The Invisible Threat: KV-botnet Infects SOHO Devices Worldwide
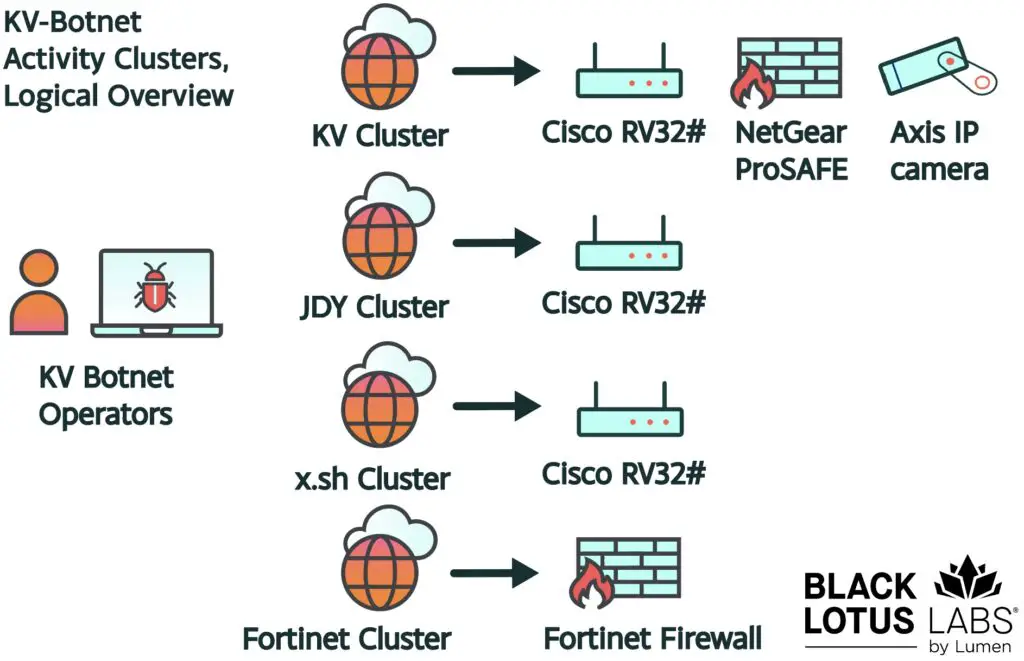
A new menace emerged, dubbed “KV-botnet,” this sophisticated malware network was identified by Lumen’s Black Lotus Labs, revealing a covert operation that had infected small-office and home-office routers and firewall devices globally.
The KV-botnet operates in the shadows, infecting small-office, home-office (SOHO) routers and firewall devices worldwide. These compromised devices, linked together in a clandestine network, serve as a covert data transfer network supporting various Chinese state-sponsored actors, including Volt Typhoon.
The KV-botnet spread its tentacles across the globe, chaining infected devices into a covert data transfer network. Its discovery prompted a swift response from cybersecurity teams, who observed significant behavioral changes in the malware’s operation post-exposure. The botnet’s resilience was tested as it underwent a phase of silence and restructuring, particularly within its secondary activity clusters.

The logical overview of the various activity clusters that comprise the KV-botnet | Image: Lumen’s Black Lotus Labs
In the weeks following its discovery, Lumen observed significant shifts in the botnet’s behavior. One such instance was the JDY cluster, which went silent for approximately fifteen days after initial detection. This lull coincided with the botnet operators’ efforts to re-establish critical elements, indicating a sophisticated response to external pressures.
Coinciding with the public revelation of the botnet’s existence, the FBI initiated a takedown operation. Targeting NetGear ProSAFE firewalls, the operation led to a flurry of activity from the threat actors, attempting to maintain their grip on compromised devices. Despite their efforts, the FBI’s intervention marked a significant setback for the KV-botnet.
The JDY cluster, primarily engaged in mass internet scanning, witnessed a decline in activity following the FBI’s actions. This pause in operations underscored the interconnected nature of the botnet’s various components and the ripple effects of law enforcement interventions.
Amidst the chaos, a new player emerged: the x.sh cluster. Operating with similar stealth and precision, this cluster posed yet another challenge for cybersecurity experts. Despite efforts to null-route its infrastructure, the x.sh cluster remained elusive.
With threats evolving at an unprecedented pace, vigilance and collaboration are more critical than ever. The demise of KV’s primary arm, coupled with the resilience of secondary clusters, serves as a stark reminder of the challenges ahead.





