At the Black Hat 2017 Security Conference held in London, the UK on December 7, 2017, two researchers from network security company enSilo, Tal Liberman and Eugene Kogan, described to us a new type of code injection technology. They will It is named “Process Doppelgänging”.
Process Doppelgänging is described as being able to work on almost all Windows operating systems, from Windows Vista to the latest Windows. In addition, because the use of Process Doppelgänging’s malicious software code will not be saved to the local hard disk (known as “fileless attack“), this makes the vast majority of popular security products and forensic tools currently on the market cannot detect this malicious software.
Researchers stated that they have tested Process Doppelgänging injection technology for various security products, including Windows Defender, Kaspersky Labs, ESET NOD32, Symantec, Trend Micro, Avast, McAfee, AVG, Panda, and even some advanced forensics tools (such as Internal memory card tool Volatility). The result is shocking, and none of these security products and forensics tools can detect malware that uses the technology.
Kaspersky Lab released a report on Monday that they discovered the first ransomware using this code injection technology, SynAck, last month. It should be noted that SynAck is not a new ransomware that has only recently emerged. The earliest time it was discovered dates back to September 2017, but recently discovered samples are using Process Doppelgänging technology.
There is no doubt that SynAck’s use of Process Doppelgänging technology is aimed at trying to bypass the detection of security products. This technology uses the NTFS mechanism of the Windows operating system to start malicious processes from transaction files so that these processes appear to be legitimate processes.
In general, to complicate the work of a malware analyst, malware developers often use custom PE packages to protect the original code of malware executable files. However, SynAck’s developers did not seem to do so, and they did not package the ransomware executable. However, they added a lot of obfuscated code to SynAck’s source code, which made it extremely difficult to analyze SynAck.
Before encrypting a file, SynAck retrieves all running processes and services and checks the hash of its name against a list of two hard-coded hash values (hundreds of combinations). If a match is found, it will try to terminate these processes or stop the service.
SynAck attempts to terminate programs related to virtual machines, office applications, script interpreters, database applications, backup systems, and game applications. Researchers believe that SynAc’s purpose is to grant itself access to valuable files used by these processes.
Like other ransomware, SynAck also collects basic information about the infected host, such as computer and usernames, operating system version information, etc., and then encrypts the target file using a randomly generated 256-bit AES key. After the file is encrypted, it will be appended with a random production extension.
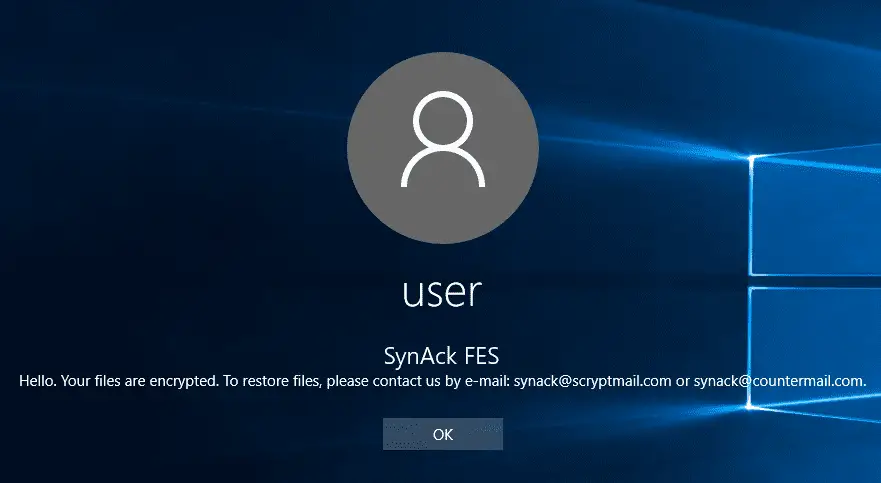
In addition, SynAck also clears the system-stored event log and can add custom text to the Windows login screen by modifying the LegalNoticeCaption and LegalNoticeText keys in the registry. Therefore, Windows will display messages from cybercriminals before users log in to their accounts.

Kaspersky concluded that they are currently monitoring several SynAck ransomware attacks in the United States, Kuwait, Germany, and Iran. This convinced them that the ransomware was specifically tailored to specific goals.