Argentine security researchers, SHEILA AYELEN BERTA and CLAUDIO CARACCIOLO will plan to show how to use the hardware backdoor Bicho to remotely control the CAN bus in the Hack In The Box Conference in April 2018, held in Amsterdam.
Bicho is an open source hardware backdoor that is small and easy to hide. It is based on the PIC18F2580 microcontroller and can receive commands via SMS, “automated launch of attack payloads at a GPS location or when a specific car status is reached; and a configuration interface that allows users to create attack payloads in an easy manner.”, which is provided by the popular SIM800L GSM module.

In an interview, Berta said that they did not use the open source electronic prototype platform Arduino (which can sense the environment through various sensors, control the lighting, motors, and other devices to feedback and influence the environment), but instead developed the hardware themselves and Which integrates a SIM800L module, insert a GSM chip to identify the phone number. After sending a text message to the phone number, the firmware in the hardware backdoor can receive the operation command.
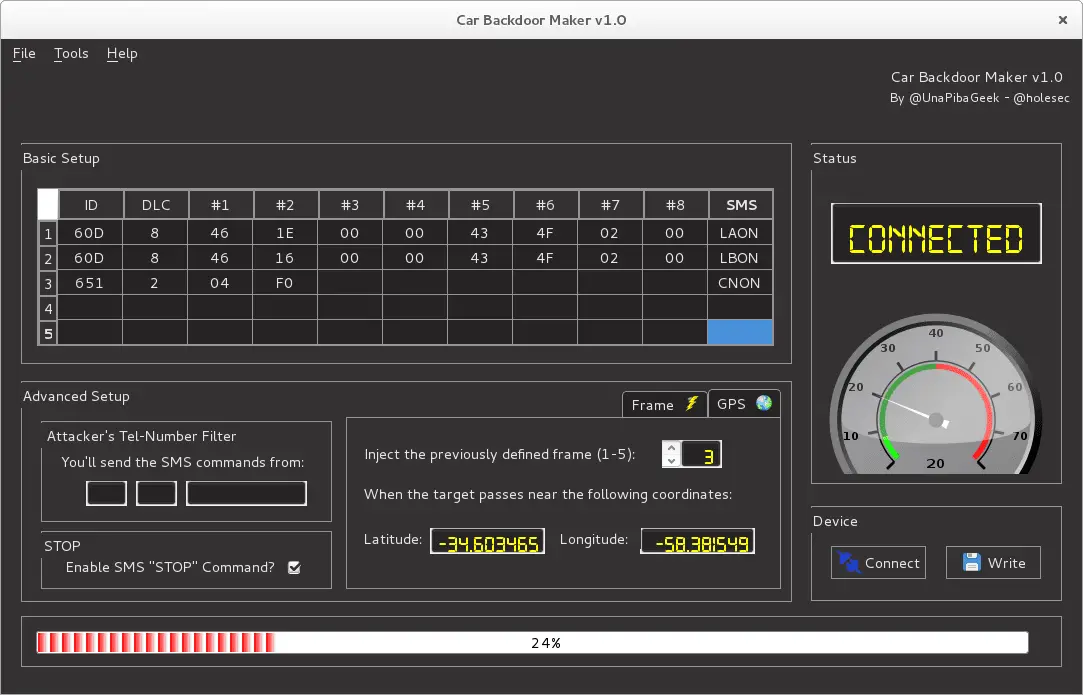
Bicho was pre-programmed with the open-source “Car Backdoor Maker” project that researchers have developed. This software has a very intuitive graphical interface. Before using the back door, it must be connected via USB to the computer running the software and preloaded with various payloads for remote injection. The payload used by the two researchers is CAN frames. All they need to do is to figure out what to do. Which CAN frame?
Berta and Claudio Caraccilo also established the OpenCANdb on-line CAN frame database, allowing users to obtain specific information based on a variety of vehicles. However, the database is still in the early stages of development and the content is still to be supplemented.
Bicho supports multiple attack payloads and can be used to point to any CAN-enabled vehicle, regardless of the manufacturer or specific vehicle model. Each of these payloads can be associated with SMS commands from anywhere.
Berta explained that the only limitation is everyone’s imagination and the attack surface of the target car. The wider the vehicle is on the CAN bus, the wider the scope of Bicho’s application. Some cars even expose light control, throttle position, and brakes on the bus, which allows the attacker to remotely control these.
At the Hack in the Box conference, the two researchers will demonstrate a new feature that proves that the attacker is fully capable of remotely shutting down the car ECU (Electronic Control Unit) computer and causing the vehicle to stop operating. Bicho can also be configured to perform certain condition detections, such as automatically executing an attack payload when the target vehicle approaches a given GPS position, exceeds a set speed, or falls below a set fuel level.
Bicho accesses the CAN bus through the OBD-II port on the vehicle, which is usually located under the vehicle’s steering wheel. Potential attackers must first physically reach the target vehicle to use this hardware back door.
Source: conference.hitb.org