The Discreet Threat of Wpeeper: A Backdoor Targeting Android Devices

A sophisticated Android backdoor known as “Wpeeper” has abruptly ceased activity after a short but potent campaign, sparking alarm within the cybersecurity community. Researchers at XLab, who uncovered the operation, discovered Wpeeper masquerading as legitimate-looking apps on the popular third-party app store UPtodown. The malware used a cunning, multi-layered evasion strategy to establish control over infected devices before mysteriously going dark.
Unveiling Wpeeper
Wpeeper is a backdoor Trojan with typical features such as collecting sensitive information from devices, managing files and directories, and executing commands remotely. However, Wpeeper distinguishes itself through its intricate network operations, showcasing the sophisticated craftsmanship of its creators. Its capabilities include:
- A multi-level Command and Control (C2) architecture using compromised WordPress sites to obfuscate the true C2 server.
- Session-specific requests using HTTPS to secure network traffic.
- AES-encrypted commands with elliptic curve signatures to prevent unauthorized access.
Origin and Distribution
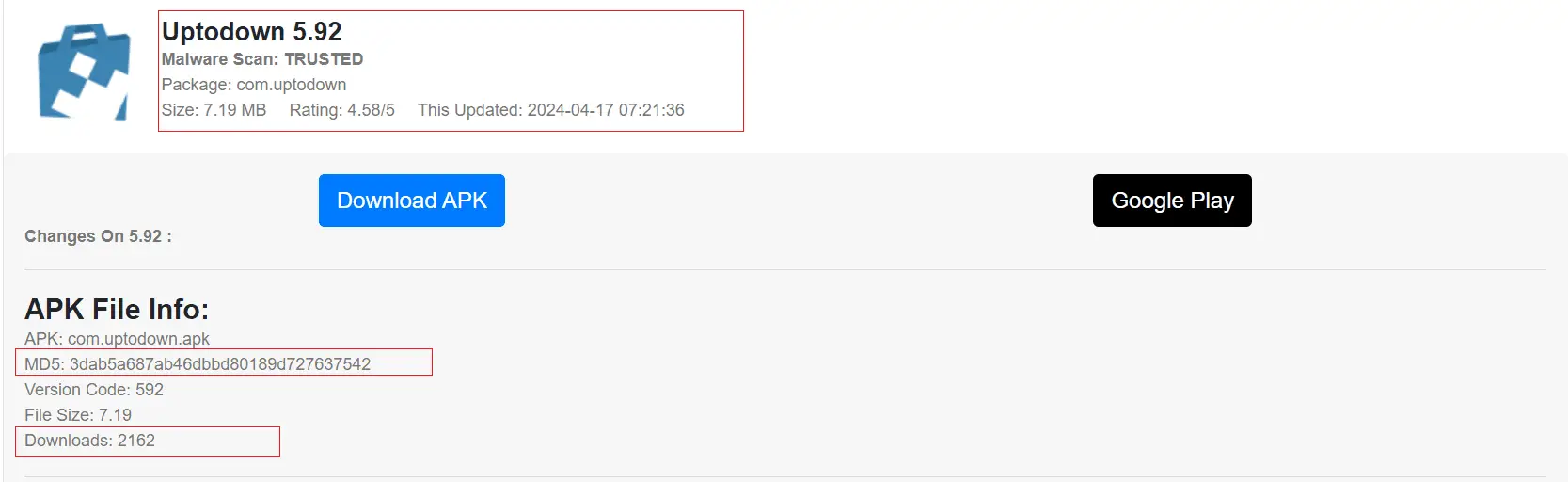
APK Installation Numbers | Image: XLab
The origin of Wpeeper can be traced back to repackaged applications in the UPtodown Store, a popular third-party app marketplace similar to Google Play. Attackers subtly embedded a small code snippet into legitimate APK files to facilitate the download and execution of the malicious ELF. This minimal intrusion means that even modified APKs remain undetected on platforms like VirusTotal.
