ThreatHunting
This is a Splunk application containing several dashboards and over 120 reports that will facilitate initial hunting indicators to investigate.
Note: ThreatHunting is not a magic bullet, it will require tuning and real investigative work to be truly effective in your environment. Try to become best friends with your system administrators. They will be able to explain a lot of the initially discovered indicators.
The app has the following structure
Trigger Overview

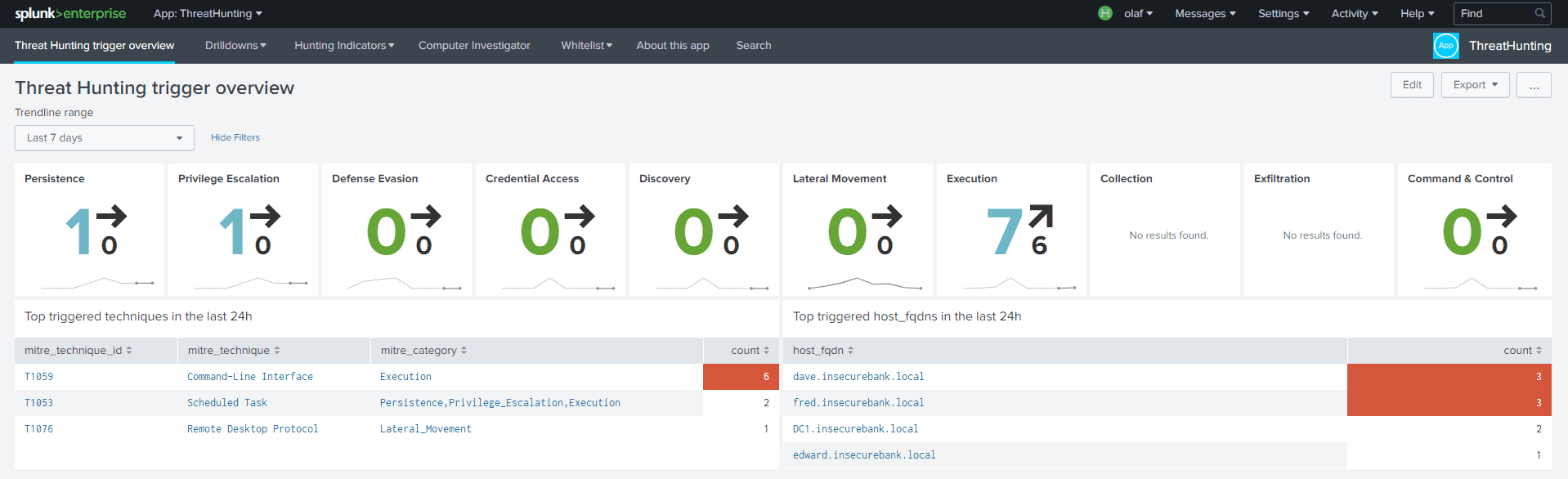
The overview page shows the following items;
The MITRE ATT&CK categories
Displaying the respectively detected indicators over the past 24 hours, the amount of the day before and a trendline of indicators over the past 7 days by default. You can change this by using the drop-down menu in the top left.
Below the categories, there are two tables
- One depicting the top triggered techniques in the last 24 hours
- One for the hosts with the most techniques triggered in the past 24 hours.
Drilldowns
- MITRE ATT&CK
- Computer Drilldown
- Network Connection Drilldown
- ParentProcess GUID Drilldown
- Process GUID Drilldown
Hunting Indicators
- Sysmon Events
- Lateral Movement Indicators
- PowerShell Events
- Newly observed hashes
Whitelists
- Process Create whitelist editor
- Network whitelist editor
- Files Access whitelist editor
- Process Access whitelist editor
- Registry whitelist editor
- Image Load whitelist editor
- Pipe Created whitelist editor
- WMI whitelist editor
Changelog v1.4
New Features
- – NEW REQUIREMENT: Link Analysis app >> LINK
- – Initial mapping of Windows 4768/9 events in props.conf
- – Pipe Drilldown dashboard
- – File create whitelist macro
- – File create Drilldown dashboard
- – Added Stacking tools section
- – Added Mitre ATT&CK stacking page
- – Added DNS stacking page with beaconing detection
- – Added User drilldown page
- – Added Macro drilldown dashboard
- – Added 24 new searches
Changes
- – Renamed pipe_created_whitelist macro to pipe_whitelist
- – Renamed pipe_created_whitelist csv to pipe_whitelist throughout the app
- – Replaced the force-directed visual by link analysis for network connection drilldown
- – Added a few fields to props.conf, including Sysmon DNS events
- – Extended T1218,T1216,T1081,T1075 searches
- – Added Credits pane
- – Rebuilt the whitelisting, searches are a LOT quicker now and take less resources
- – Added original_file_name to event_id 1 and 7
- – Top triggered techniques drilldown changed to technique_id
Bugfixes
- – T1197 had a typo
- – props fix for host_fqdn in non-xml ingest
- – whitelisting with long csv files caused bad behavior
- – File created events didn’t show
- – Initial Access events didn’t show on overview
- – T1044 was misrepresented
Download && Use
Copyright (c) 2018 Olaf Hartong