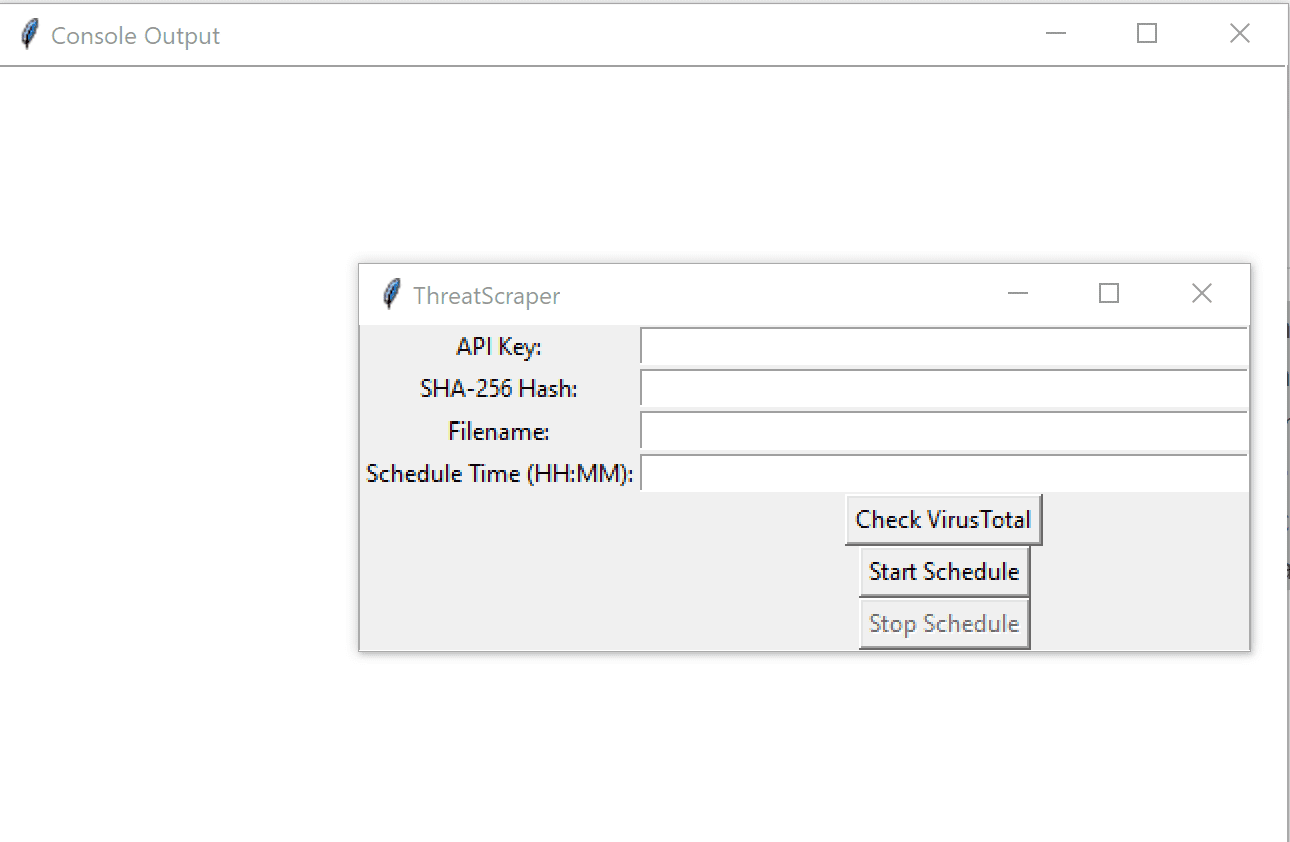
ThreatScraper
ThreatScraper is a Python-based tool designed to check virus information by using VirusTotal API. It offers functionalities such as scheduling the checking at specific times, showing and saving the graph of malware detection trends, as well as saving virus information to an Excel file. The Excel file “Toxicember.xlsx” is an example file that can be used to test the program, and also to show how a typical scheduled report will be displayed.
This version of ThreatScraper has been enhanced to use poentry for dependency management and to use black and isort for code formatting.

ThreatScraper is being developed in Python to interface with VirusTotal’s v2 API to search their database for a file hash (SHA256/SHA1/MD5), and if a match is found the report data is sent back to the requestor. The information sent back contains 70 different Anti Virus products, with their individual findings on the file (malicious or not), the version and date of the Anti Virus definitions, and what individual naming convention the Anti Virus service uses for the specific file requested (trojan, worm, keylogger, etc). The information is stored in an Excel file and can be scheduled to run multiple times during the day. The program is very much in development, however, the ThreatScraper.py script is a working prototype.
-
Modify the script with your VirusTotal API key.
-
Enter the file hash that you would like to search for.
-
Provide the script with the Excel file location to save the report.
-
Modify the scheduled times at the end, the script will execute during those times.
-
Save and close. In a command prompt, run the script with “python ThreatScraper.py”.
Install & Use
Copyright (c) 2023 amorath