Malware attributions
Cyberattack has become a battleground for not just companies and individuals, but also geopolitical entities. A striking example of this is the emergence and evolution of the Gaza Cybergang, a sophisticated cyber espionage group with a focus on Palestinian entities and Israeli targets. SentinelLabs’ analysis delves into the complex world of the Gaza Cybergang, its operations, and the broader implications of its activities.
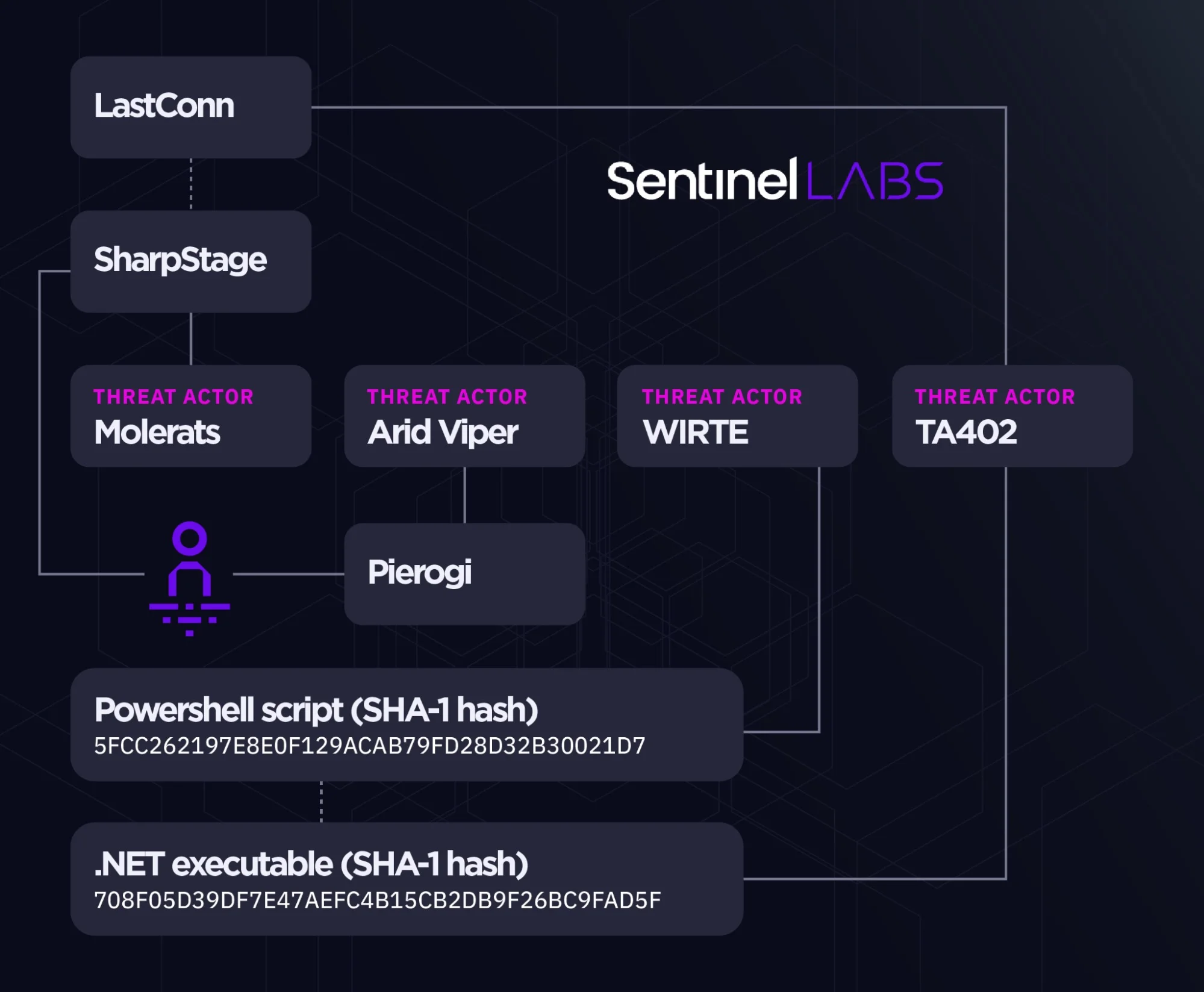
Active since at least 2012, the Gaza Cybergang is suspected of aligning with Hamas. Its primary focus has been on intelligence collection and espionage, targeting entities in Palestine and Israel. This group is not a monolith; it consists of several sub-groups including Gaza Cybergang Group 1 (Molerats), Group 2 (Arid Viper, Desert Falcons, APT-C-23), and Group 3 (behind Operation Parliament). Each group shares victims, tactics, techniques, and procedures (TTPs), and uses related malware strains, indicating a sophisticated and coordinated effort.

The Cybergang’s malware evolution is notable for its sophistication and adaptability. Key malware includes the Micropsia family and the recently upgraded Pierogi++ backdoor, first used in 2022 and continuing through 2023. Pierogi++ is an evolution of the older Pierogi strain, first observed in 2019, and is typically delivered via archive files or weaponized Office documents focused on Palestinian issues. The use of politically themed lures in Arabic or English further signifies the group’s targeted approach.
The Gaza Cybergang’s activities align with the broader tensions between Hamas and Fatah factions, especially in the backdrop of the Israel-Hamas war. While their targeting has remained consistent, focusing on Palestinian entities, the group’s evolution in terms of malware sophistication suggests a sustained and long-term investment in cyber espionage capabilities.
The overlap in malware and targeting among the Gaza Cybergang’s sub-groups post-2018 suggests a possible consolidation, involving the establishment of internal malware development hubs or external supply lines. This unification of efforts underlines the Cybergang’s strategic approach to cyber operations.
The activities of the Gaza Cybergang underscore the growing trend of cyber operations in geopolitical conflicts. Their focus on espionage, intelligence gathering, and the use of sophisticated malware signify a new era where digital warfare is as consequential as traditional warfare. The group’s persistent activities and evolving tactics highlight the necessity for sustained vigilance and cooperative cybersecurity measures.
The Gaza Cybergang represents a complex and evolving threat in the cyber domain, particularly in the Middle Eastern context. Their continuous investment in malware innovation, targeting of political entities, and the intricate interplay of their sub-groups, all point to a sophisticated and dedicated effort in cyber espionage.