Overview of recent UAC-0099 activities
In the digital battlegrounds of modern warfare, a new adversary has emerged, codenamed ‘UAC-0099’. This nefarious cyber threat actor has been actively targeting Ukraine since mid-2022, according to insights from the Deep Instinct Threat Lab and Ukrainian CERT advisories.
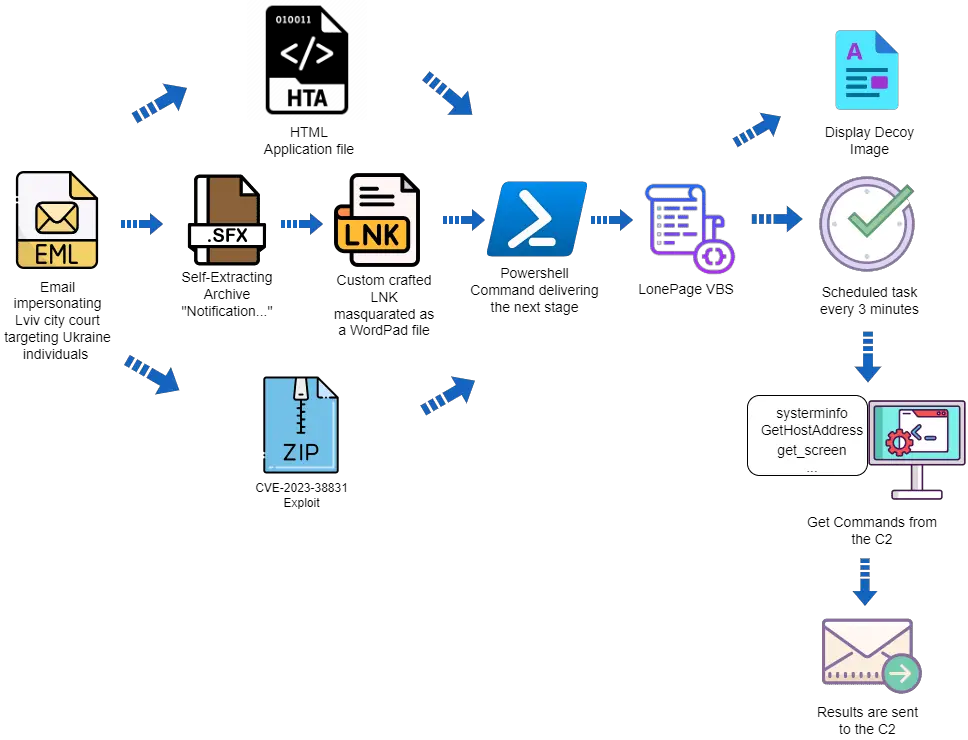
UAC-0099’s methods are a testament to their cunning and technical prowess. Leveraging a vulnerability identified as CVE-2023-38831, they’ve orchestrated attacks on Ukrainian employees of companies based outside Ukraine. These attacks are not just isolated incidents but part of a broader, more sinister campaign.
One of the most devious tactics employed by UAC-0099 involves sending emails impersonating official entities, such as the Lviv city court. These emails, complete with malicious attachments, are designed to deceive victims into executing harmful files. The attack vectors are diverse, ranging from RAR SFX with LNK files to HTA files, each carrying its unique deceptive methodologies.

At the heart of UAC-0099’s arsenal lies the LonePage malware, a sophisticated VBS script capable of creating hidden processes and communicating with control servers. This malware can execute commands remotely, sending back data to the attackers and maintaining a persistent threat.
The activities of UAC-0099 are not static; they evolve, adapting to countermeasures and exploiting new vulnerabilities. Their use of the WinRAR CVE-2023-38831 vulnerability, discovered by Group-IB, highlights their ability to quickly capitalize on emerging security gaps.
The threat posed by UAC-0099 is a stark reminder of the ever-evolving landscape of cyber warfare. For Ukraine, and indeed for global cybersecurity, understanding and anticipating the strategies of such actors is crucial. Vigilance, combined with swift adoption of security updates and a keen eye for suspicious emails, remains our best defense against the shadowy maneuvers of UAC-0099.