The Silent Threat: Unmasking Undetected macOS InfoStealers
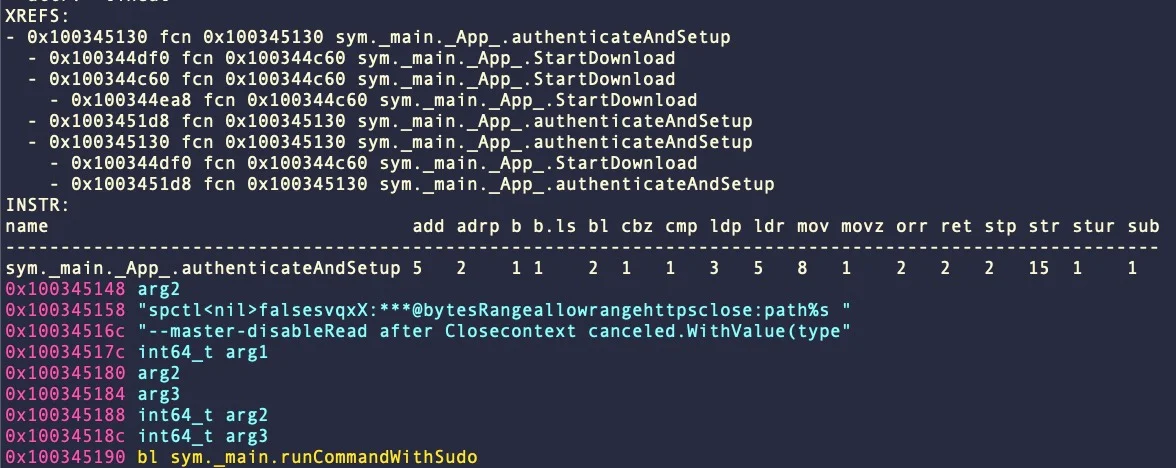
In the realm of cybersecurity, the rise of sophisticated infostealers targeting macOS has emerged as a significant threat. These advanced malware variants, like KeySteal, Atomic InfoStealer, and CherryPie, are adept at evading detection and have evolved rapidly, outpacing traditional security measures. Security researchers from SentinelOne detail these infostealers in recent their report.
The Rise of macOS InfoStealers
SentinelOne has been sounding alarms on the rise of these InfoStealers targeting macOS systems. These nefarious programs, including variants like Atomic Stealer, MetaStealer, and RealStealer, have evolved, continuously evading detection by conventional security measures.
The Chameleon Tactics of KeySteal
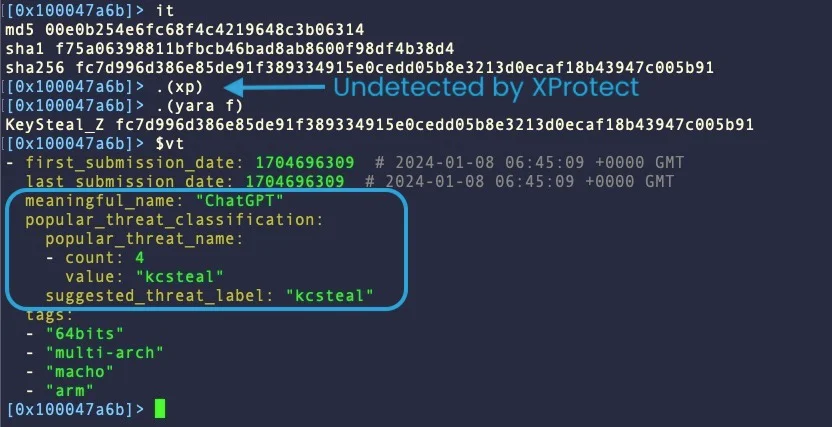
A recent sample of KeySteal uses the name ‘ChatGPT’ for its executable | Image: SentinelOne
KeySteal has undergone significant transformation. Initially appearing as a benign .pkg file, it now masquerades under innocuous names like “ChatGPT,” slipping past Apple’s XProtect and maintaining low detection scores on VirusTotal. Its primary weapon is its ability to stealthily extract Keychain information, deploying persistence mechanisms that remain hidden in plain sight.
Atomic InfoStealer: The Evolving Menace
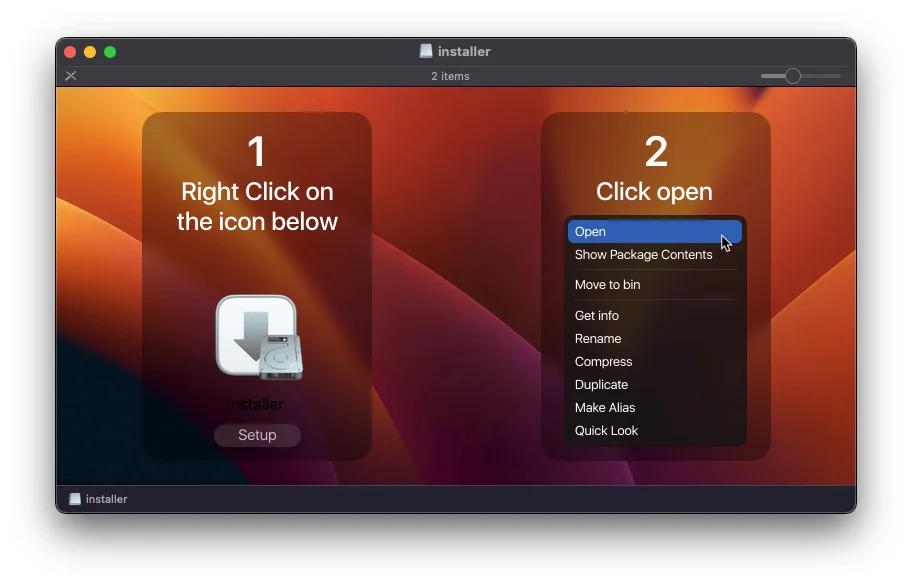
An Atomic Stealer installer instructing the victim to override Gatekeeper control | Image: SentinelOne
Similarly, Atomic InfoStealer showcases its adaptability. Written in multiple languages, including Go and C++, it exhibits anti-analysis techniques and VM detection capabilities. This stealer not only evades XProtect but also garners low detection rates on VirusTotal, indicating its high level of stealth and sophistication.
CherryPie: A Sweet Name for a Sour Purpose

macOS.CherryPie attempts to disable Gatekeeper with admin privileges Image: SentinelOne
CherryPie, another stealthy infiltrator, exemplifies the cross-platform threat. Despite being caught by Apple, many static engines lag in detection. It utilizes legitimate open-source tools to wrap its malicious intent, further complicating its detection and removal.
Conclusion
The ongoing battle against macOS InfoStealers like KeySteal, Atomic InfoStealer, and CherryPie highlights the need for a robust, multi-layered defense strategy. Relying solely on signature-based detection is no longer sufficient. As these threats evolve, so must our approach to cybersecurity, incorporating proactive threat hunting, enhanced detection rules, and an awareness of these evolving tactics.





