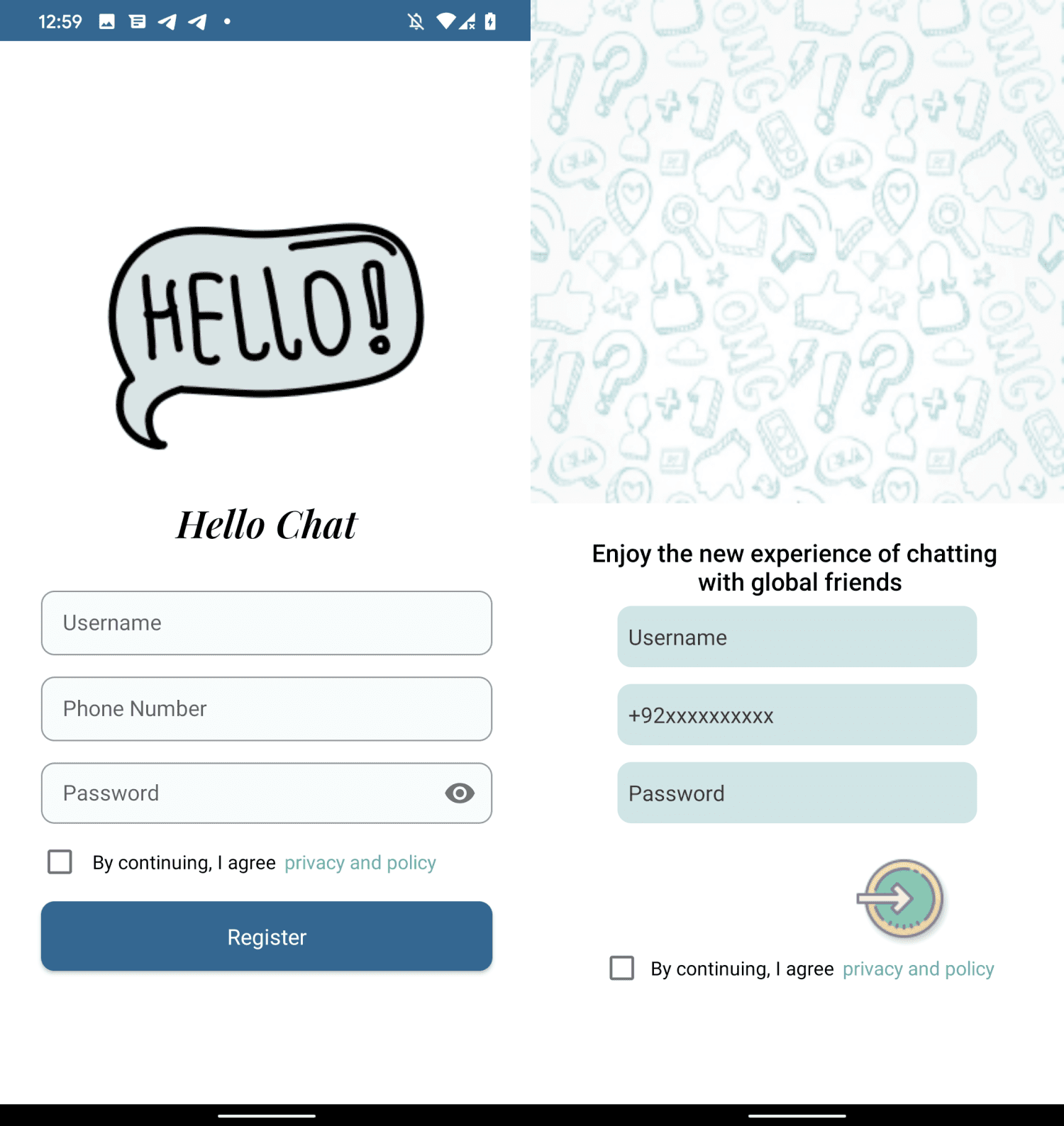
Login screen of Hello Chat (left) and MeetMe and Chit Chat (right) | Image: ESET
Recently, researchers from ESET have uncovered a startling revelation: a series of Android espionage apps bundled with the VajraSpy remote access trojan (RAT), all orchestrated by the elusive Patchwork APT group. These nefarious applications, concealed behind seemingly innocent facades, have infiltrated both Google Play and other online channels.
