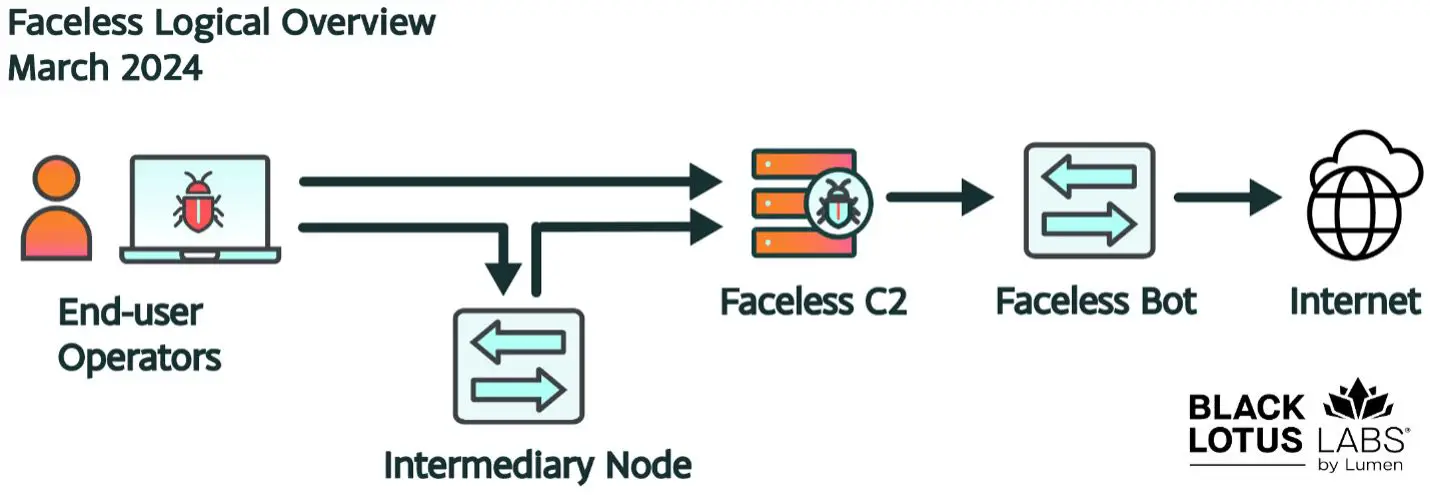
Logical Overview of Faceless Network | Image: Black Lotus Labs
Researchers at Lumen Technologies’ Black Lotus Labs have uncovered a newly updated version of the “TheMoon” malware, dating back to 2014. This updated strain of malware is being used to silently infect end-of-life (EoL) networking devices and hijack them into a large-scale proxy network known as “Faceless”. This illicit proxy service is a favorite tool of cybercriminals seeking to mask their activities online.
Despite operating under the radar, TheMoon has amassed an army of over 40,000 bots from 88 countries in just the first two months of 2024, forming the backbone of a notorious cybercriminal proxy service dubbed Faceless. The alarming growth rate of nearly 7,000 new users per week underlines the significant threat it poses.
TheMoon malware’s resurgence marks a critical development in the cybercrime ecosystem, as it has become the primary supplier to the Faceless proxy service. This service, rising from the ashes of the “iSocks” anonymity service, offers cybercriminals a means to anonymize their online activities, making it an invaluable asset for those seeking to evade detection. Through meticulous analysis, Black Lotus Labs has identified and disrupted a campaign targeting over 6,000 ASUS routers within 72 hours in early March 2024, underscoring the scale and precision of these attacks.

The technical sophistication of TheMoon malware is evident from its infection process, employing a multi-stage payload delivery system that ensures persistence and evasion from detection tools. It cleverly manipulates device capabilities to establish a command and control (C2) infrastructure, enabling the spread of the malware and facilitating the proxy service operations. Moreover, the malware’s integration with Faceless reveals a high degree of operational security, with infected devices being siloed to prevent detection and ensure the continuity of the proxy service.
This campaign’s impact extends beyond the mere infection of vulnerable devices. The Faceless service leverages this vast network of compromised devices to offer its users the ability to mimic legitimate ISP end-users, effectively bypassing standard network-based detection tools. This capability is particularly alarming given that 80% of Faceless bots are located in the United States, hinting at a targeted approach toward exploiting organizations within the country. The implications for data exfiltration and password spraying attacks, especially against the financial sector, are profound.
The Black Lotus Labs report is a stark reminder of the evolving threats in the cyber landscape, particularly as cybercriminals continually seek new methods to obscure their activities. The sophistication of TheMoon malware and its integration with the Faceless proxy service exemplifies the complex challenges faced by cybersecurity professionals. It also highlights the importance of ongoing vigilance, advanced network analytics, and international collaboration in combating these threats.