In the ever-evolving landscape of information technology, a recent study from RedHunt Labs has uncovered a startling reality – thousands of exposed and leaky cloud storage buckets, potentially posing a significant threat to data security across various sectors.
Cloud object storage buckets, akin to digital containers in the cloud, are fundamental in organizing and accessing data securely. However, these virtual repositories can become a nightmare for organizations if not properly secured. This vulnerability was the focus of a groundbreaking study using the in-house developed tool, BucketLoot, at BlackHat USA and MEA 2023. The goal was to identify and analyze misconfigured storage bucket instances across AWS, DigitalOcean, and GCP.
The study embarked on a vast scan, targeting approximately 170,000 instances across AWS, DigitalOcean, and GCP, utilizing the innovative capabilities of BucketLoot. This tool, designed for automated inspection of S3-compatible buckets, was configured to scan files up to 10 MB, focusing on textual data like configuration logs and code files.

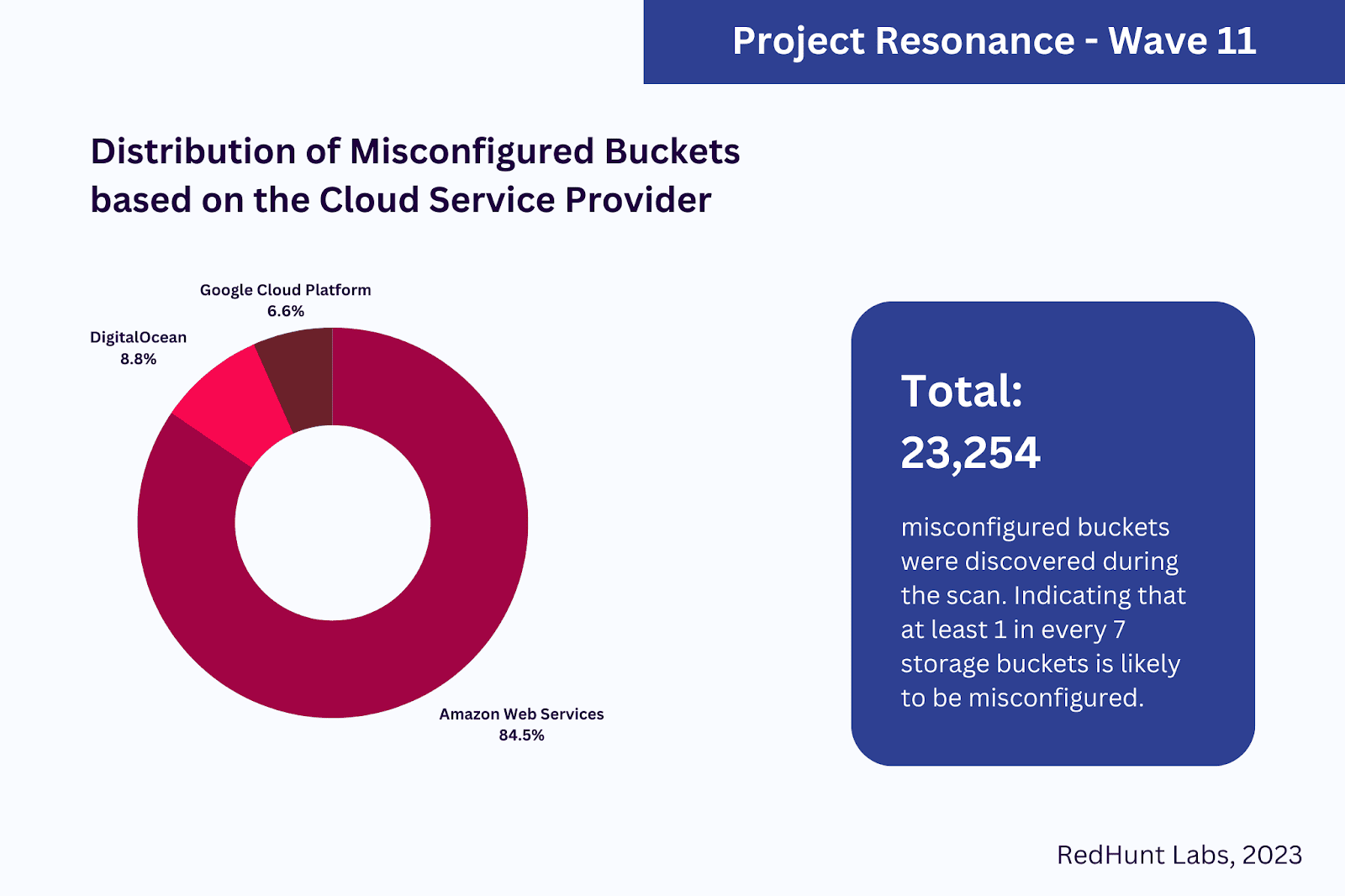
The results were alarming. The scan revealed over 23,254 misconfigured buckets, suggesting that 1 in every 7 buckets was likely vulnerable. These misconfigurations were not limited to individual owners but spanned across well-known companies, including a Biomedical Research and Development NPO. The exposure of sensitive data like medical records underscores the critical nature of this issue.
Furthermore, the study unearthed an astounding 13,425 secret exposures from these buckets. The most common were Google API keys, AWS Access Key IDs, and Amazon SNS Topic Disclosures. These exposures, particularly prevalent in AWS buckets, have the potential to facilitate actions like manipulating GCP services or interacting with AWS CLI, posing enormous risks to affected parties.
The research also focused on asset intelligence, discovering over 543 million URL occurrences, of which 160 million were unique. The findings included a range of domains and subdomains, revealing hidden endpoints and URLs that could be crucial for bug hunters and penetration testers.
The insights from this research led to three key recommendations for handling cloud object storage buckets:
- Proper Configuration of Security Settings: This includes setting correct access controls, permissions, and policies to prevent unauthorized access.
- Avoid Storing Secrets in Buckets: Sensitive data such as access keys and API tokens should be stored in dedicated secrets management solutions or secure key vaults.
- Regular Monitoring and Auditing: Continuous vigilance is essential to prevent security misconfigurations and ensure the safety of bucket contents.
This extensive study highlights the urgent need for improved security practices around cloud object storage buckets. The findings demonstrate the vast potential for data leaks and the importance of immediate action to secure these vital storage instances. As cloud storage continues to be an integral part of IT infrastructure, understanding and addressing these vulnerabilities is not just advisable – it’s imperative.