ESET’s journey into this espionage saga began in January 2023, when they stumbled upon a deceitful news app named “Rafaqat رفاقت” (which translates to “Fellowship” in Urdu). Further investigation unveiled a chilling truth: several other applications harbored the same malicious code as Rafaqat رفاقت. This treacherous web comprised twelve trojanized apps in total, six of which infiltrated Google Play, while the rest operated in the wild.

One of the most intriguing aspects of this campaign was the bait used by the threat actors. Researchers strongly believe that the Patchwork APT group employed a honey-trap romance scam to lure unsuspecting victims into downloading these malicious apps. Initial contact likely occurred on alternative platforms, with attackers feigning romantic in their targets before convincing them to switch to the trojanized chat applications. This modus operandi aligns with a broader trend observed in the world of cybercrime.
Among the trojanized apps, six managed to infiltrate Google Play between April 2021 and March 2023, reaching a combined total of over 1,400 downloads. These seemingly innocuous apps included “Privee Talk,” “MeetMe,” “Let’s Chat,” “Quick Chat,” “Rafaqat رفاقت,” and “Chit Chat.” While these apps appeared to offer messaging functionalities, they harbored the VajraSpy RAT code, concealed beneath the surface.
A key revelation was the commonalities shared by these apps. Most of them masqueraded as messaging applications, all bundled with the VajraSpy RAT code. Researchers noted striking similarities in the user login interface of “MeetMe” and “Chit Chat,” both of which were found to be signed by a unique developer certificate, suggesting a common creator.
Apart from those that infiltrated Google Play, another six trojanized messaging applications were discovered outside the Google Play ecosystem. Chronologically, “YohooTalk” was the first to emerge in February 2022, followed by “TikTalk,” “Hello Chat,” “Nidus,” “GlowChat,” and “Wave Chat” in subsequent months. These rogue apps, harboring the same malicious code, posed a significant threat to unsuspecting users.
VajraSpy, the covert operative within these trojanized apps, is a versatile and customizable RAT designed for data exfiltration. Its insidious nature lies in its adaptability, with its capabilities expanding based on the permissions granted to the host app. Among its espionage functionalities are the theft of contacts, files, call logs, SMS messages, and even the extraction of WhatsApp and Signal messages. Moreover, VajraSpy can record phone calls, capture images with the device’s camera, and execute a host of other intrusive actions.
The malicious code executed by these apps, identified as VajraSpy, was first encountered in March 2022 by QiAnXin, who attributed it to APT-Q-43. In March 2023, Meta published a report shedding light on the Patchwork APT group’s takedown operation and tactics, corroborating QiAnXin’s findings. In November 2023, Qihoo 360 independently associated these malicious apps with the VajraSpy malware operated by the Fire Demon Snake (APT-C-52), a new APT group. ESET’s analysis firmly linked VajraSpy to the Patchwork APT group, underscoring the coordinated nature of this campaign.
VajraSpy’s malicious functionalities vary based on the permissions granted to the host application. The trojanized apps can be categorized into three groups based on their capabilities:
- Group One: Trojanized messaging apps with basic functionalities, including contact theft, SMS interception, call log access, device location tracking, and more.
- Group Two: Trojanized messaging apps with advanced capabilities, including interception of WhatsApp, WhatsApp Business, and Signal communication, along with notifications and chat message interception.
- Group Three: Non-messaging applications, with Rafaqat رفاقت as the prime example, having limited capabilities compared to other trojanized apps.
The Patchwork APT group’s espionage campaign serves as a stark reminder of the evolving tactics employed by cybercriminals. Social engineering remains a potent weapon, with attackers constantly devising new ways to deceive and infiltrate. As the battle against cyber threats continues, vigilance is paramount. Users must exercise caution when clicking on links and downloading applications.