In-Depth Analysis of Wpeeper
Technical examination of Wpeeper reveals its methods for managing commands and communicating with C2 servers:
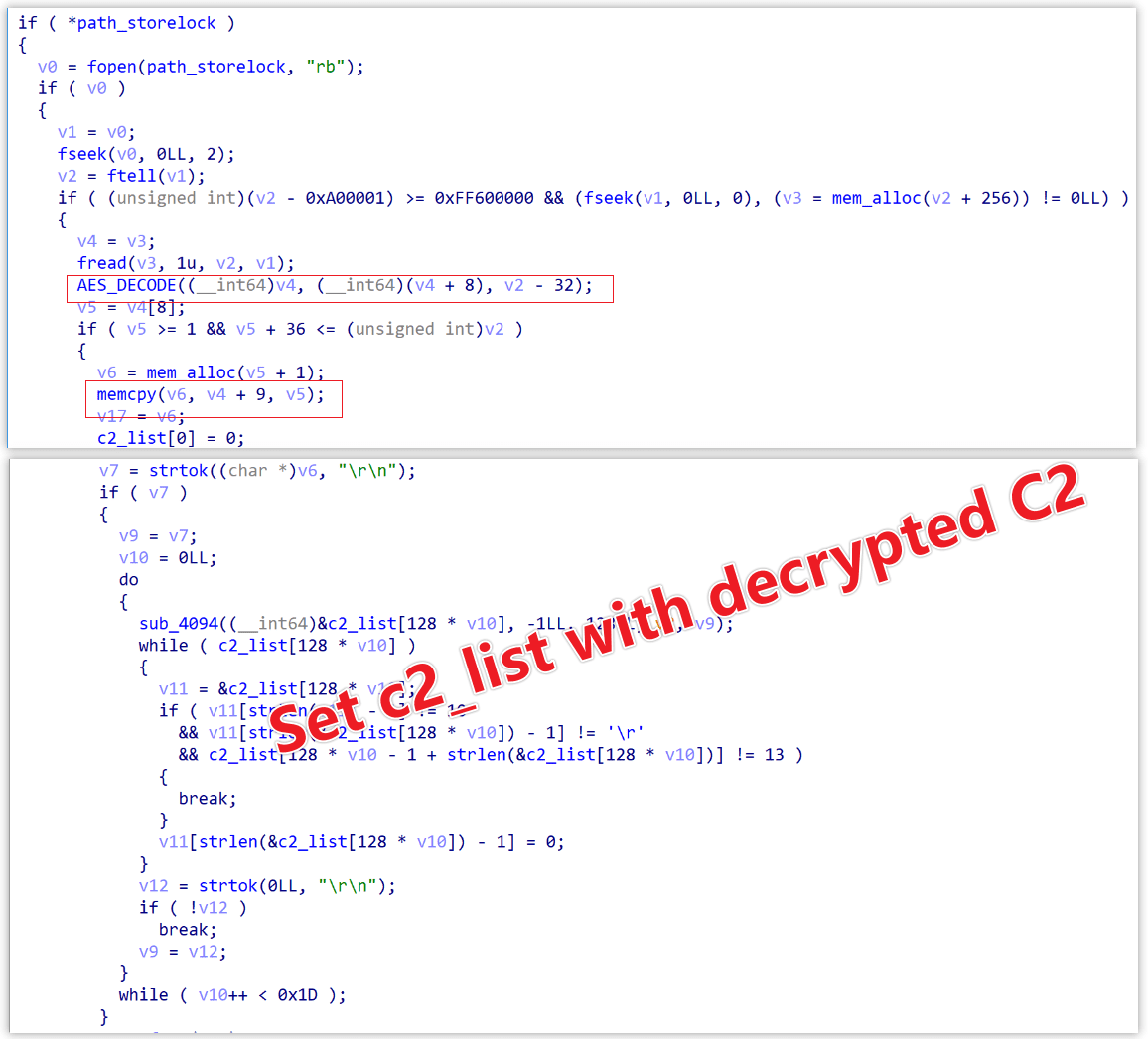
Source 2: store.lock | Image: XLab
- ELF Functionality: When executed, Wpeeper checks for a configuration file named
store.lockwhich contains essential data such as C2 server addresses and operational parameters. If not found, it proceeds to create this file using data encoded within the malware itself. - Command Management: Wpeeper supports various operations from device information collection to self-destruction, reflecting a wide range of capabilities designed to provide comprehensive control over compromised devices.
The Mystery: Why the Sudden Stop?
On April 22nd, the entire network fell silent. Download servers ceased providing Wpeeper, C2 relay sites went offline, and astonishingly, infected devices were remotely instructed to delete the malware. XLab researchers are left with possibilities:
-
Foiled Mission: The discovery of the campaign may have forced the attackers to cut their losses, abandoning this initial attempt to control devices for plans.
-
The Ultimate Disguise: By intentionally disappearing, Wpeeper may aim to fool antivirus AI systems into “learning” that its signature is benign. If this tactic succeeds, infected devices could essentially go invisible, creating a hidden army of compromised smartphones ready to be reactivated at will.
While direct data on Wpeeper’s spread is scarce, available information suggests thousands of installations, but not widespread propagation. The analysis of domain resolution counts and other online footprints offers some insight into the malware’s distribution and reach.
Conclusion
We urges Android users who have recently downloaded or updated apps from UPtodown to be extra cautious. Stay on the lookout for unusual activity like increased battery drain, unexpected data usage, or strange app behaviors. The threat of Wpeeper may have faded for now, but its tactics underscore the ever-present risk to mobile device security.





