The Hidden Menace of Glupteba: Infiltrating Systems with UEFI Bootkits
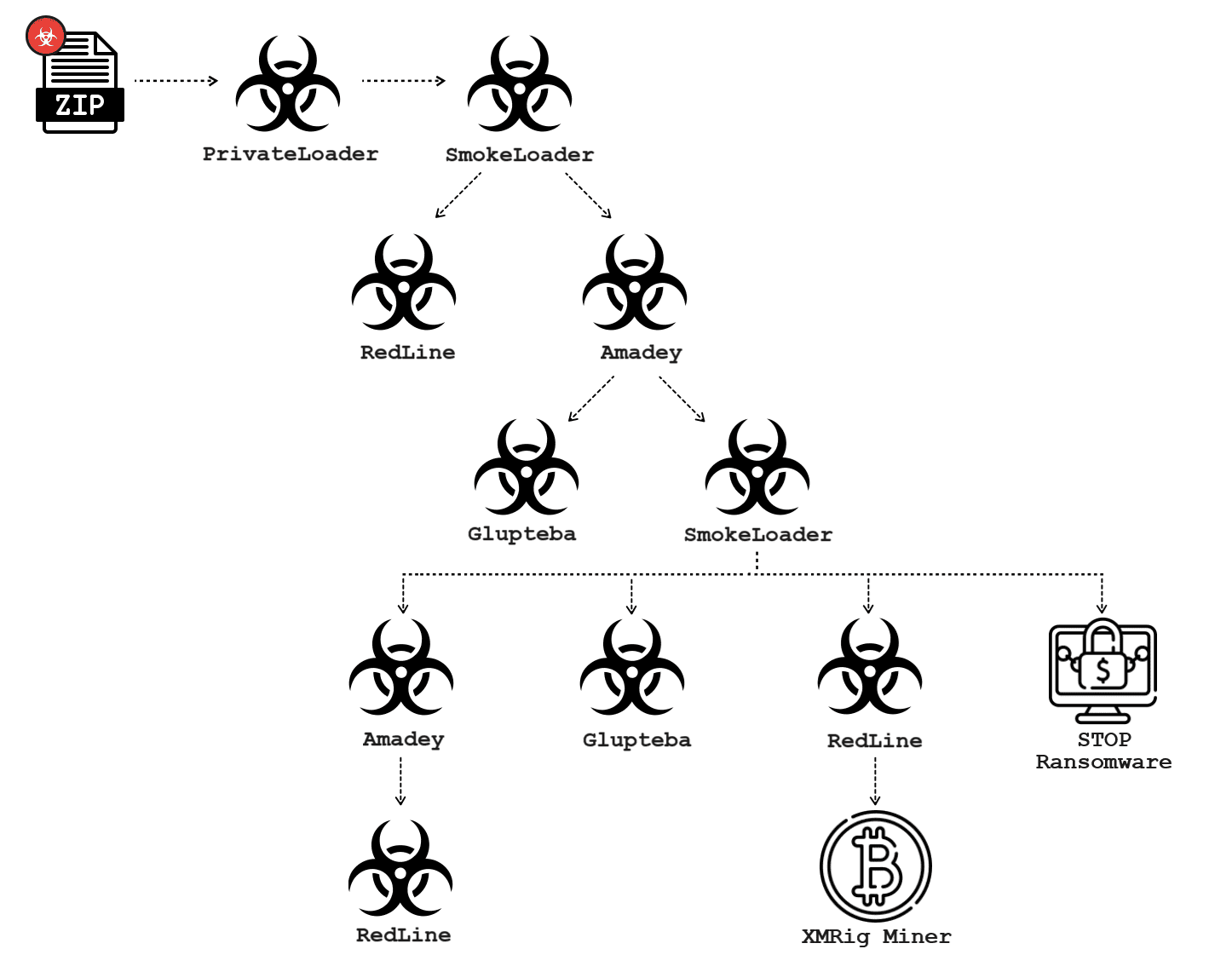
In the shadowy corners of the internet, a formidable malware known as Glupteba has been lurking, evolving, and spreading its tentacles across the globe. This sophisticated malware has carved a niche for itself in the cybercrime ecosystem, primarily driven by financial motives. With a history dating back over a decade, Glupteba’s recent activities have unveiled some of its most cunning and previously undocumented capabilities. Recently, Unit 42 from Palo Alto Networks revealed the infection chain of a new campaign that took place around November 2023.
Since its inception, Glupteba has undergone a remarkable transformation, constantly adapting and evolving to stay ahead of the curve. Initially conceived as a simple backdoor, it has now matured into a versatile botnet, wielding an arsenal of capabilities that can wreak havoc on unsuspecting victims.

Malware infection graph for a 2023 campaign that includes Glupteba | Image: Unit 42
Among its many hidden features, one stands out: the Unified Extensible Firmware Interface (UEFI) bootkit. This clandestine tool allows Glupteba to infiltrate and manipulate the very core of a system’s boot process, ensnaring it in a web of stealthy persistence that eludes detection and eradication.
At the heart of Glupteba lies its modular architecture. This design enables Glupteba to download and execute additional components or payloads, tailoring its attack to suit various scenarios and environments. From delivering payloads to stealing sensitive information and even enrolling infected systems in cryptomining botnets, Glupteba is a Swiss Army knife of cybercrime.
But how does Glupteba find its way into the digital battlegrounds of cyberspace? Enter the Pay-Per-Install (PPI) ecosystem, a thriving marketplace where cybercriminals converge to distribute their nefarious wares. This model, once a tool for legitimate advertising, has now been hijacked to propagate malware on a global scale, with operators like Ruzki facilitating the dissemination of threats like Glupteba.
Despite facing setbacks, such as Google’s intervention in 2021, Glupteba has resurfaced with renewed vigor, launching a widespread campaign that spans continents and industries. Using web-based distribution and large-scale phishing attacks, threat actors have orchestrated a chain of infection, ensnaring unsuspecting victims in their trap.
Central to Glupteba’s arsenal is its undocumented UEFI bootkit, a clandestine weapon that strikes at the very foundation of a system’s security. By implanting itself into the system firmware, Glupteba gains unparalleled control, rendering traditional security measures obsolete.
“Since its discovery in the early 2010s, Glupteba has evolved significantly and undergone a series of stealthy metamorphoses. This threat is particularly known for its elaborate infection chains that showcase its operators’ continuous developments and their attempts to evade traditional security measures,” the researcher concluded.





