Kryptina Builder
In the ever-evolving landscape of cyber threats, ransomware has emerged as one of the most pervasive and damaging forms of malware. Among the latest additions to this malicious arsenal is Kryptina Ransomware, a Linux-focused ransomware-as-a-service (RaaS) that has taken a unique path from a paid underground tool to a freely accessible open-source project. Recently, SentinelOne delved into the development, technical intricacies, and implications of Kryptina RaaS as it poses a significant threat to Linux systems worldwide.
Kryptina RaaS made its debut in December 2023, offering cybercriminals a lightweight, customizable, and fast ransomware solution tailored specifically for Linux environments. Initially marketed with a pricing model ranging from $20 for a standalone build to $800 for a complete package, Kryptina quickly garnered attention in underground forums. However, the landscape shifted dramatically in February when the developer, known as ‘Corlys,’ unexpectedly released the entire source code on BreachForums, making it freely available to anyone with internet access.

While the motives behind this surprising move remain speculative, it’s evident that the release of Kryptina’s source code carries significant implications. Whether driven by a lack of buyers, a bid for recognition within the cybercrime community, or other undisclosed reasons, the aftermath of this release has the potential to reshape the ransomware landscape.
Kryptina employs a sophisticated encryption process leveraging OpenSSL’s libcrypto library and the AES256 algorithm in CBC mode. The ransomware utilizes parallel threads for efficient encryption, with keys and configuration data obfuscated via XOR and base64 encoding. Notably, Kryptina offers a feature for secure file deletion before encryption, further complicating data recovery efforts.
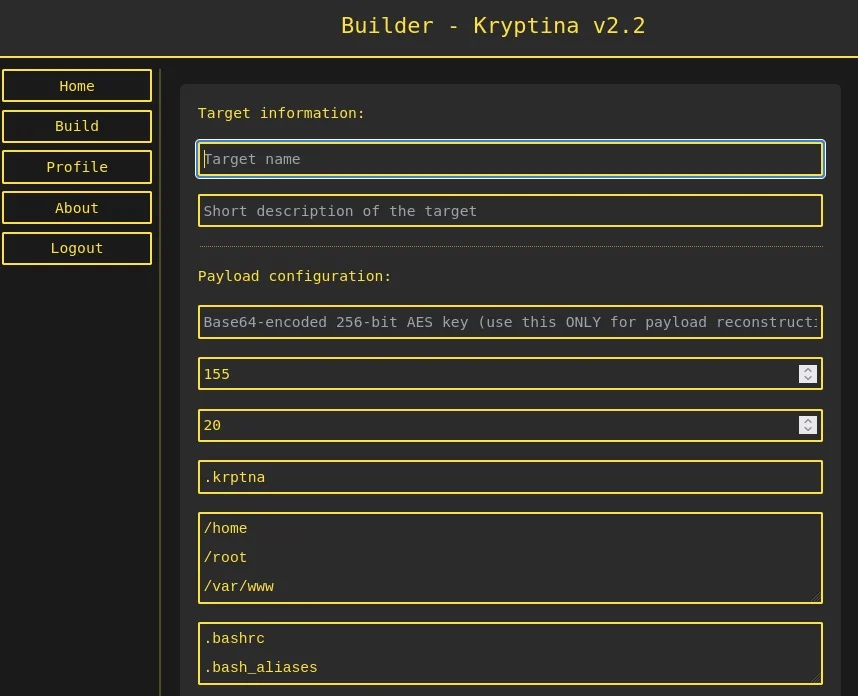
The web interface and builder components of Kryptina, built on Python scripts and powered by Flask, provide operators with granular control over campaign management and victim communication. The tool’s versatility and ease of use underscore its potential for widespread adoption and adaptation by cybercriminals.
As Kryptina’s source code circulates within the cybercrime ecosystem, the risk of variant proliferation and increased attack frequency looms large. Linux systems, powering critical infrastructure and cloud environments, are prime targets for ransomware attacks, necessitating robust defense measures and proactive security strategies.