Threat Actor Deploys LummaC2 and Rhadamanthys Stealers in Attacks on Taiwanese Facebook Accounts
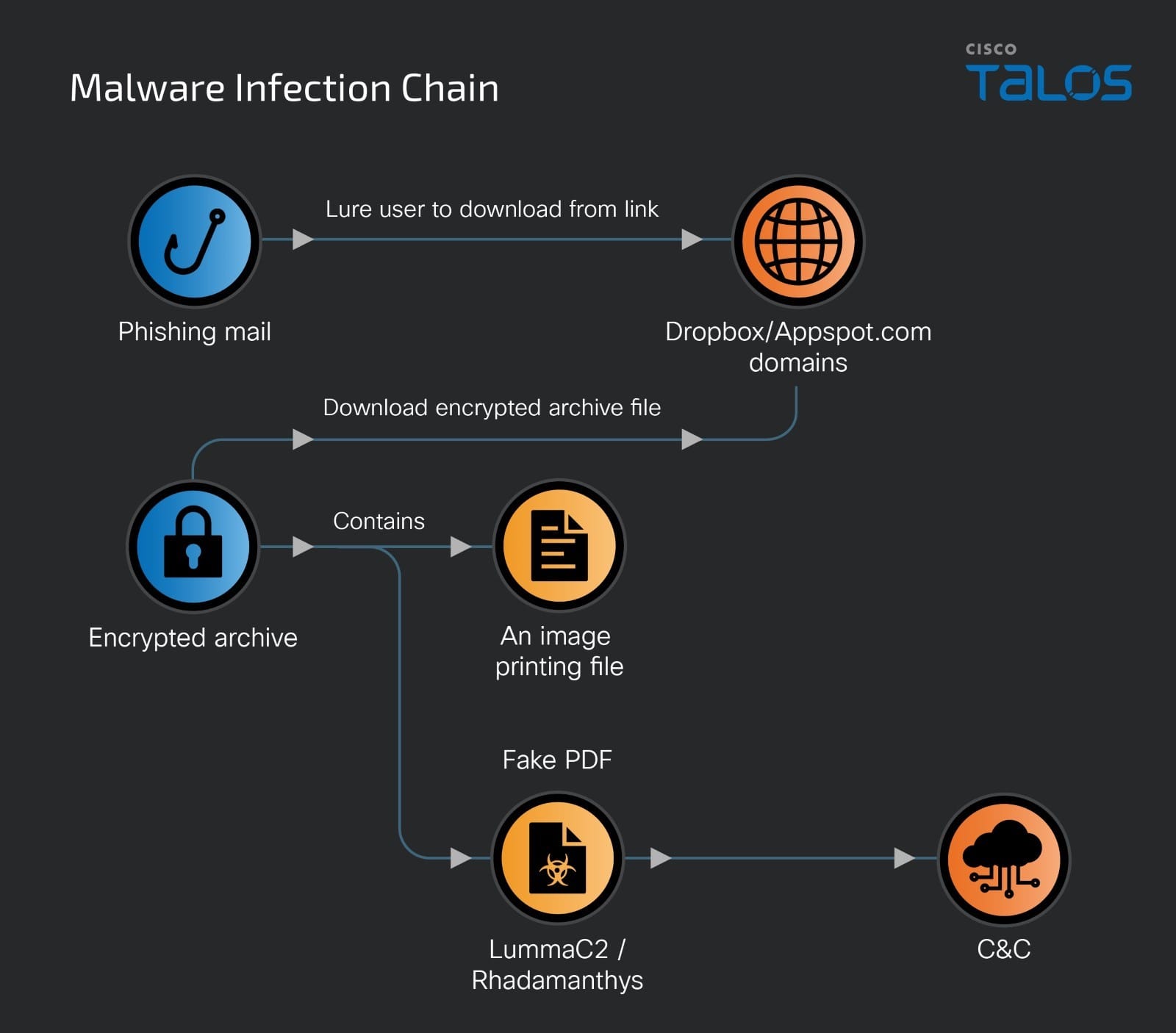
A new phishing campaign, tracked by Cisco Talos, has been targeting Facebook business account users in Taiwan since at least July 2024. This campaign is specifically designed to lure victims into downloading malware by posing as copyright infringement notices, a tactic that has proven effective in evading detection and engaging victims.
