
Trend Micro Research has revealed a significant evolution in the behavior of the Gafgyt malware (also known as Bashlite or Lizkebab), which is now targeting misconfigured Docker Remote API servers. This marks a shift from Gafgyt’s traditional focus on vulnerable IoT devices.
The report reveals that threat actors exploit publicly exposed and misconfigured Docker Remote API servers to deploy Gafgyt malware. Attackers create Docker containers using legitimate images, such as the lightweight “alpine” image, and leverage techniques like privilege escalation to gain control over host systems. According to the report, “The attacker uses this command to mount the host’s root directory (/:) to the /mnt directory inside the container. This means the container can access and modify the host’s filesystem as if it were part of its own filesystem. By doing so, the attacker can escalate privileges and potentially gain control over the host system.”
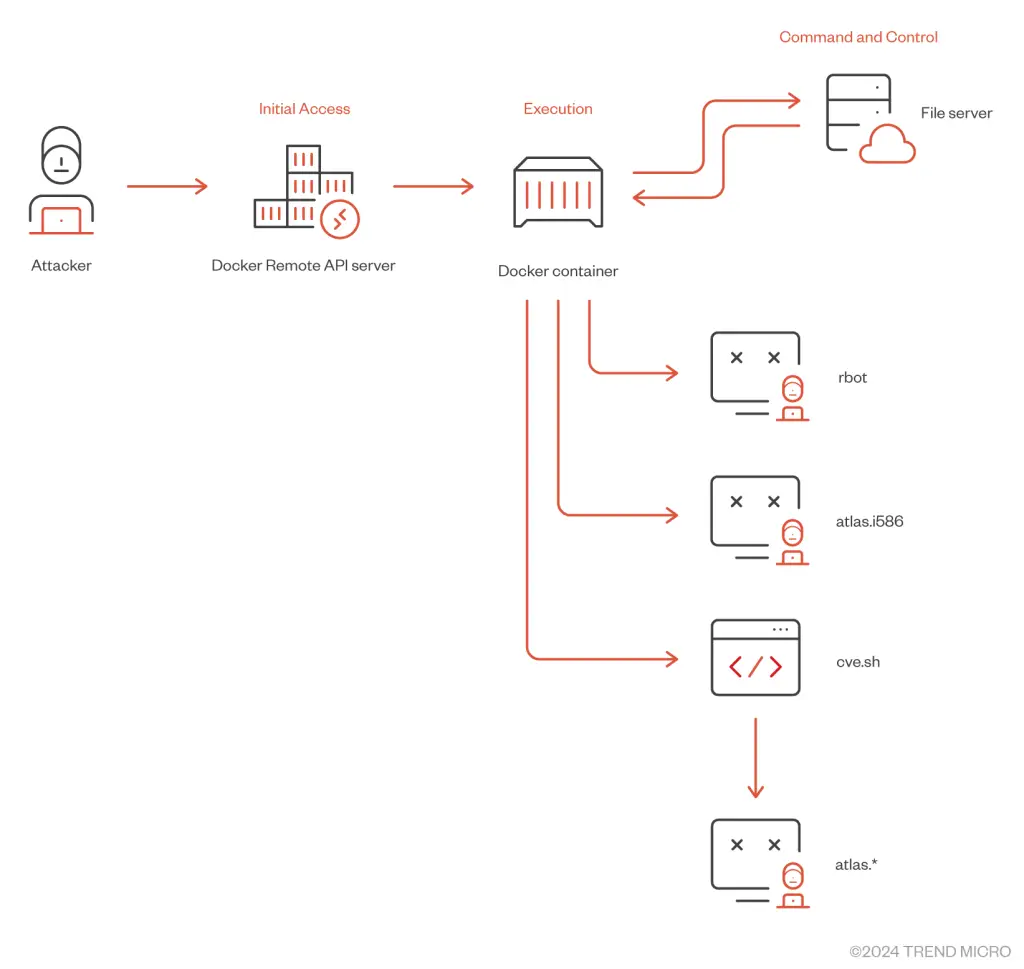
In the observed attacks, Gafgyt binaries were deployed with filenames like “rbot” and “atlas.i586,” both of which were hardcoded with command-and-control (C&C) server IP addresses and ports. These binaries enable attackers to launch distributed denial-of-service (DDoS) attacks using UDP, TCP, HTTP, and other protocols. Sunil Bharti, Senior Threat Researcher at Trend Micro notes, “In case of a failed attempt of container deployment, the attacker gives another try to deploy another variant of Gafgyt botnet binary via deployment of a shell script, which downloads and executes the botnet binaries for different system architectures.”
Once successfully deployed, the malware connects to its C&C server to receive instructions. It can then execute a variety of DDoS attacks, leveraging multiple protocols to overwhelm targets. Additionally, the malware includes functionality to identify the local IP address of the victim host by interacting with Google’s DNS server (8.8.8.8). This step ensures the attacker’s commands are executed within the correct network environment.
By attacking Docker Remote API servers, threat actors can exploit enterprise-level infrastructure, potentially leading to more severe consequences than traditional IoT device compromises. Bharti emphasized, “a shift in its behavior as it expands its targets beyond its usual scope.”
Trend Micro urges organizations to secure their Docker environments by disabling Remote API access if not required, implementing robust authentication, and monitoring network traffic for unusual activity. Regular patching and proper configuration management remain critical to mitigating such threats.
Related Posts:
- Gafgyt Botnet: Now Exploiting GPU Power in Cloud-Native Environments
- Sophisticated Linux Malware Campaign Targets Misconfigured Cloud Services
- Evolving Cryptojacking Campaign Targets Misconfigured Kubernetes Clusters
- Misconfigured Jenkins Servers Targeted in Cryptojacking Attacks