The Escalating Threat of the EV Code Signing Certificate Black Market
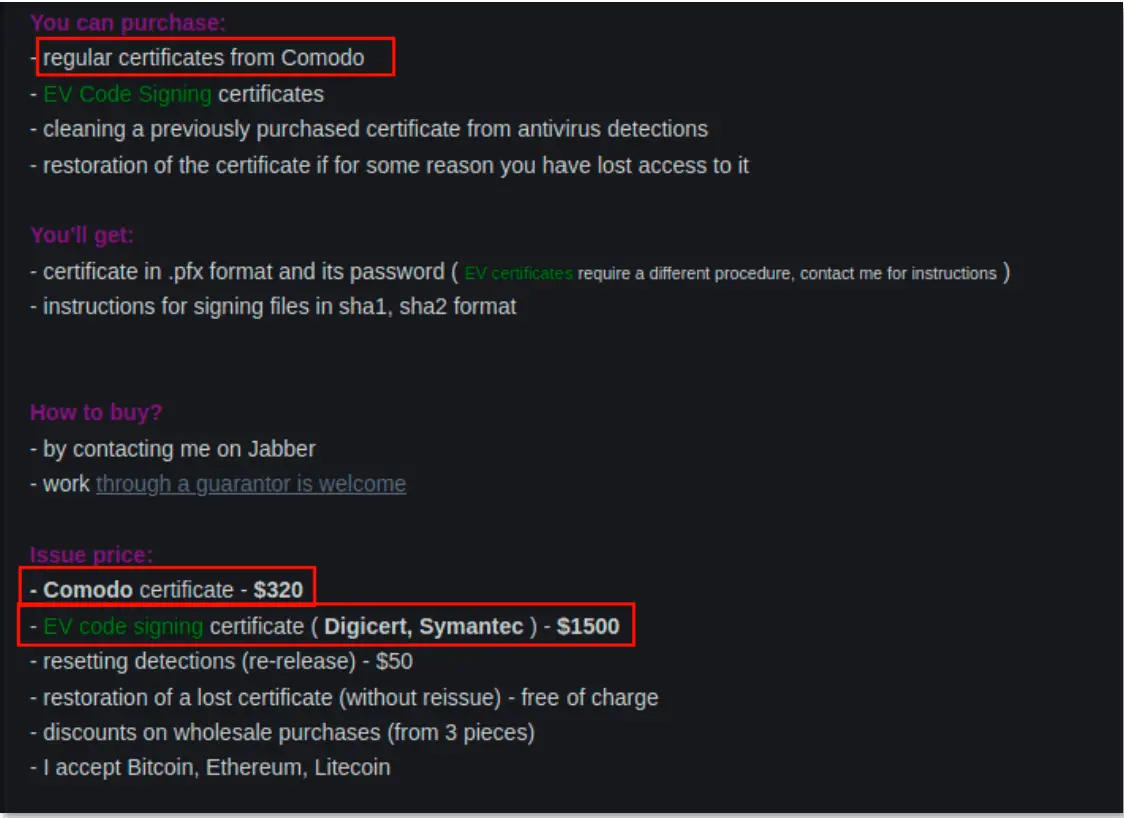
The cybersecurity landscape is facing a growing threat from the illicit trade of Extended Validation (EV) code signing certificates, as revealed in a recent report by Intrinsec. These certificates, designed to establish trust and authenticity for software, are being exploited by cybercriminals to bypass security measures and deceive users.
The report highlights the thriving underground market for EV certificates, where prices range from $2,000 to $6,000 depending on factors like customization and delivery method. Cybercriminals are leveraging these certificates to sign malicious code, enabling them to evade detection by security software, gain administrative privileges, and trick users into trusting their malware.
The abuse of code signing certificates provides several benefits to attackers, including:
- Bypassing Security Measures: Signed code is more likely to bypass security features like Microsoft’s SmartScreen, which is designed to block untrusted software.
- Gaining Administrative Privileges: Signed malware can often gain elevated privileges on a system, allowing it to execute harmful actions without raising alarms.
- Deceiving Users: Users are more likely to trust software that appears to be signed by a reputable source, increasing the likelihood of successful attacks.
- Avoiding Detection: Code signing can lower the risk score assigned by antivirus programs, making it harder for security solutions to detect malicious software.
The methods used to obtain these certificates are concerning. Some threat actors impersonate legitimate companies or even register new ones solely for this purpose. The report also points to instances of stolen certificates being used, as in the case of NVIDIA’s 2022 breach.
The impact of this illicit market is significant. High-profile malware campaigns, such as QakBot and Grandoreiro, have successfully used EV certificates to distribute their malicious payloads. The report also details how North Korean APT group Kimsuky has employed stolen certificates in their espionage activities.
The report underscores the urgent need for enhanced security measures to combat this threat. Recommendations include stricter application whitelisting, thorough certificate validation, and employee training to recognize unsigned or maliciously signed code. Additionally, the report advises users to exercise caution when downloading software and to rely on official sources whenever possible.
The EV code signing certificate black market poses a serious challenge to cybersecurity. By understanding the tactics employed by cybercriminals and implementing robust security practices, individuals and organizations can better protect themselves against these evolving threats.





