Image: ThreatFabric
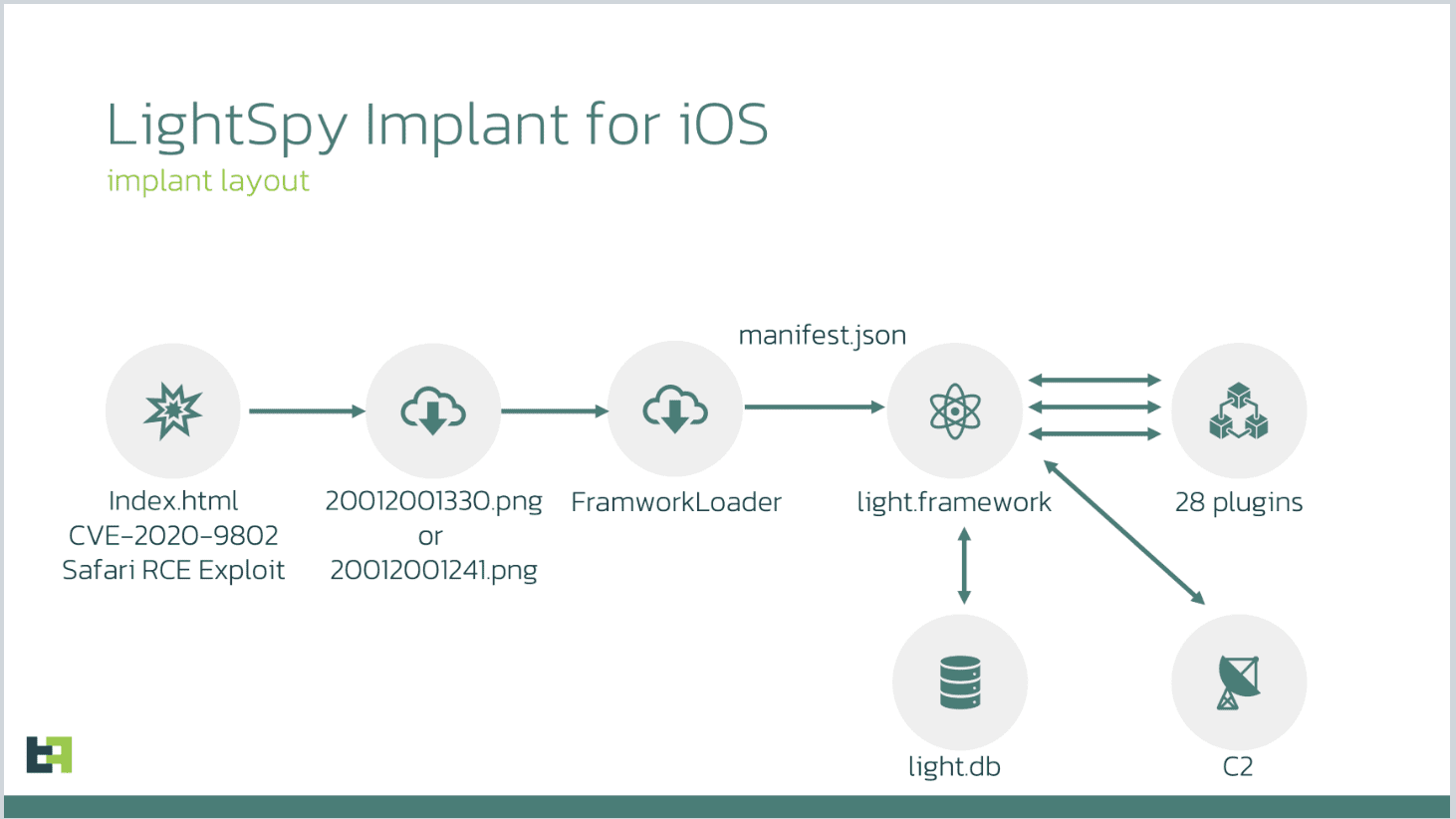
ThreatFabric released a report detailing advancements in the LightSpy implant, an iOS spyware first identified in 2020, which has evolved into a more complex and damaging tool. The latest findings reveal that the spyware, now version 7.9.0, has been upgraded to include 28 plugins, seven of which possess destructive capabilities. These updates underscore an intensified threat to iOS users as the spyware increasingly targets specific vulnerabilities and is becoming more potent in disrupting device stability.
One notable feature of LightSpy is its utilization of public exploits, including CVE-2020-9802 for initial access and CVE-2020-3837 for privilege escalation, enabling access to devices running iOS versions up to 13.3. While previous versions targeted a smaller set of iOS models, the latest update expands the range of supported devices, from iPhone 6 to iPhone X, using sophisticated, WebKit-based exploits. The malware also incorporates a series of plugins designed to disrupt functionality, from freezing devices to preventing them from booting.
The plugin count in LightSpy has grown dramatically, expanding from 12 to 28, with additions that facilitate both data exfiltration and destructive actions. ThreatFabric’s analysis emphasizes the increasing “destructive capabilities,” highlighting how the malware can delete contacts, SMS messages, and media files. According to ThreatFabric, “One particular campaign included plugins that could disrupt the operating system’s stability, with capabilities to freeze the device or even prevent it from booting up,” a testament to the increasing severity of LightSpy’s capabilities.
ThreatFabric’s findings indicate that LightSpy’s infection chain closely mirrors that of its macOS counterpart, leveraging identical WebKit-based vulnerabilities. The spyware’s core interacts with several C2 servers, maintaining consistent communication with the attackers. The report reveals that five active C2 servers, primarily based in Asia, help deploy the malware to iOS devices. Interestingly, ThreatFabric found JSON files indicating deployment dates, with some samples labeled as “DEMO,” suggesting the possibility of LightSpy being used for demonstrations rather than widespread distribution.
ThreatFabric suspects that the operators behind LightSpy are highly familiar with jailbreak techniques, integrating elements of public jailbreak tools to gain unauthorized access and persist on targeted devices. In particular, several plugins in LightSpy utilize jailbreak code and even bear the same certificates used in widely known jailbreak kits. While much of the malware’s infrastructure is hosted on IPs linked to China, ThreatFabric notes code similarities between the iOS and macOS versions of LightSpy, implying that both versions were likely created by the same development team.
Victims of LightSpy are often exposed through “watering hole” attacks, wherein users unknowingly visit infected sites, triggering the exploit chain. ThreatFabric’s investigation found evidence of exfiltrated data linked to 15 unique victims, eight of whom were using iOS devices. This malicious infrastructure’s focus on Chinese and Hong Kong devices, and the software’s embedded location recalibration function designed for Chinese coordinates, point toward a China-based threat actor.
LightSpy’s evolution serves as a reminder of the increasing risks tied to iOS vulnerabilities. ThreatFabric suggests that frequent reboots, which disrupt the persistence of non-rooted jailbreak malware, can serve as a simple but effective measure to limit data exposure on compromised devices. While this practice won’t entirely prevent reinfection, it can interrupt attackers’ attempts to maintain prolonged access.
Related Posts:
- LightSpy Malware Strikes macOS: Your Mac Could be the Target
- Espionage Campaign Returns: LightSpy Targets Southern Asia
- Biometric Bypass: Chameleon Banking Trojan Evolves, Android 13 Vulnerable
- SecuriDropper Unveiled: The Alarming Rise of Dropper-as-a-Service Cyberthreats