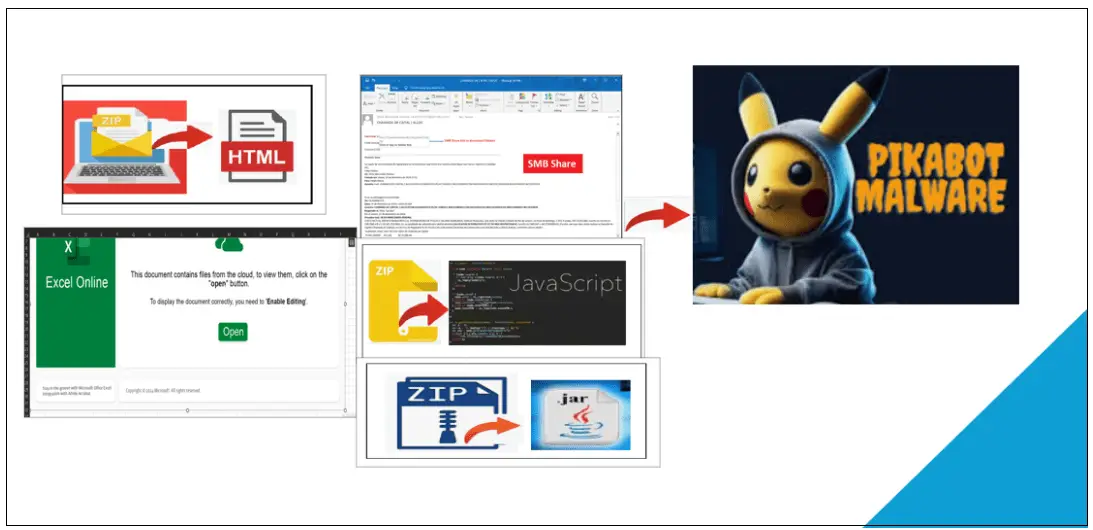
Distinctive Campaigns of Pikabot
A new report from McAfee Labs reveals a troubling evolution in the PikaBot malware campaign, showcasing an alarming range of infection vectors and techniques. Once limited in its distribution methods, PikaBot is now spreading rapidly through HTML, JavaScript, malicious Excel files, SMB shares, and JAR files – a level of sophistication that suggests well-coordinated and determined threat actors.
What is PikaBot?

PikaBot is a modular backdoor trojan designed to steal data and provide attackers with remote access to compromised systems. Its similarities to the Qakbot malware have raised concerns about connections to the prolific cybercrime gang.
Unusually Aggressive Campaign
McAfee Labs observed a dramatic surge in PikaBot attacks in February 2024, with threat actors employing multiple, often simultaneous methods of infection. This aggressiveness is atypical, suggesting the malware is being actively developed and weaponized for a significant campaign.
Key Findings from the Report:
Each campaign employed by Pikabot reveals a meticulous approach to ensure successful infiltration and execution:
- HTML Campaign: Utilizes a zip file containing an HTML file, which then downloads a text file to deploy the payload. The use of meta tag refreshes for redirection exemplifies the stealth and evasion tactics designed to bypass detection mechanisms.
- JavaScript Campaign: A .js file within a zip file initiates the download of the payload, demonstrating the malware’s ability to manipulate legitimate system utilities like curl.exe to further its malicious objectives.
- SMB Share Campaign: Exploits the MonikerLink bug, distributing malware through seemingly innocuous email threads that contain a link to an SMB share hosting the malicious payload.
- Excel Campaign: Tricks users with an Excel spreadsheet that prompts them to download a JavaScript file from an SMB share, which subsequently downloads and executes a malicious DLL file.
- JAR Campaign: A .jar file contained within a zip file drops a DLL payload, showcasing the malware’s ability to use Java archives as a means of distribution.
The Technical Mastery Behind Pikabot
Pikabot’s loader and core module exhibit a high level of sophistication, employing encryption and memory allocation techniques to decrypt and inject the core module into legitimate processes. The malware‘s ability to inject malicious content into ctfmon.exe and its use of hardcoded mutex values to prevent double infection reflect a well-engineered mechanism designed to evade detection and analysis.
Moreover, Pikabot’s network communication strategies, involving data exfiltration over HTTPS on non-traditional ports, highlight the malware’s advanced capabilities in maintaining stealth and ensuring the persistence of its operations.
Staying One Step Ahead
The PikaBot campaign highlights the rapidly changing cyberthreat landscape. Security teams and individuals must remain vigilant, update their defenses, and stay informed about the latest malware tactics to stay protected.