The phishing emails are written in traditional Chinese, suggesting they are tailored for users in Taiwan and Hong Kong. Each email claims to be a notice from a company’s legal department, alleging copyright infringement and threatening legal action if the infringing content is not removed. Cisco Talos reports, “The emails claim that the company’s legal representatives have issued a notice to a Facebook page administrator alleging copyright infringement due to the unauthorized use of their images and videos for product promotion.” The messages warn recipients to remove the infringing content within 24 hours to avoid further legal consequences.
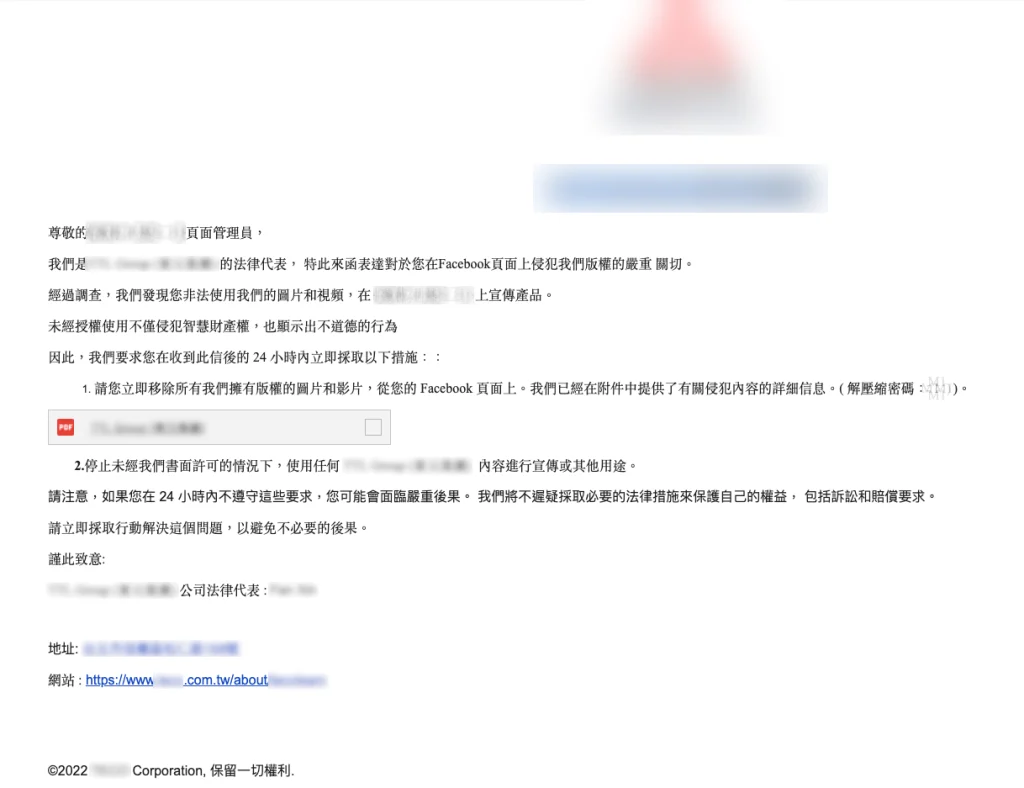
Phishing email impersonating a well-known industrial motor manufacturer.
The email attachments contain malicious executables disguised as PDFs with filenames such as “IMAGE COPYRIGHTED.exe” and “[Redacted]的影片內容遭到侵犯版權.exe” (translated: “[Redacted]’s video content has been copyright infringed.exe”). The filenames often include names of well-known companies to increase credibility, showing that the threat actors conducted thorough research to maximize the effectiveness of their attack.
Upon downloading and running the fake PDF executable, victims unknowingly launch an information stealer, either LummaC2 or Rhadamanthys, which is designed to exfiltrate sensitive data. Once executed, the malware “collects the victim’s credentials and data, sending them back to the C2 server,” Cisco Talos explains. The malware’s loaders employ techniques to evade detection, such as injecting the malicious payload into legitimate processes like “dialer.exe” and utilizing obfuscation methods.
The infection process involves a series of redirections. When victims click the download link, they are initially connected to a Google Appspot domain, then redirected to a short URL, and finally to Dropbox, where the malicious RAR archive is hosted. According to Cisco Talos, “The actor is using the third-party data storage service as a download server to deceive network defenders” and obscure the attack’s origin.
LummaC2 and Rhadamanthys, the information stealers used in this campaign, are capable of harvesting a range of data, including system details, credentials, cryptocurrency wallet information, and browser cookies. Rhadamanthys, in particular, is known for expanding its file size to evade detection. “This significant increase in file size is intended to bypass heuristic and signature-based detection mechanisms,” making it more challenging for security solutions to detect and stop the malware.





