Deepfence ThreatMapper
Deepfence ThreatMapper helps you to monitor and secure your running applications, in Cloud, Kubernetes, Docker, and Fargate Serverless.
Your ‘Shift Left’ initiatives enable you to deliver secure applications; ThreatMapper picks up where ‘Shift Left’ ends:
- Discover Running Workloads: ThreatMapper scans your platforms and identifies pods, containers, applications, and infrastructure. Use ThreatMapper to discover the topology of your applications and attack surface.
- Discover Vulnerabilities: ThreatMapper obtains manifests of dependencies from running pods and containers, serverless apps, applications, and operating systems. ThreatMapper matches these against vulnerability feeds to identify vulnerable components.
- Rank Vulnerabilities by Risk-of-Exploit: ThreatMapper ranks discovered vulnerabilities against CVSS and other severity scores, exploit method, and proximity to attack surface, in order to identify which issues pose the greatest risk of exploit.
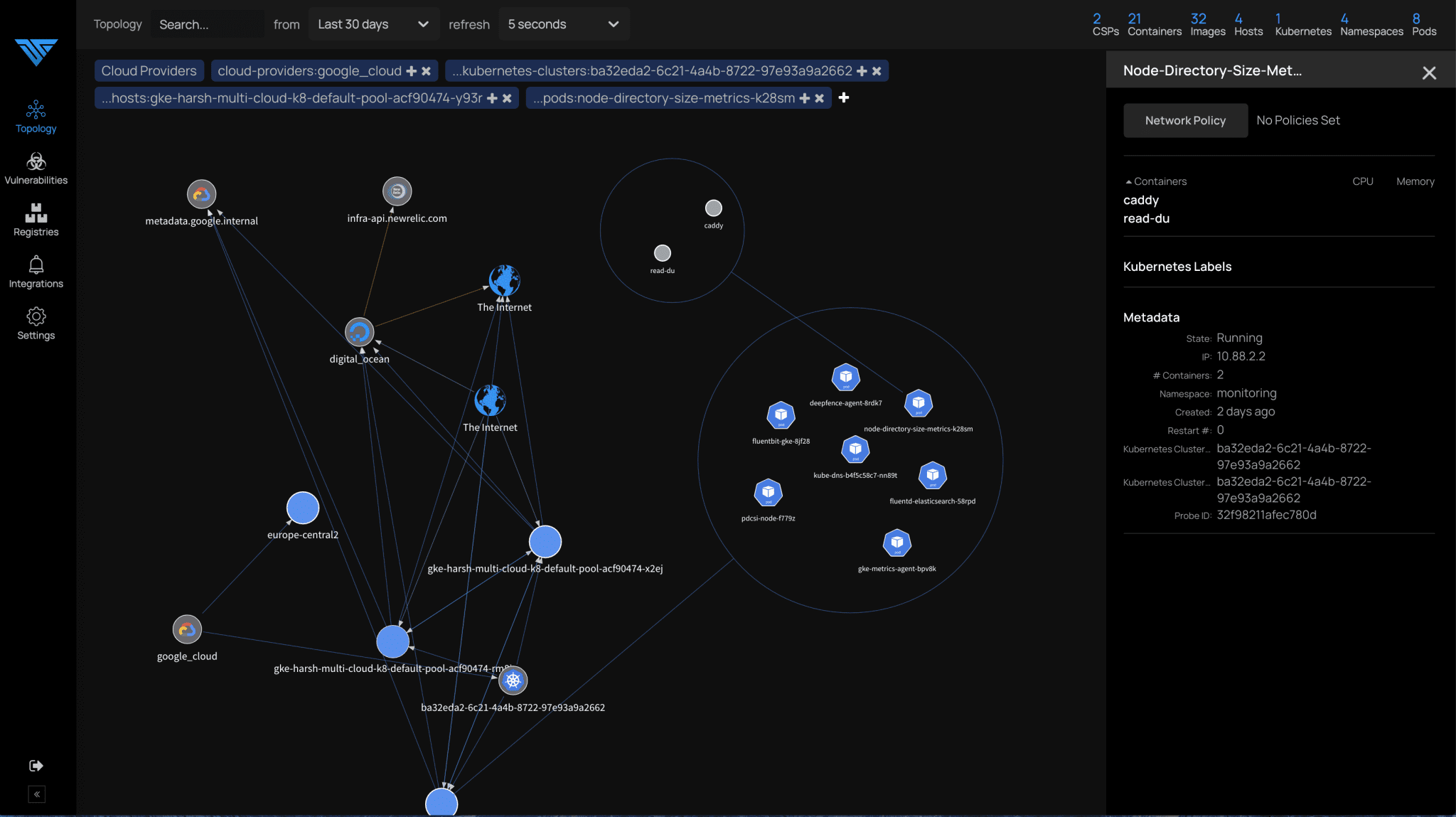
ThreatMapper discovers, annotates, and displays the topology of your applications across multiple cloud environments:
What is ThreatMapper?
