Thousands of Fortinet Devices Remain Exposed to RCE CVE-2024-23113 Vulnerability
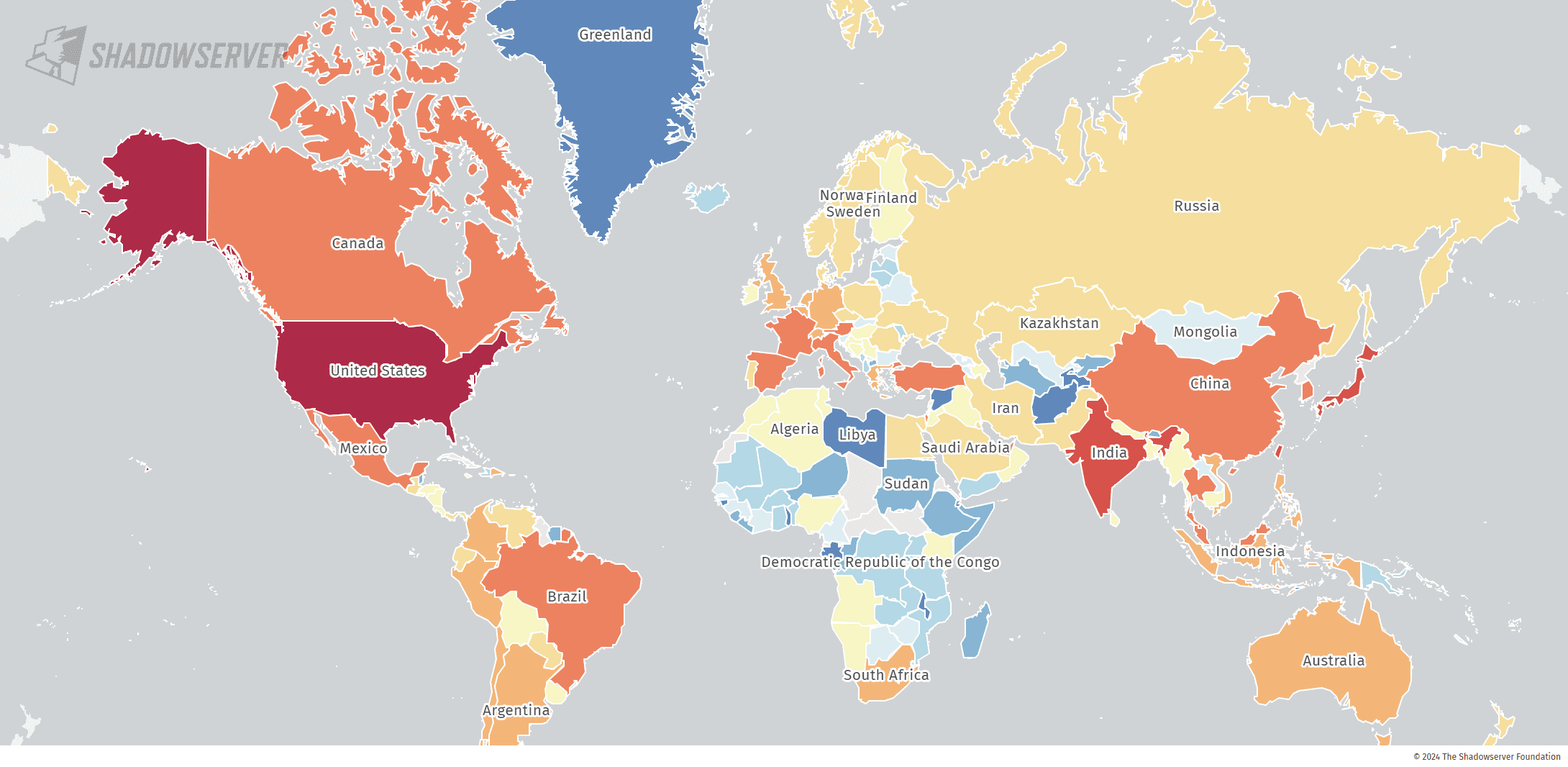
A recent report from the Shadowserver Foundation has revealed a concerning number of Fortinet devices remain vulnerable to a critical remote code execution (RCE) vulnerability, despite patches being available for months and active exploitation in the wild.
CVE-2024-23113, a pre-authentication RCE vulnerability affecting the fgfmd daemon, was first disclosed and patched by Fortinet back in February 2024. This flaw allows unauthenticated attackers to execute arbitrary code on vulnerable devices through simple attacks that require no user interaction.
Shadowserver’s scan on October 12th, 2024, identified a staggering 87,390 unique IP addresses still hosting vulnerable Fortinet devices. The US leads with the highest number of exposed devices (approximately 14,000), followed by Japan (5,100) and India (4,800).
We are now reporting in our feeds Fortinet IPs still likely vulnerable to CVE-2024-23113 (format string pre-auth RCE). This vulnerability is known to be exploited in the wild.
87,390 IPs found on 2024-10-12 scan. Top: US (14K), Japan (5.1K), India (4.8K)https://t.co/KRov0cOJev pic.twitter.com/ddipRXlBTL
— The Shadowserver Foundation (@Shadowserver) October 13, 2024
This vulnerability impacts a wide range of Fortinet products, including:
- FortiOS 7.0 and later
- FortiPAM 1.0 and higher
- FortiProxy 7.0 and above
- FortiWeb 7.4
Fortinet initially disclosed and patched the vulnerability in February 2024, urging administrators to update their systems to avoid exploitation. The company recommended removing access to the vulnerable fgfmd daemon from all interfaces as a critical mitigation measure, though this comes at the cost of limiting FortiGate discovery by FortiManager. Fortinet further suggested that administrators implement local-in policies to restrict FGFM connections to specific IP addresses. However, they stressed that this is only a mitigation, not a comprehensive solution, as the vulnerability could still be exploited from the allowed IP.
Despite these warnings, a significant number of devices remain unpatched, posing a continued risk to organizations worldwide.
Last week, the Cybersecurity and Infrastructure Security Agency (CISA) raised alarms, confirming that CVE-2024-23113 is actively being exploited by attackers in the wild. Shadowserver’s recent findings further underline the scale of this vulnerability, as thousands of Fortinet devices remain exposed. This widespread exposure puts critical infrastructure, businesses, and government organizations at risk of cyberattacks, especially since the vulnerability requires minimal effort to exploit.
Related Posts:
- Critical Alert: FortiOS Vulnerable to Remote Code Execution (CVE-2024-23113)
- Fortinet Faces Potential Data Breach, Customer Data at Risk
- Critical Fortinet Vulnerability Exploited: Hackers Deploy Remote Control Tools and Backdoors
- PoC Exploit Released for Critical Fortinet FortiClient EMS Flaw
- CVE-2023-48788 Exploited: Researcher Details Cyberattacks on Fortinet EMS





