
A recent report from CloudSek’s Threat Researcher Team exposes a highly sophisticated phishing campaign that targets popular YouTube channels through fraudulent brand collaboration offers. Threat actors behind this scheme employ a blend of social engineering tactics and advanced malware techniques to compromise victims, stealing sensitive data and potentially taking over their accounts.
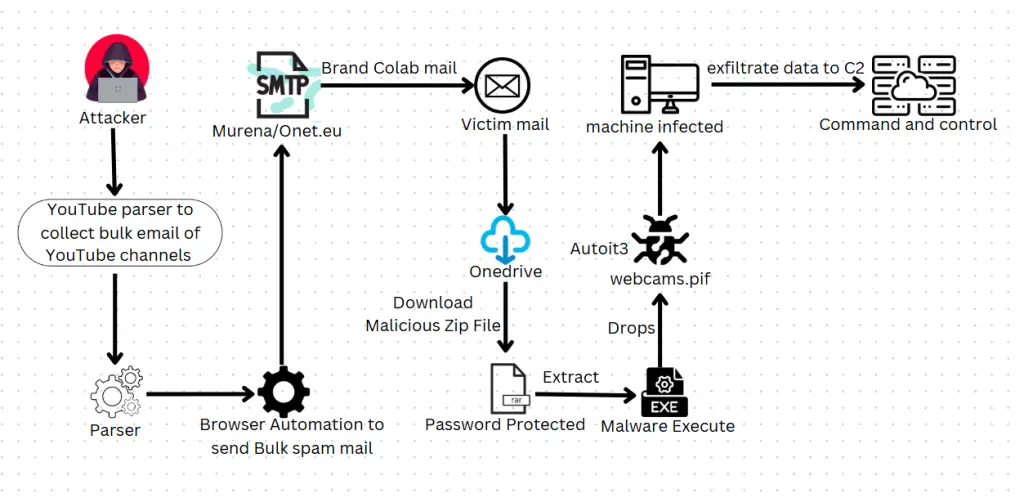
The attackers initiate their scheme by impersonating well-known brands and offering lucrative collaboration deals to YouTube creators. According to CloudSek, these emails are crafted to appear as genuine business proposals, often including compensation structures based on subscriber counts. “The attackers are leveraging trusted brand names and professional collaboration offers as a cover to distribute malicious attachments,” the report highlights.
The phishing emails typically include a link to a OneDrive-hosted ZIP file containing promotional materials and agreements, protected by a password. However, these files are traps: hidden within them are malicious payloads that infect the recipient’s system once extracted.
The threat actors execute their campaign in several well-coordinated stages:
- Initial Contact: Using spoofed or compromised email addresses, the attackers send brand collaboration proposals, convincing YouTube creators to download a ZIP file.
- Malicious Payload Delivery: The ZIP file contains a secondary compressed file with password protection. Extracting this reveals files such as “Digital Agreement Terms and Payments Comprehensive Evaluation.exe,” which deploys malware.
- System Compromise: Once executed, the malware installs on the victim’s device, enabling attackers to steal browser credentials, cookies, clipboard data, and other sensitive information.
The report also notes that the attackers use automation tools, such as Browser Automation Studio and YouParser, to gather email addresses from YouTube channels and send bulk phishing emails, increasing their reach and efficiency.
To bypass antivirus detection, the attackers employ multi-layered compression and obfuscation techniques. For instance, malware is disguised as legitimate files like “webcams.pif,” an AutoIt script, which then deploys additional malicious binaries such as RegAsm.exe for persistence.
CloudSek’s analysis reveals that these payloads communicate with Command and Control (C2) servers to exfiltrate stolen data. The malware also checks for antivirus processes and attempts to evade detection by disabling them using batch scripts.
The campaign appears to have a global scope, with YouTube creators being the primary targets. “Recipients are lured into downloading the attached files, believing they are legitimate business offers,” the report states. The attackers utilize stolen data for credential harvesting, account takeovers, and further lateral movement, potentially compromising multiple accounts and systems linked to the victims.
CloudSek researchers identified several key indicators of the attack, including:
- Malicious domains such as vm95039.vps.client-server.site:27105.
- Files like webcams.pif and Larger.bat, used to automate malicious processes.
- Email spoofing infrastructure, including over 340 SMTP servers and 26 SOCKS5 proxies, facilitating anonymity and scalability.
By exploiting trust in recognized brands, threat actors are not only stealing data but also undermining the credibility of legitimate partnerships.
Related Posts:
- Security Alert: Hackers Can Access Google Accounts Without Passwords
- Hacker forged Windows 11 upgrade website to trick users to download the virus
- Cryptocurrency Malware: The Hidden Threat Lurking on YouTube
- Hackers changed and removed a lot of popular music videos on Youtube
