
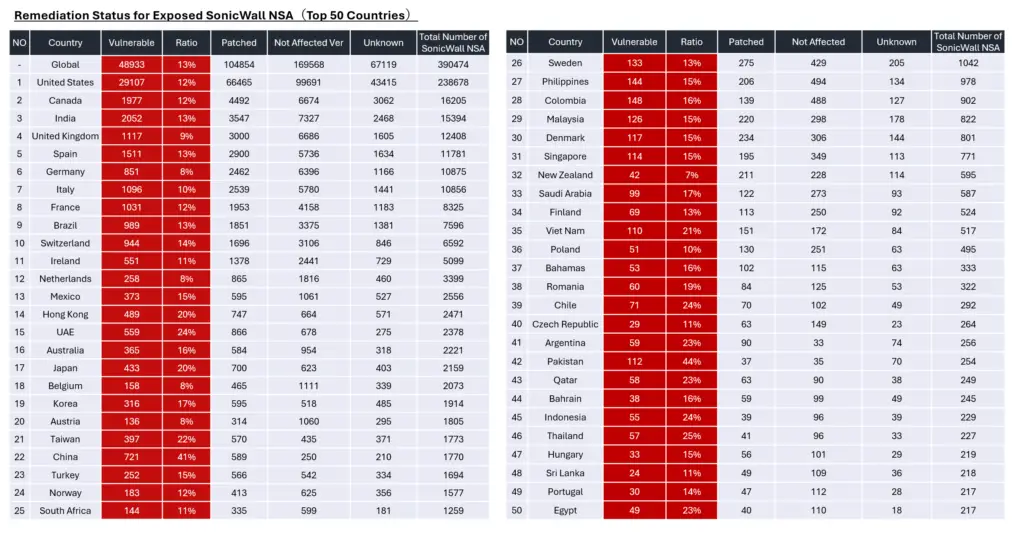
In September 2024, a critical vulnerability in SonicWall NSA devices, tracked as CVE-2024-40766, was disclosed. Since then, threat actors Akira and Fog have reportedly exploited this flaw to infiltrate organizations worldwide. According to Yutaka Sejiyama, a threat researcher at Macnica, over 100 companies have likely fallen victim to these ransomware groups via this vulnerability, with at least 48,933 devices still exposed as of late December 2024.
Sejiyama’s investigation linked SonicWall devices to 46% of organizations listed as victims on the leak sites of Akira and Fog, significantly higher than the 5% seen among other ransomware groups. “This trend has continued from September through December. Depending on the period, this figure can exceed 50%,” Sejiyama notes.
While direct attribution remains challenging due to the absence of a public proof-of-concept (PoC) and SonicWall’s limited disclosure on the vulnerability’s exploitation mechanisms, the circumstantial evidence is compelling. “SonicWall has not provided sufficient information about the potential impact of the vulnerability when exploited, and no PoC has been publicly released, leaving many details unclear,” explains Sejiyama.
Despite the patch for CVE-2024-40766 being available, remediation efforts have been slow. “As of December 24, 2024, at least 48,933 SonicWall devices remain vulnerable,” warns Sejiyama. This sluggish response highlights systemic challenges in vulnerability management, particularly in certain regions. Poor patch adoption in parts of Asia and a general slowdown after the initial patch release mirror trends observed in other high-profile vulnerabilities.
Through careful reconnaissance and exploitation of unpatched SonicWall NSA devices, attackers can gain unauthorized access, steal credentials, and launch ransomware attacks. Akira and Fog have likely diversified their methods to avoid detection, leveraging the vulnerability to infiltrate networks and escalate their foothold.
The lack of decisive action could prolong the lifecycle of this vulnerability as an attack vector for Akira, Fog, and potentially other groups. “The number of victims leaked by Akira and Fog has significantly increased, which may be contributing to their growing success,” Sejiyama concludes.
As 13% of global public servers remain vulnerable, the defenders must prioritize collaborative efforts to mitigate risks and address the exploitation of CVE-2024-40766.
Related Posts:
- Fog Ransomware Group Shifts Focus: Financial Sector Now in Crosshairs
- Fog & Akira Ransomware Exploit Critical Veeam RCE Flaw CVE-2024-40711 After PoC Release
- SonicWall Issues Urgent Patch for Critical Firewall Vulnerability (CVE-2024-40766)
- SonicWall Confirms Critical CVE-2024-40766 Vulnerability Actively Exploited in the Wild
- Akira Ransomware Exploit CVE-2024-40766 in SonicWall SonicOS