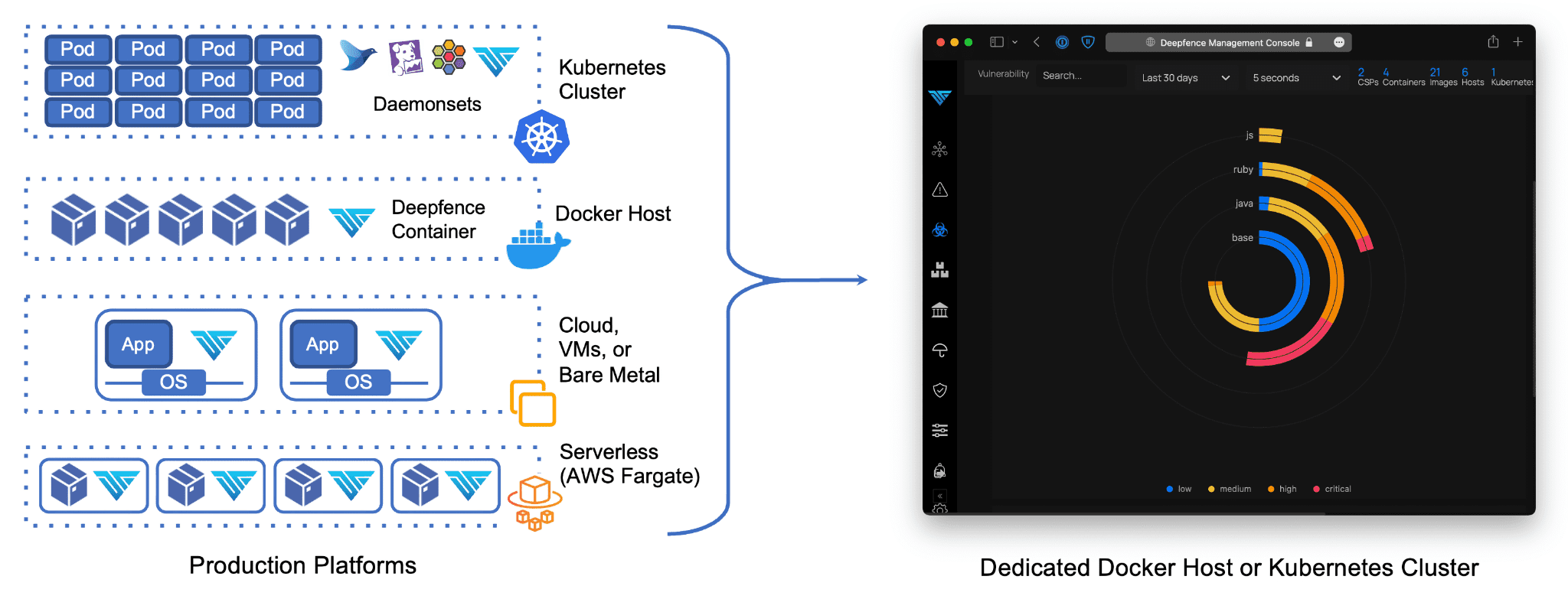
Deepfence ThreatMapper consists of two components – the Deepfence Management Console, and a series of Deepfence Sensors. The sensors should be deployed within your production platforms, and they forward manifest and telemetry securely to your dedicated console. The console calculates the topology of your applications, interrogates manifests to find vulnerabilities, and displays a ‘Threat Map’ for your applications.

The Deepfence Management Console
The Deepfence Management Console (“Console”) is a standalone application, implemented as a fleet of containers. It should be deployed on either a single docker host or (for larger deployments) a dedicated Kubernetes cluster. The console is self-contained and exposes an HTTPS interface for administration and API automation.
The console allows you to:
- Manage the users who can access the console.
- Visualize and drill down into Kubernetes clusters, virtual machines, containers, and images, running processes, and network connections in near real-time.
- Invoke vulnerability scans on running containers and applications and review the results, ranked by risk-of-exploit.
- Invoke vulnerability scans on infrastructure hosts, manually or automatically when they are added to a cluster.
- Scan container registries for vulnerabilities, to review workloads before they are deployed.
- Scan image builds during the CI/CD pipeline, supporting CircleCI, Jenkins, and GitLab.
- Configure integrations with external notification, SIEM, and ticketing systems, including Slack, PagerDuty, Jira, Splunk, ELK, Sumo Logic, and Amazon S3.
Deepfence ThreatMapper supports multiple production deployments simultaneously so that you can visualize and scan workloads across a large production estate.
Deepfence Sensors
Deepfence Sensors are deployed on your production platforms. They communicate securely with your Deepfence Management Console, taking instructions to perform scans, and forwarding telemetry data.
The sensors support a range of production platforms:
- Kubernetes: The sensors are deployed as a daemonset, similar to other kubernetes services.
- Docker: The sensor is deployed as a docker container on each docker host.
- Bare metal and VM-based platforms: Sensors are deployed as a Docker container on each operating system instance, using a Docker runtime. Both Windows and Linux instances are supported.
- AWS Fargate The sensor is deployed as a daemon service alongside each serverless instance.
Install & Use
Copyright (C) 2021 deepfence