Image: Neroteam
In the digital era, small and medium-sized businesses have become increasingly reliant on the Internet for their daily operations. However, with this reliance comes a heightened vulnerability to cyber threats. The recent discovery of multiple security vulnerabilities in the Buffalo VR-S1000 BroadStation Pro VPN router underscores the critical need for vigilant cybersecurity practices.
The VR-S1000 router, a staple in many business networks for creating secure VPN connections between multiple locations, has been found to have significant security flaws in versions ‘2.37’ and earlier. These vulnerabilities not only pose a risk to the integrity of business networks but also open the door to potential data breaches and unauthorized access.
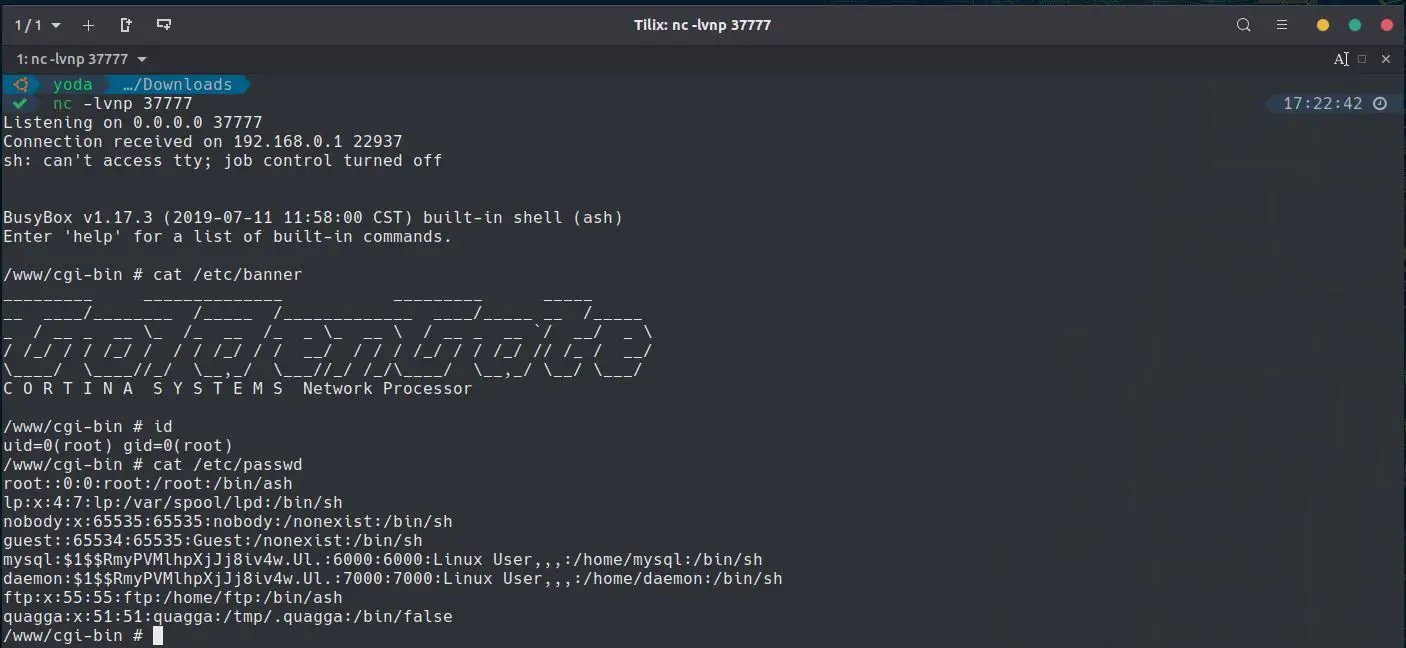
1. CVE-2023-45741 – OS Command Injection: This vulnerability represents a chink in the armor of the VR-S1000’s defenses. It allows an authenticated remote attacker to exploit the router by injecting arbitrary commands into the operating system. The root of this vulnerability lies in the unsafe implementation of the ping command, a fundamental network utility.

2. CVE-2023-46681 – SSH CLI Command Injection: This flaw lurks within the router’s command-line interface (CLI). It enables a local attacker with minimal privileges to perform a command injection attack, compromising the router’s core operating system.
3. CVE-2023-46711 – Use of Weak Hard-coded Cryptographic Key: This vulnerability exposes a weak link in the VR-S1000’s security, with hard-coded MD5crypt hashes for the mysql and daemon users, making the device an easy target for brute-force attacks.
4. CVE-2023-51363 – Sensitive Information Exposure: This vulnerability allows an unauthenticated attacker with network adjacency to access the router’s web management page and obtain sensitive information.
Three flaws including CVE-2023-45741, CVE-2023-46681, and CVE-2023-46711 were found by two security researchers Thomas Knudsen (@Knudsec) and Samy Younsi (@0xSamy_) from NeroTeam Security Labs. Also, the researchers published the technical details and proof-of-concept for these vulnerabilities.
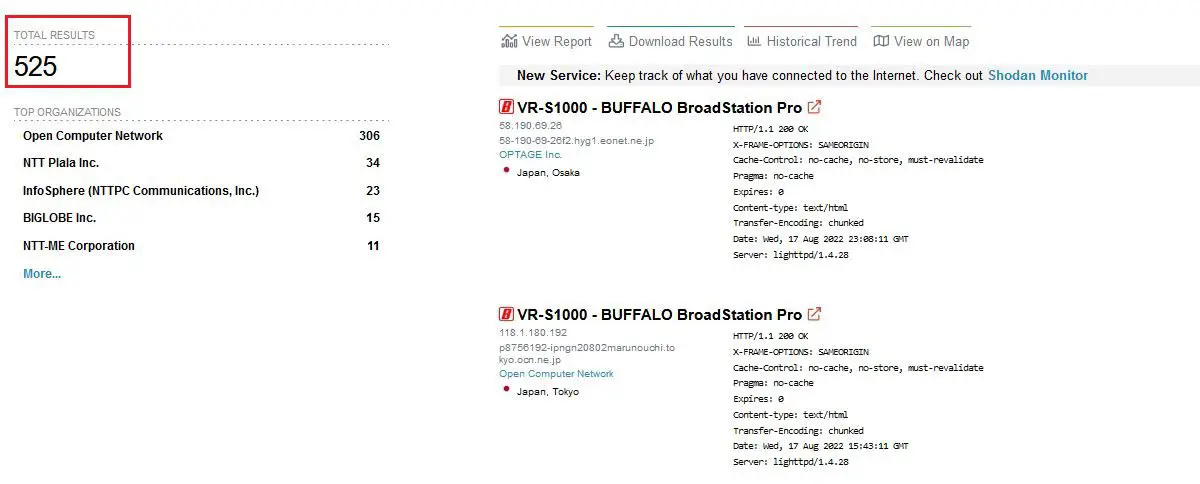
As of 15 Aug 2022, there were 525 Buffalo vr-s1000 BroadStation Pro devices exposed to the internet and were affected by the vulnerabilities discovered.
In response to these alarming vulnerabilities, Buffalo has issued a firmware update, version ‘2.42’. This update is not just a patch; it’s a vital shield fortifying the VR-S1000 against these vulnerabilities. Buffalo urges all users to update their devices to ensure the sanctity of their digital fortresses.