLock immediately reported the problem to Tesla, who also implemented the fix in time.
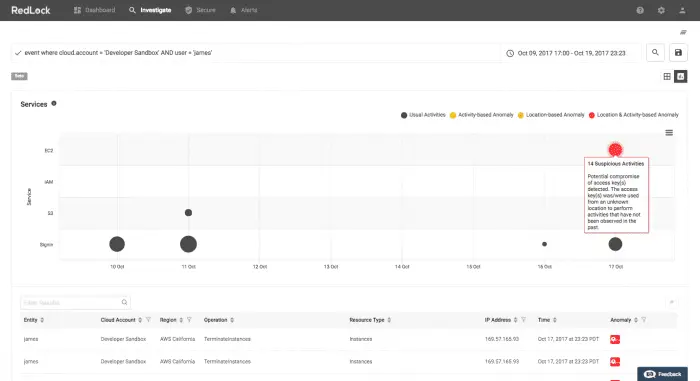
Figure-4: RedLock Abnormal Behavior Test
Tesla said in a statement to Engadget:
“We maintain a bug bounty program to encourage this type of research, and we addressed this vulnerability within hours of learning about it. The impact seems to be limited to internally-used engineering test cars only, and our initial investigation found no indication that customer privacy or vehicle safety or security was compromised in any way.”